Sponsored by Palo Alto Networks
Sponsored by Elastic
Transforming Defense Intelligence: A Global Data Mesh Approach
Sponsored by JFrog
Cloud Migration 101
Sponsored by Exabeam
The Ultimate Guide to Cloud-Native SIEM: Transition SIEM to the Cloud
Sponsored by Palo Alto Networks
Attack Surface Management for Dummies®
Sponsored by Dimension Data and SAP
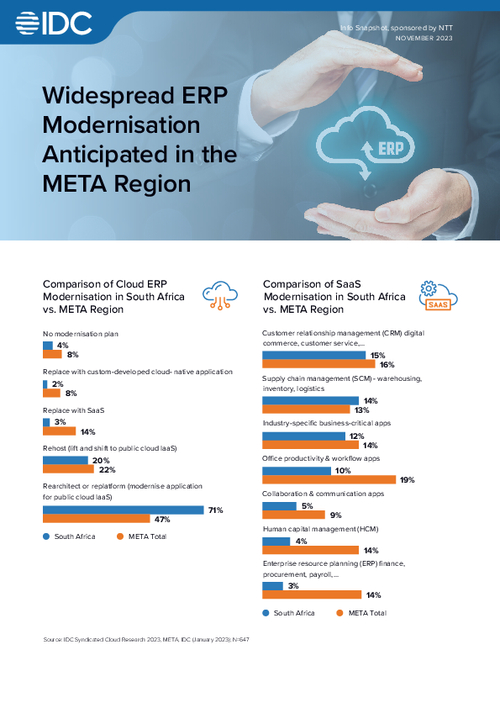
Widespread ERP Modernisation Anticipated in the META Region
Sponsored by Dimension Data and SAP
The Need to Modernise with Cloud ERP Has Never Been Greater
Sponsored by Wiz
Survival Guide For the Next Log4Shell
Sponsored by Wiz
Frost Radar: Cloud-Native Application Protection Platforms, 2023
Sponsored by Claroty & Rockwell Automation
What's Driving Industrial Cybersecurity into the Cloud?
Sponsored by Wiz
CSPM Buyers Guide
Sponsored by Wiz
Wiz for CSPM
Sponsored by Wiz