Sponsored by Fortra
Sponsored by Fortra
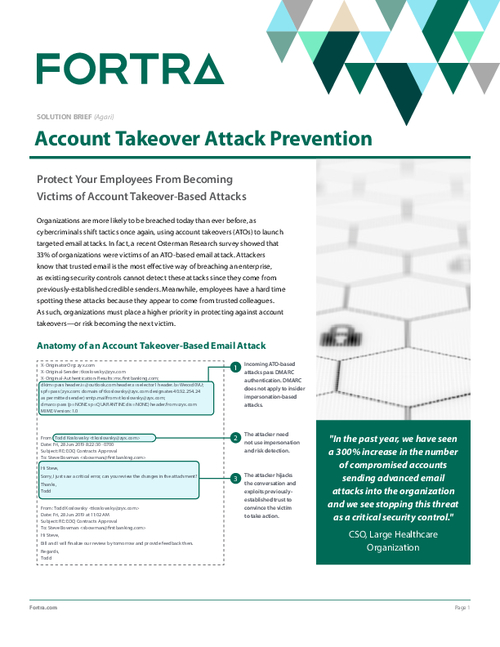
ATO Attacks: How to Prevent Account Takeover-Based Email Attacks
Sponsored by Abnormal Security
CISO Guide to Account Takeover
Sponsored by Abnormal Security
Abnormal Intelligence: New Threat Intel Site Launched
Sponsored by NICE Actimize
2023 FRAML Outlook: Trends, Scams & Fighting Back
Sponsored by Deepwatch
How to Manage Growing Threats, Tighter Budgets (eBook)
Sponsored by Abnormal Security
H2 2022: Threat Actors Impersonate 265 Brands in Credential Phishing Attacks
Sponsored by Expel
Expel Quarterly Threat Report - Q2 2022
Sponsored by LexisNexis Risk Solutions
Balancing Risk & Reward in APAC: The New Mobile Battlefield
Sponsored by Abnormal Security
From CEO Fraud to Vendor Fraud: The Shift to Financial Supply Chain Compromise
Sponsored by Signifyd
The Commerce Protection Buyer’s Guide
Sponsored by TeleSign
eBook I Beyond Authentication: Identifying the Person behind the Number
Sponsored by TeleSign
eBook I Building Trust at Every Stage of the Customer Journey
Sponsored by TeleSign
Stopping Fake Users at the Door
Sponsored by TeleSign