Sponsored by Menlo Security
Sponsored by Menlo Security
Reimagining Online Security for Federal Agencies
Sponsored by Menlo Security
Stop Malware for Good: A New Game Plan for Securing Federal Agencies
Sponsored by Menlo Security
Ransomware: State & Local Governments Fight Back
Sponsored by Intrinsic ID
Protecting the IoT with Invisible Keys
Sponsored by Intrinsic ID
IoT Device Security with Cryptographic Keys
Sponsored by Whitesource
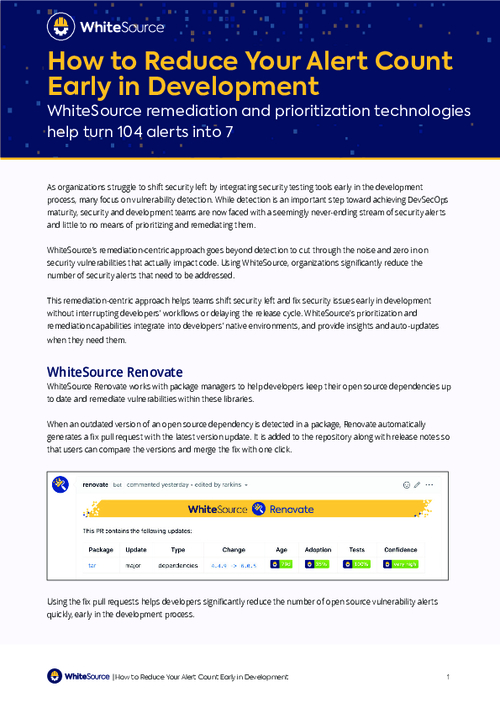
How to Reduce Your Alert Count In Early Development
Sponsored by Palo Alto Networks
Cybersecurity Reference Blueprint for Manufacturing
Sponsored by Palo Alto Networks
Secure Access Service Edge for Manufacturing
Sponsored by Palo Alto Networks
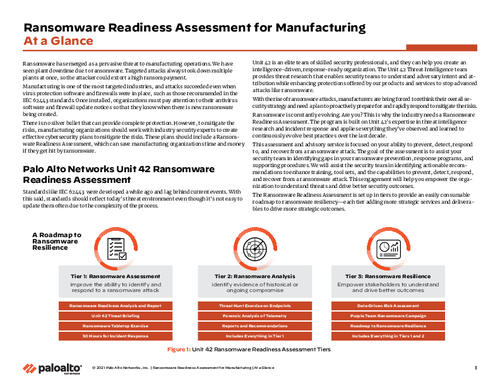
Ransomware Readiness Assessment for Manufacturing At a Glance
Sponsored by Cyberark
Endpoint Least Privilege: A Foundational Security Control
Sponsored by LogMeIn
LastPass Success Story: Yelp
Sponsored by LogMeIn
Finding A Password Management Solution For Your Business
Sponsored by LogMeIn
10 Ways to Increase Security and Productivity During Remote Work
Sponsored by LogMeIn