Sponsored by Horizon3.ai
Sponsored by BeyondTrust
Advancing Zero Trust with Privileged Access Management (PAM)
Sponsored by Cisco
Customer Case Study: Cosentino
Sponsored by SailPoint
The state of identity security 2023: A spotlight on financial services
Sponsored by SailPoint
Securing digital identities: How to protect banks and financial firms
Sponsored by Radiant Logic
Analyst Survey | Identity Data Management: Roadblock or Business Enabler?
Sponsored by Bishop Fox
Getting Red Teaming Right: A How-to Guide
Sponsored by Radiant Logic
Customer Success Story | Large Healthcare Organization Achieves Future-State IAM
Sponsored by Radiant Logic
Forrester Report | The Total Economic Impact™ of Radiant Logic
Sponsored by 1Password
The Total Economic Impact™ of 1Password Business
Sponsored by 1Password
The Guide to Creating a Culture of Security
Sponsored by 1Password
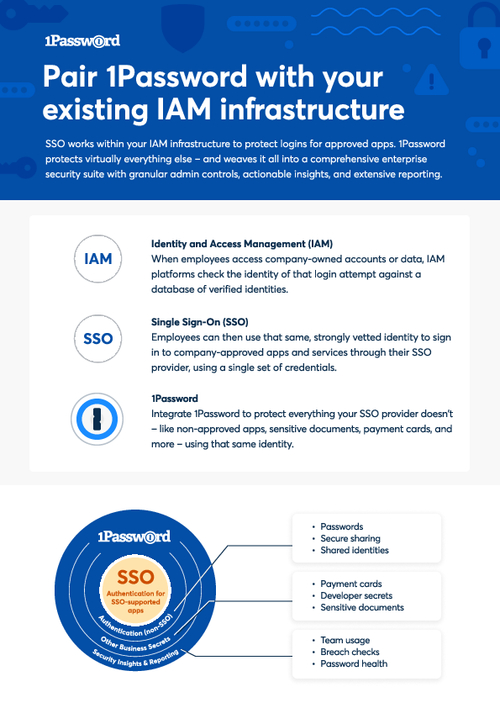
Pair 1Password with Your Existing IAM Infrastructure
Sponsored by Cisco