Sponsored by Palo Alto Networks
Sponsored by Palo Alto Networks
Bringing Zero Trust Security to the Public Cloud
Sponsored by Sevco Security
Cyber Hygiene and Asset Management Perception vs. Reality
Sponsored by Binalyze
13 Essential Criteria to Consider For Cyber Resilience in IR & SoC Teams
Sponsored by Palo Alto Networks
Challenge vs. Solution: The Next Era of Virtual Network Innovation
Sponsored by Palo Alto Networks
How to Plan for Tomorrow’s SOC, Today
Sponsored by CrowdStrike
The Buyer’s Guide to Complete Cloud Security
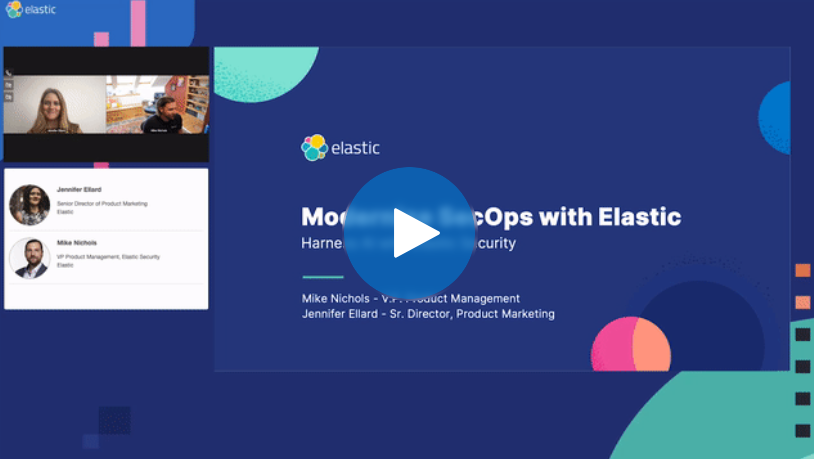
Sponsored by Elastic
Modernize SecOps: Harness AI with Elastic Security
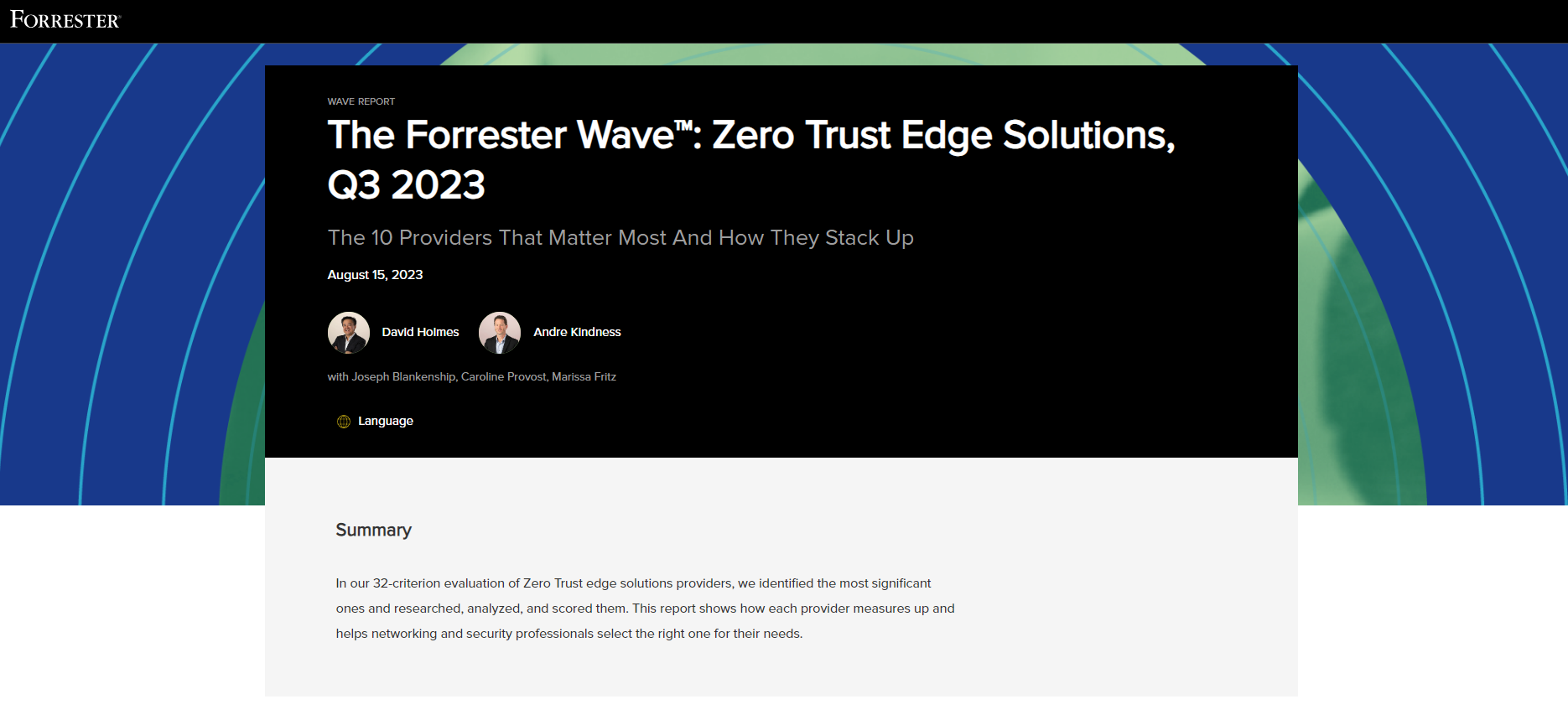
Sponsored by Palo Alto Networks
The Forrester Wave™: Zero Trust Edge Solutions, Q3 2023
Sponsored by Palo Alto Networks
The Total Economic Impact™ Of Palo Alto Networks Prisma SASE
Sponsored by Palo Alto Networks
Hackers Are Coming For Your Cloud-Based Applications
Sponsored by Palo Alto Networks
A CISO’s Guide to Attack Surface Management
Sponsored by Palo Alto Networks
Five Key Challenges in Private Cloud Security
Sponsored by Palo Alto Networks