Sponsored by Bomgar
How to Rethink Third-Party Access
Sponsored by SolarWinds
The 12 Core Requirements of Achieving MSSP Status
Sponsored by SolarWinds
Cybersecurity Blueprint: A Four-Part Model for Providing Comprehensive Layered Security
Sponsored by Red Canary
PowerShell Deep Dive: A United Threat Research Report
Sponsored by Red Canary
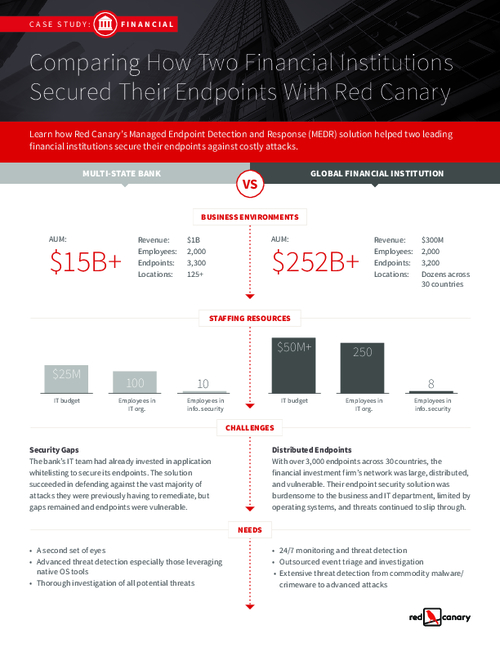
Case Study: How Two Financial Institutions Secured Their Endpoints
Sponsored by Red Canary
Case Study: How an Investment Firm Uses Multiple MSSPs
Sponsored by Windstream
Deploy SD-WAN to Achieve Consistent Security
Sponsored by Windstream
How to be an Innovative Security Leader
Sponsored by Windstream
Are you using SD-WAN To Optimize Your Security Controls?
Sponsored by Windstream
TCO Analysis UCaaS vs On-Premises
Sponsored by Windstream
Case Study: Propelling Growth & Connectivity with UCaaS
Sponsored by Windstream
The UCaaS Era: Where Best-in-Class Takes Place in the Collaborative Cloud
Sponsored by Windstream