Sponsored by ServiceNow
Enterprise Strategy Group: Security Hygiene And Posture Management
Sponsored by Proofpoint
Ransomware: How to Win the Battle
Sponsored by ServiceNow
Enterprise Strategy Group: A Prudent Approach To Ransomware Defense
Sponsored by ServiceNow
Using ServiceNow SOAR To Operationalize MITRE ATT&CK
Sponsored by ServiceNow
5 Stages of Security Automation Maturity: How Do You Compare?
Sponsored by ServiceNow
Cybercriminals Are Resilient. How About You?
Sponsored by ServiceNow
Create Continuity Plans That Minimize Disruptions And Protect Critical Assets
Sponsored by ServiceNow
Data Privacy Report: Data Privacy Priorities, 2021
Sponsored by ServiceNow
Risk and Security Workflows Book of Knowledge
Sponsored by ServiceNow
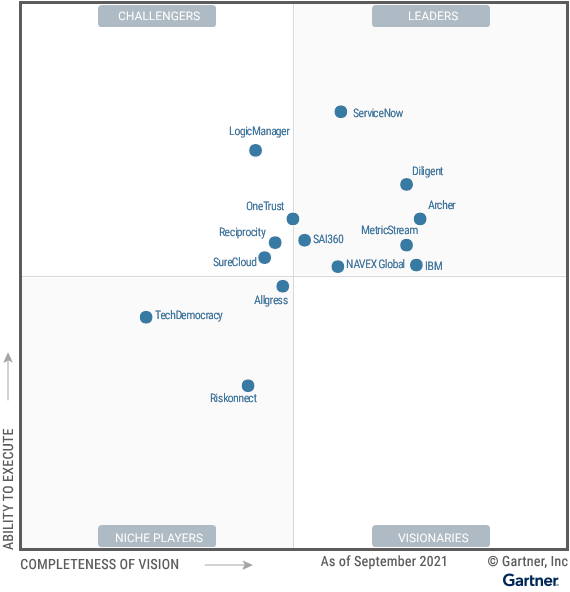
Gartner Magic Quadrant for IT Vendor Risk Management Tools
Sponsored by ServiceNow
Gartner Magic Quadrant for IT Risk Management
Sponsored by ServiceNow
5 Ways To Reduce Risk With Continuous Monitoring
Sponsored by ServiceNow
Transforming Risk - Why Digital Transformation Depends on Integrated Risk Management
Sponsored by Proofpoint