Sponsored by Terbium Labs
A Holistic Approach to Understanding and Monitoring Fraud on the Dark Web
Sponsored by Terbium Labs
The Clear Web is Darker Than You May Think: Fraud Prevails Regardless
Sponsored by Terbium Labs
A Scientific Approach to Analyzing Dark Web Content
Sponsored by Terbium Labs
Mid-sized Financial Institutions Struggle to Fight Fraud: A Case Study
Sponsored by Terbium Labs
3-Step Process to Defeat Stolen Data Cybercriminals
Sponsored by BitSight
The Do's and Don'ts of Reporting to the Board
Sponsored by Sift Science
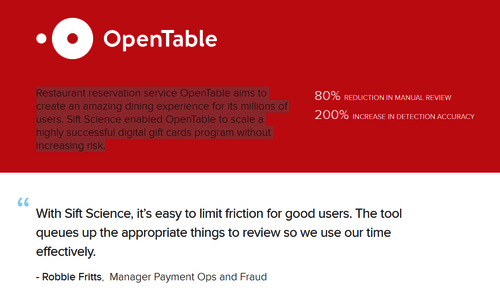
Case Study: Enhancing User Experience While Mitigating Risk
Sponsored by Digital Shadows
Top Cybercrime Threats to Financial Institutions in 2018
Sponsored by Digital Shadows
An Inside Look at Online Carding Courses for Cybercriminals
Sponsored by Digital Shadows
Bank Employee Offering Insider Information
Sponsored by Harland Clarke
Open Banking & Other Risk Challenges For Banks
Sponsored by Lastline