Business Continuity Management / Disaster Recovery , Cybercrime as-a-service , Fraud Management & Cybercrime
Ransomware School: The Rise of GandCrab Disciples
Upskilled Hackers Have Moved to Sodinokibi Ransomware-as-a-Service and Beyond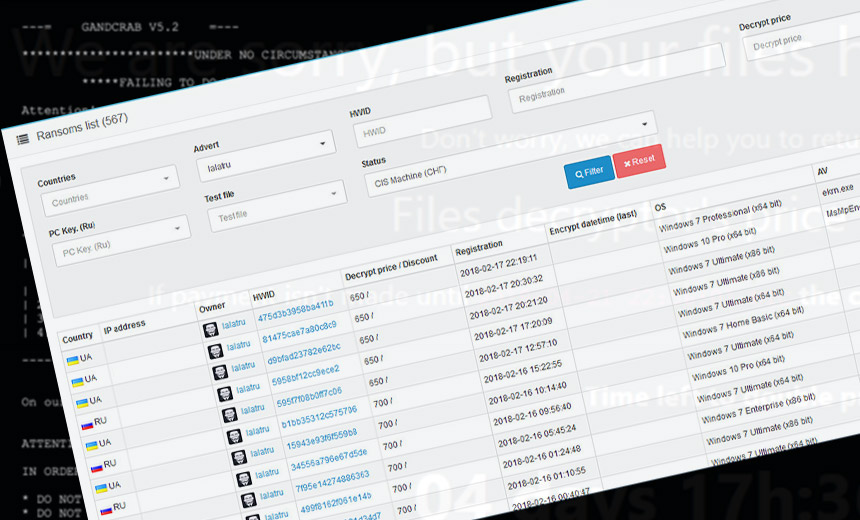
Criminal innovation continues to thrive online, facilitated by the highly specialized cybercrime-as-a-service economy. Ransomware-as-a-service offerings such as Sodinokibi - also known as REvil or Sodin - have made high-quality crypto-locking code available to any attacker who wants to subscribe and share profits.
See Also: Ransomware Response Essential: Fixing Initial Access Vector
This industrialization and democratization of RaaS offerings has led to a profound shift in how ransomware attacks get waged (see: Sodinokibi Ransomware Gang Appears to Be Making a Killing).
"The underground community [has reacted] by developing multidimensional structures of criminal alliances, shadow auctions, trusted groups, secretive relationships and partnerships designed to maximize the revenue of the expanding ransomware market," according to a new report released by New York-based cyber intelligence firm Advanced Intelligence, or AdvIntel. "These fragile unions bring together experts from all across the dark web, who join the efforts to attack the most secure and lucrative targets."
A Questions of Ethics
Ransomware wasn't always like this. Indeed, in the early days, at least in the Russian-speaking cybercrime underground, ransomware was taboo.
Security experts tell Information Security Media Group this was largely for two reasons: One, many hackers viewed ransomware as being unethical, even debating its moral implications, such as the risk posed by infecting hospitals and potentially facilitating patient deaths. Second, such attacks are very noisy, which historically has driven security companies to identify and block this type of malware very quickly and also provoked a law enforcement response.
But AdvIntel says that some members of the Russian-speaking cybercrime community pursued ransomware, albeit very quietly and in small, exclusive groups, including the Cerber RaaS operation.
As ransomware profits continued to increase, more criminals moved to embrace it (see: Ransomware: Average Ransom Payout Increases to $41,000).
But it wasn’t until the introduction of the slickly marketed - if not always well-coded - GandCrab RaaS offering in January 2018, however, that the floodgates truly opened, experts say. GandCrab made ransomware attacks easier than ever for would-be affiliates to launch, driving a cybercrime culture shift.
"Before GandCrab, traditional ransomware teams, run by Russian-speaking hackers, were acting privately, silently and avoided underground forums," AdvIntel says. "The secrecy originated from the traditional pursuit of anonymity across the cybercrime community and as a result of social and cultural repulsion associated with ransomware development. The Russian-speaking underground considered digital extortion unethical, anti-intellectual and damaging for the cybercrime sociocultural ecosystem."
Money Talks
Originally, GandCrab was derided as being just a Cerber knockoff. Quickly, however, it gained cult status.
"GandCrab developed its own charity campaigns and micro-loan partnerships across forums, while community members were devoting poetry to the group and referenced it during forum discussions of relationships and romance," AdvIntel says. "The cybercrime syndicate’s impact was so strong that even one review posted by their official dark web accounts was enough to elevate or erase a certain malware product offered for sale."
One mark of GandCrab's cachet: New loaders and stealers began to be advertised as being "Crab-compatible," and a mark of quality quickly become “sold to GandCrab," says Yelisey Boguslavskiy, director of research at AdvIntel (see: GandCrab Ransomware Partners With Crypter Service).
Whereas RaaS operators previously tended to work only with a small cadre of hand-picked associates, AdvIntel says anyone could become an affiliate of GandCrab, which helped shepherd newbies through the process of turning a criminal profit.
"For a huge proportion of those who worked with GandCrab, this was the first real experience with ransomware," AdvIntel says. "Their RaaS programs and affiliate relationships were built in a way to serve as a safe haven for those who just started to navigate across the murky waters of cybercrime."
Upskilled GandCrab Affiliates Move On
GandCrab also served as a launching pad for other ransomware endeavors. The ransomware collectives “jsworm” and affiliate “PenLat” later launched the JSworm and Nemty ransomware strains, AdvIntel says, while the “truniger” - aka “TeamSnatch” - hacker collective appeared to learn the RaaS ropes with GandCrab before moving on to take down bigger prey.
On May 31, however, the operators of GandCrab, boasting that their affiliates had earned more than $2 billion, announced their retirement (see: Ransomware: As GandCrab Retires, Sodinokibi Rises).
Security experts say that some big-name "Crab" supporters, including truniger as well as the threat actor “Lalartu" - the name of a ghostly, vampiric spirit in Sumerian legend - at some point shifted from working with GandCrab to Sodinokibi, which now dominates the RaaS landscape.
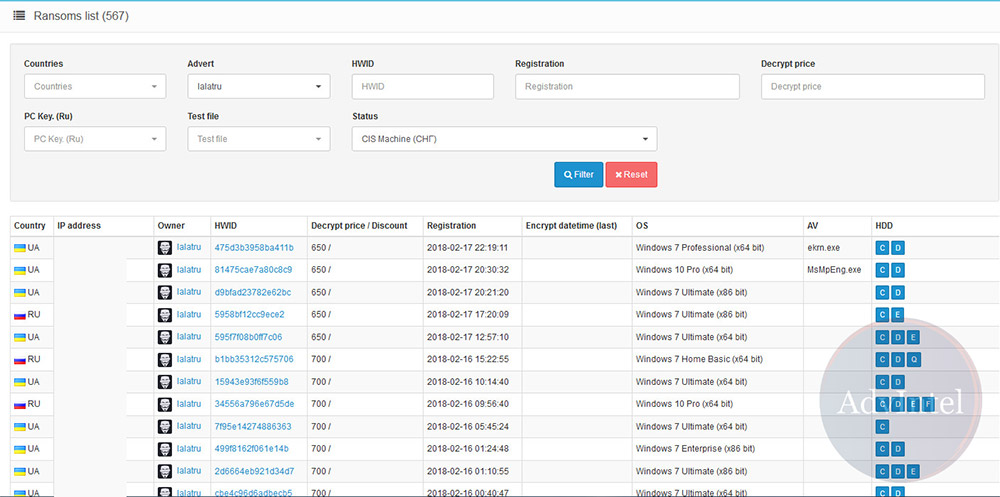
Here's how Sodinokibi works: Individuals or groups sign up to be affiliates and receive a unique version of malware tied to their affiliate ID, so any ransom payments can be correctly routed.
Sodinokibi affiliates keep 60 percent of every ransom payment, rising to 70 percent after they book three successful ransom payments, McAfee's John Fokker and Christiaan Beek note in a recent research report. The remaining 30 to 40 percent gets remitted to the actor or actors behind Sodinokibi. The average ransom amount paid to attackers wielding that strain of ransomware is between $2,500 and $5,000, meaning an average payday to affiliates of $1,800 to $3,500 every time a victim pays.
Relationship Status: Unclear
The precise relationship between GandCrab and Sodinokibi, meanwhile, remains unknown.
Security firm Secureworks says that based on clues, it believes that the threat groups behind GandCrab and Sodinokibi "overlap or are linked."
"From the first time we saw Sodinokibi, you could immediately see the parallels," Bill Siegel, CEO of Coveware, has told ISMG. "Everything from the way the TOR sites work, down to the personality of the staff that manages the chat window for victims on the TOR site. It felt very much like the same group that has made some incremental upgrades to how their operation worked." (See: Did GandCrab Gang Fake Its Ransomware Retirement?)
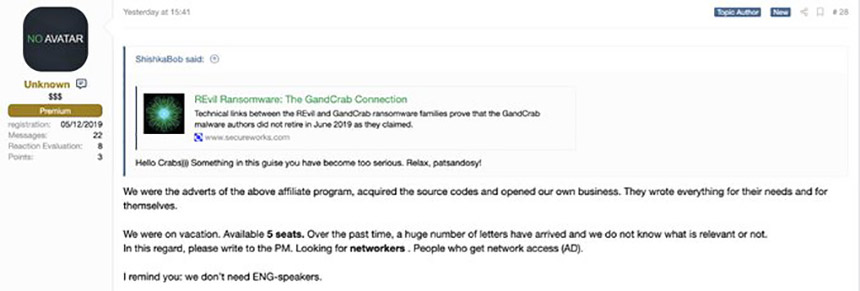
Several weeks ago, meanwhile, the Sodinokibi actors posted a message on an underground forum claiming that they obtained the source code from GandCrab and set up their own shop. ISMG was not able to verify that claim.
Big Earner
Regardless, Sodinokibi appears to be incredibly lucrative for the scheme's operators, who take a cut of every ransom payment. The same goes for at least some of the RaaS operation's affiliates. Lalartu, for example, claimed to have made $287,000 in just 72 hours. McAfee says it has counted at least 41 affiliates, inluding individuals and collectives.
Lalartu and Truniger don't appear to only be working with Sodinokibi. AdvIntel reports that Truniger - operating under the Team Snatch moniker - was also behind the April breach of Germany IT service provider CityComp, which led to the theft of data from such organizations as Airbus, BT, Oracle, Porsche, SAP, Toshiba, Volkswagen and others, as well as a ransom demand that was reportedly worth $5,000. But when CityComp didn't pay, the attackers went ahead and leaked the data.
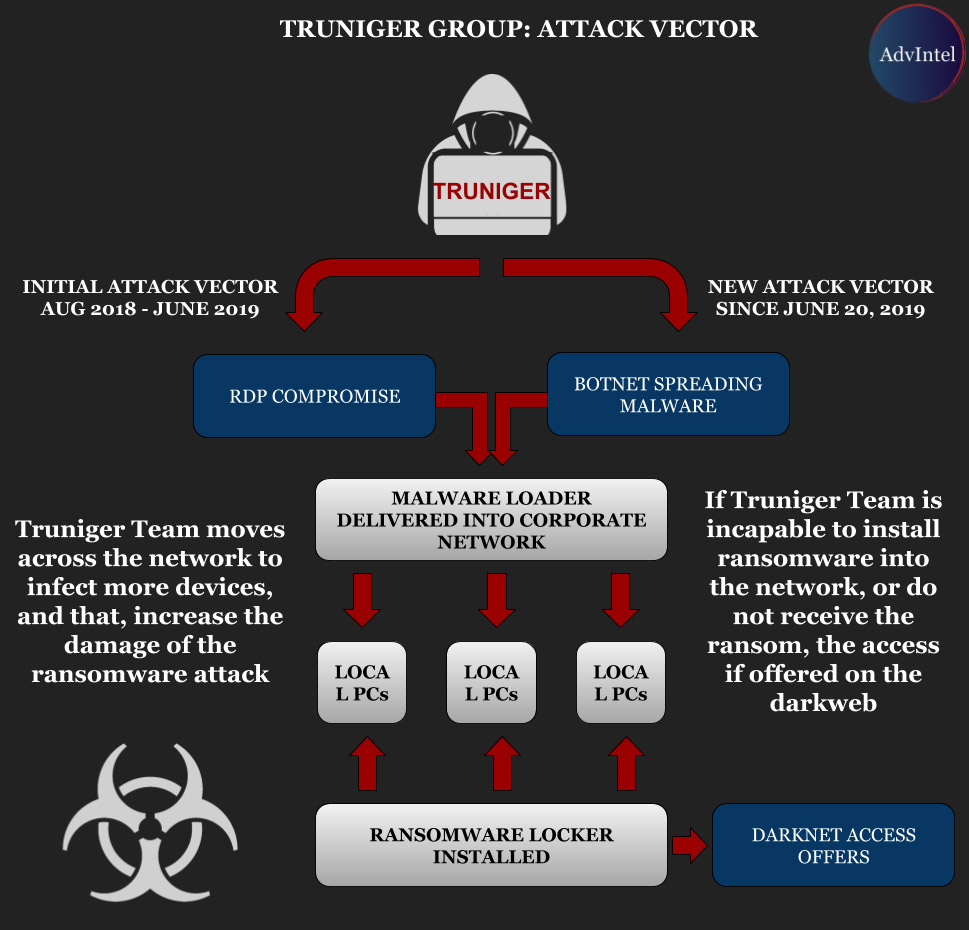
AdvIntel says the group has also been behind network intrusions at insurers and municipal governments in Italy. And in Canada, at least one manufacturer as well as a KIA dealership was targeted.
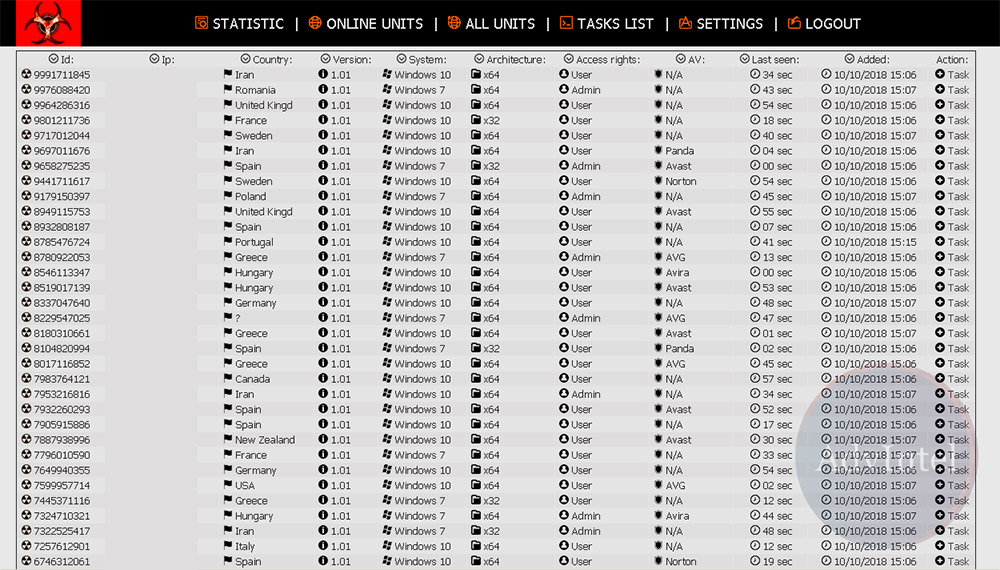
When the hacking collective cannot infect a victim's network with ransomware, then it often sells the network access to others, AdvIntel says.
In that respect, the group continues to demonstrate how cybercrime keeps evolving. New tools and services come onto the market, making it easier than ever for less-skilled attackers to use the tools to turn an illicit profit.
Some of those threat actors - such as Truniger - may initially display scant initial technical sophistication. But as they forge new partnerships and gain new abilities, their reach and earning potential improves - as does their list of victims.