Cybercrime , Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime
Steele Dossier Case: Expert Traces Spear-Phishing of DNC
XBT/Webzilla Hosting Infrastructure Used for Nation-State Hacking, Expert Finds
Expert analysis submitted as part of a failed defamation lawsuit over the Steele dossier says a web hosting firm's infrastructure was used to attack U.S. Democratic Party officials.
See Also: Bank on Seeing More Targeted Attacks on Financial Services
Anthony J. Ferrante, global head of cybersecurity for FTI Consulting and formerly head of cyber incident response for the White House, said in a court report that infrastructure hosted by XBT Holding and its Webzilla subsidiary was a cybercrime and cyber espionage nexus and that the company appears to have done little if anything to stop it. The report was unsealed on Thursday.
He says attackers used XBT's infrastructure as part of 2016 U.S. election hacking efforts, including against the Democratic National Party.
"Technical evidence suggests that Russian cyber espionage groups used XBT infrastructure to support malicious spear-phishing campaigns against the Democratic Party leadership, which resulted in the theft of emails from a senior member of the Hillary Clinton presidential campaign," Ferrante wrote.
XBT did not immediately respond to a request for comment.
Ferrante's expert report was submitted to the court as part of the proceedings of a lawsuit that began in February 2017, one month after Buzzfeed published a collection of 16 private intelligence memos, spanning 35 pages, which were written by Christopher Steele, a former agent for Britain's Secret Intelligence Service, better known as MI6. Steele was commissioned to investigate Donald Trump's business dealings in Russia by U.S. private investigation firm Fusion GPS, on behalf of its Republican and later Democratic clients.
To date, nothing in the public record substantiates the suggestion in the dossier that the Trump campaign may have been paying foreign hackers or substantiates any of its claims about the president.
Since Buzzfeed published the memos, Trump has continued to strongly dismiss their claims.

In response to the memos being published, Russian technology executive and venture capitalist Aleksej Gubarev, who's based in Cyprus, filed a libel lawsuit against Buzzfeed and Ben Smith, its editor-in-chief.
Gubarev is chairman and CEO of Luxembourg-based XBT Holding S.A. and a group of web-hosting businesses, based in Fort Lauderdale, Florida, that carry the Webzilla name and specialize in internet hosting and web development. He and his businesses were named in the dossier as having allegedly been part of attacks that targeted the leadership of the Democratic National Party.
U.S. intelligence agencies say Russia was behind the spear-phishing attacks, which included stealing emails from Clinton's campaign chairman, John Podesta, and leaking them via WikiLeaks (see: Nation-State Spear Phishing Attacks Remain Alive and Well).
In the libel lawsuit - "Aleksej Gubarev, XBT Holding S.A. and Webzilla, Inc. v. BuzzFeed, Inc. and Ben Smith" - Gubarev denies that he or his firm had anything to do with the attacks.
A judge dismissed the lawsuit in December 2018.
Investigator Probes Possible Links
In response to the defamation lawsuit, Buzzfeed's defense counsel, Davis Wright Tremaine LLP, commissioned global consultancy FTI to investigate whether there was any connection between XBT and Russian attacks against the U.S.
Ferrante, who led the investigation, was formerly a member of the FBI's Cyber Action Team, after which he served as chief of staff of the FBI's cyber division and then the director for cyber incident response at the U.S. National Security Council at the White House.
As newspaper chain McClatchy has reported, Ferrante's expert report found that XBT's infrastructure was used to attack the DNC, as well as for numerous other cyberattacks. In addition, he said XBT appeared to lack any meaningful controls for monitoring or blocking cybercrime or cyber espionage conducted via its network.
"FTI investigated the veracity of the Dossier's statements concerning the plaintiffs, as well as the same statements as applied to other subsidiaries of XBT," Ferrante writes. "FTI also investigated information pertaining to the reputation, if any, of the plaintiffs, as well as other subsidiaries of XBT, for involvement in malicious cyber activity."
It's not clear if XBT's leadership knew about or sanctioned such attacks. XBT told McClatchy that "just because something occurred in the past does not mean it is related to current events."
But Ferrante found that XBT was doing little, if anything, to stop such activity, including attacks tied to Fancy Bear, aka APT28, which is believed to be associated with Russia's GRU military intelligence agency, and Cozy Bear, aka APT29, which is believed to be associated with the FSB (see: Report: Guccifer 2.0 Unmasked at Last).
"XBT and its affiliated web hosting companies have provided gateways to the internet for cybercriminals and Russian state sponsored actors to launch and control large scale malware campaigns over the past decade," Ferrante wrote.
"Data provided by Bitly indicates that an XBT affiliate owned infrastructure that was used to support the malicious spear-phishing attack of Democratic Party leadership in 2016 which resulted in the theft and subsequent publication of highly sensitive information related to the Hillary Clinton presidential campaign," he said. "Additionally, evidence suggests that Cozy Bear and Fancy Bear, the Russian government affiliated APT groups responsible for hacking the Democratic Party leadership, have used XBT infrastructure to support other malicious activity."
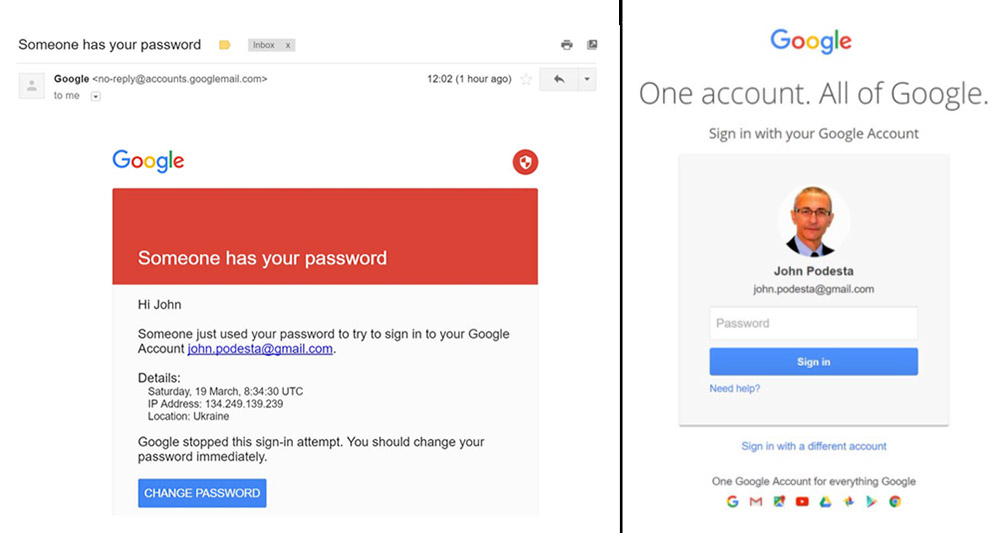
XBT Infrastructure Used by Attackers
Ferrante also referenced reports from private security firms that traced numerous attacks - including state-sponsored campaigns - to XBT infrastructure.
"Those reports suggest XBT infrastructure has been used to propagate malware, to attack the Ukrainian power grid, to engage in spear-phishing attacks, to deliver ransomware, to launch online advertising click-fraud theft schemes and to host botnets," he said. "Additionally, XBT has a public reputation for hosting malicious cyber activity," referencing reports that its infrastructure was often found being used as part of command-and-control operations for botnets, including "hosts of high levels of Zeus botnet activity," as well as for digital advertising fraud, including a scheme known as Methbot.
But Ferrante said XBT does not appear to have defenses in place to counter these types of activities or pay attention to third-party abuse reports. For example, Root S.A., an XBT-owned subsidiary that provides web hosting, domain names and dedicated servers, "does not appear to have any enterprise infrastructure monitoring in place to identify the use of their infrastructure to launch a cyberattack," he said. "Additionally, no formal procedures appear to be in place to monitor abuse alerts."
As part of a deposition in the libel case he launched against Buzzfeed, XBT's Gubarev said that his company had received $200,000 per month from Alexander Zhukov to rent Dallas-based server hosting until Webzilla shut down the hosting in December 2016. Zhukov was one of a number of individuals indicted by the Justice Department for allegedly running the Methbot fake advertising network. The scheme was the focus of a 13-count indictment unsealed last November.
During the deposition, McClatchy reports that when Miami attorney Roy Black, who was defending Buzzfeed, asked Gubarev why his firm hadn't notified the FBI about Zhukov's suspicious activities, the CEO responded: "It's not my duty. They have to investigate."
'Botnets and Porn Traffic'
The final page of the Steele dossier includes a private intelligence memo dated Dec. 13, 2016, which says a source told Steele that President Donald Trump's lawyer, Michael Cohen, had traveled to Prague to meet with Kremlin representatives operating under cover as members of the Russian NGO Rossotrudnichestvo. These members of Russia's state security service, known as the FSB, were allegedly running a campaign that used XBT/Webzilla infrastructure as part of hack attacks.
From the dossier, as cited in the libel lawsuit:
[redacted] reported that over the period March-September 2016 a company called XBT/Webzilla and its affiliates had been using botnets and porn traffic to transmit viruses, plant bugs, steal data and conduct "altering operations" against the Democratic Party leadership. Entities linked to one Alexei GUBAROV [sic] were involved and he and another hacking expert, both recruited under duress by the FSB, Seva KAPSUGOVICH, were significant players in this operation. In Prague, COHEN agreed contingency plans for various scenarios to protect the operations, but in particular what was to be done in the event that Hillary CLINTON won the presidency. It was important in this event that all cash payments owed were made quickly and discreetly and that cyber and other operators were stood down / able to go effectively to ground to cover their traces.
Gubarev's lawsuit disputed every claim involving him or his companies. For example, the lawsuit says that "neither XBT nor Webzilla nor any of their affiliates" had been using botnets or porn traffic to launch malware attacks.
In addition, "Mr. Gubarev was not 'recruited under duress by the FSB' (to be clear, he was not recruited at all - whether under duress or otherwise), nor was he recruited for such activities by anyone else at any other time or in any other circumstances whatsoever," the lawsuit states. "Additionally, he has no knowledge of, has never met and has never spoken to a person known as Seva Kapsugovich."
Dossier: Washington's 'Worst-Kept Secret'
The private intelligence memos arose from Fusion having hired Steele, who runs London-based private investigations firm Orbis, to provide research for its clients on Trump.
Reportedly alarmed by what his sources were telling him, Steele continued to investigate Trump, ultimately sharing his findings with the FBI and U.K. intelligence agencies, among others.
Details from the dossier, if not always the contents, quickly became "the worst-kept secret in politics and the media," Guardian reporter Luke Harding recounts in his book "Collusion."
In January 2017, citing concerns that decisions and actions had already been made in the U.S. political sphere as a result of the dossier, Buzzfeed opted to publish a copy of the memos, redacting some information.
Allegations Not Proven
Steele reported finding numerous alleged links between Russians and the Trump campaign team.
None of the allegations against the president contained in the raw intelligence reports, however, have been proven. Likewise, none of the allegations against Cohen, Manafort and Page contained in the dossier have been proven, although the men have also been subject to separate FBI investigations. Manafort has since been found guilty of other crimes, including tax fraud and bank fraud, and received a 90-month jail sentence, while Cohen pleaded guilty to a number of crimes, receiving a three-year sentence last December (see: Collusion Investigation: 37 Indictments and Counting).
Summertime in Prague
In response to the libel case, Buzzfeed told the court that it had sent reporters to Prague to try to prove or disprove the allegation about Cohen, but said it was unable to do so.
Cohen continues to deny that he traveled to Prague.
I hear #Prague #CzechRepublic is beautiful in the summertime. I wouldn't know as I have never been. #Mueller knows everything!
— Michael Cohen (@MichaelCohen212) December 27, 2018






















