Fraud Management & Cybercrime , Fraud Risk Management , Governance & Risk Management
Rushed to Market: DearCry Ransomware Targeting Exchange Bug
'Unsophisticated' Code Has Scant Resemblance to WannaCry Namesake, Researchers Say
Fresh ransomware targeting as-yet-unpatched on-premises Exchange servers appears to have been rushed to market, with attackers seeking to capitalize on new opportunities before the competition stepped in, security firm Sophos reports.
See Also: Securing Your Workforce with Datto RMM: Automating Patching, Hardening, and Backups
Sophos has published a teardown of the new DearCry ransomware, which it describes as being "unsophisticated" and apparently "created by a beginner." The ransomware was first spotted in the wild on March 9.
DearCry targets a critical proxy-logon flaw in Microsoft Exchange email servers, which was one of four zero-day flaws Microsoft patched via software updates issued on March 2, when it warned that the flaws were already being exploited in the wild.
Since then, organizations have been scrambling to get patches applied, and incident response teams have been reviewing all systems for signs of long-term compromise. Security firm Volexity recently warned that the flaws appear to have been first exploited beginning on Jan. 6.
We have detected and are now blocking a new family of ransomware being used after an initial compromise of unpatched on-premises Exchange Servers. Microsoft protects against this threat known as Ransom:Win32/DoejoCrypt.A, and also as DearCry.
— Microsoft Security Intelligence (@MsftSecIntel) March 12, 2021
On the ransomware front at least, here's some welcome news for defenders: Like its WannaCry worm namesake - and it's not clear there's any connection with that malicious code - DearCry's coding to date has been relatively shoddy.
No doubt seeking to maximize their ability to exploit organizations still running unpatched Exchange servers, whoever's behind DearCry appears to have rushed their effort to hit as many organizations as possible before they patched the proxy-logon Exchange flaw, aka CVE-2021-26855.
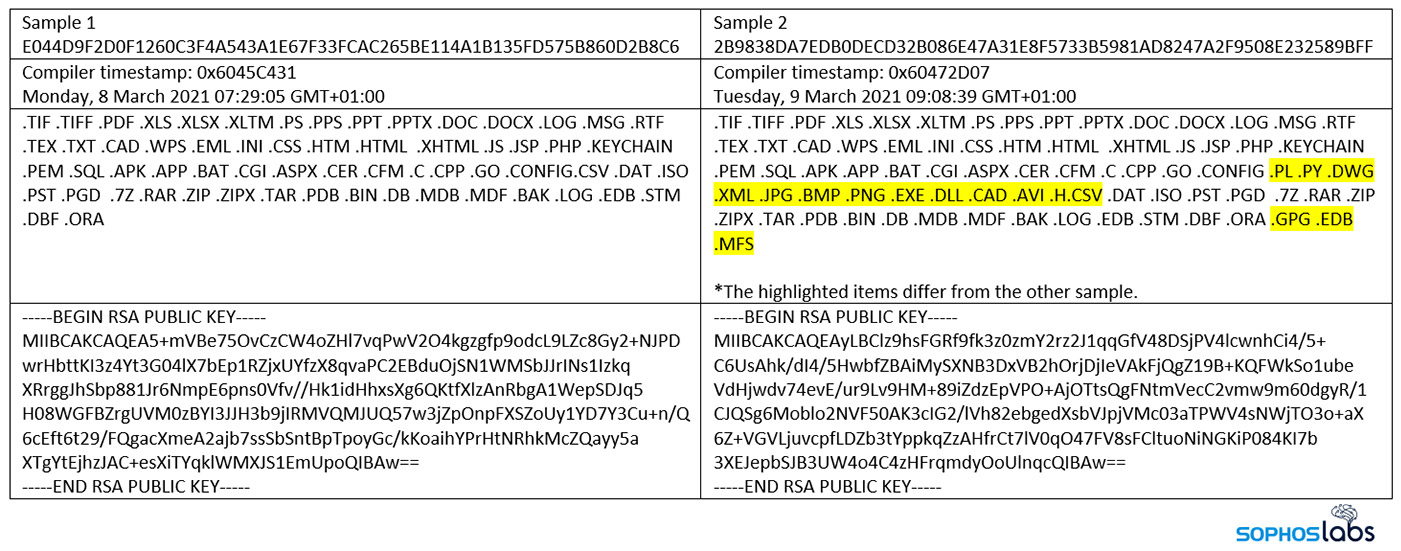
From a software engineering perspective, the rush has led to predictable results - as in, "unusual characteristics," says Mark Loman, director of the engineering technology office at Sophos. "The ransomware actor has been creating new binaries for new victims," he says, meaning the hackers have been updating the attack code at an unusually fast rate, potentially to fix bugs or add functionality as they go.
#DearCry ransomware is now going after a significant amount of different file types and has a different encryption key, indicating the attacker is creating the ransomware per target. pic.twitter.com/NUiGIlwAnq
— Mark Loman @ (@markloman) March 12, 2021
"The list of file types targeted has evolved from victim to victim, too," he says. "Our analysis further shows that the code does not come with the kind of anti-detection features you would normally expect with ransomware, like packing or obfuscation. These and other signs suggest that DearCry may be a prototype, possibly rushed into use to seize the opportunity presented by the Microsoft Exchange Server vulnerabilities, or created by less experienced developers."
Unusual 'Copy' Approach to File Encryption
Many human-operated or more advanced ransomware operations today - including Ryuk, Sodinokibi - aka REvil, BitPaymer, now-defunct Maze and Clop - use in-place encryption, Sophos says. This means the ransomware forcibly encrypts files, after which the attackers drop a ransom note.
But DearCry uses a more primitive, less effective and relatively unusual hybrid approach, Loman says. The malware first generates an encrypted copy of a targeted file and then attempts to overwrite the original with the encrypted copy.
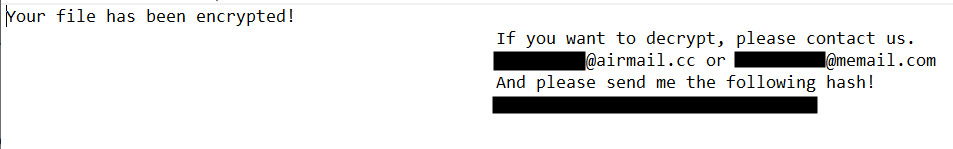
"The only other ransomware I’ve investigated over the years that employed a hybrid approach was WannaCry, and this was auto-spreading rather than human-operated, like DearCry," Loman says.
"‘Copy’ ransomware allows victims to potentially recover some data," he says. "However, with in-place encryption, recovery via undelete tools is impossible."
"Signs suggest that DearCry may be a prototype, possibly rushed into use to seize the opportunity presented by the Microsoft Exchange Server vulnerabilities, or created by less experienced developers."
— Mark Loman, Sophos
To be clear, there are no signs of any connection between WannaCry and DearCry. "DearCry’s code, approach and abilities differ significantly from WannaCry," Loman says. For example, DearCry uses "an embedded RSA encryption key," but does not use a command-and-control server, display a countdown timer to victims "and - most importantly - does not spread itself to other machines on the network."
But one commonality is that both were designed to target "specific exploits," tweets Rickey Gevers, a researcher at security firm Bitdefender. He says that is "nonstandard behavior for ransomware and doesn't really make sense."
Patch Exchange Now, Governments Warn
It's not yet clear how widespread DearCry attacks might be. On March 9, the free ID Ransomware service reported that a handful of DearCry malware samples - from attacks that hit organizations or individuals - were submitted for identification.
Sophos says its endpoint security products recorded the first attempt to infect users with WannaCry on Saturday.
On Friday, the British government's cybersecurity organization urged all Exchange-using organizations to "install the latest updates immediately."
The National Cyber Security Center, the public-facing arm of Britain's GCHQ intelligence agency, says the risk is so severe that until updates get installed, organizations should apply temporary mitigations or else isolate Exchange servers from the internet.
Microsoft Exchange Server 2013, 2016 and 2019 are at risk, and Microsoft has also pushed an update to protect now-unsupported Microsoft Exchange Server 2010. "Organizations running an out-of-support version of Exchange Server should update to a supported version without delay," NCSC says. "Exchange Online - as part of Microsoft 365 - is not affected."
Migrating away from on-premises Exchange in favor of a cloud-based approach is one potential long-term solution, experts say, but not likely a short-term solution for many, given the time, effort and planning required.
"Migrating to O365 is an incredibly complex task for medium-sized organizations, requiring weeks if not months of planning, new infrastructure, major changes, teams of people, etc.," says Kevin Beaumont, a security researcher at Microsoft.
How Did Exchange Flaws Leak?
One outstanding question pertaining to the Exchange zero-day exploits is how attackers first obtained them.
The four flaws in Exchange were reported to Microsoft on Jan. 5, together with a proof-of-concept exploit, by the well-known security researcher Cheng-da Tsai, aka Orange Tsai, who works for Taiwan-based security consultancy Devcore. Later, Microsoft distributed the information to its Microsoft Active Protections Program, or MAPP - a group of 82 vetted business partners, including numerous security firms.
Between the time the flaws were reported and Microsoft released its patches, the exploit somehow leaked, and advanced persistent threat - aka nation-state - attackers began to use the exploit against targets. Microsoft attributed the initial APT attacks to a Chinese state-sponsored group it calls Hafnium. But security firm ESET says at least 10 APT groups - not all with ties to China - have been exploiting the flaw, in some cases before Microsoft released its patches.
Devcore says it did not leak any details, and Tsai has noted that his exploit appears to have been obtained and modified by the APT attackers because their attack code includes information that he hardcoded into his exploit.
Microsoft is reportedly now investigating whether the leak traces to one of its MAPP partners.
Given the timing of DearCry's arrival after Microsoft issued patches, it doesn't appear that the ransomware's developers had any advance knowledge of the Exchange flaws. It's also not clear yet how prevalent DearCry attacks might be. But the crypto-locking malware's operators appear to still be enjoying an early-mover advantage.
"So far, we've not seen any other ransomware exploiting these bugs, but there will inevitably be adversaries out there trying to see how they can take advantage of them - so we advise organizations with on-premises Exchange servers to apply the security patches as soon as they can and also to do a thorough check of activity on their servers," Loman says.