Cybercrime , Cybercrime as-a-service , Cyberwarfare / Nation-State Attacks
Ransomware Landscape: REvil Is One of Many Operators
Biden Administration Says Attempted Ransomware Disruption Efforts Won't Be Immediate
As the Biden administration attempts to force Russia to crack down on domestic cybercriminals, one challenge will be the sheer diversity of attack code being wielded. Another is that any proactive moves Moscow does make will likely require many months to take effect, as will White House efforts to bolster U.S. cybersecurity defenses in the public and private sectors.
See Also: The State of Organizations' Security Posture as of Q1 2018
For cracking down on individual ransomware operations, one hurdle remains on the current threat landscape: As ever, multiple strains of crypto-locking malware are being used by many different attackers - not just operations and affiliates based in Russia - and there's a constant influx of new strains and players, driven by the increasing profits to be obtained via ransomware, and backed by a vibrant cybercrime-as-a-service economy.
Ransomware-as-a-service operations have also burgeoned, with cybersecurity firm Intel 471 late last year counting five major players, nine up-and-coming operations and 10 newcomers.
To pick just one operator: The massive attack against software developer Kaseya that came to light earlier this month was the latest in a long line of recent hits tracing back to ransomware-wielding attackers, and in this case to REvil, which many experts suspect has operations based in or around Russia.
Again, however, that's just one player. "For perspective, REvil accounts for less than 10% of global ransomware incidents," says Brett Callow, a threat analyst at security firm Emsisoft.
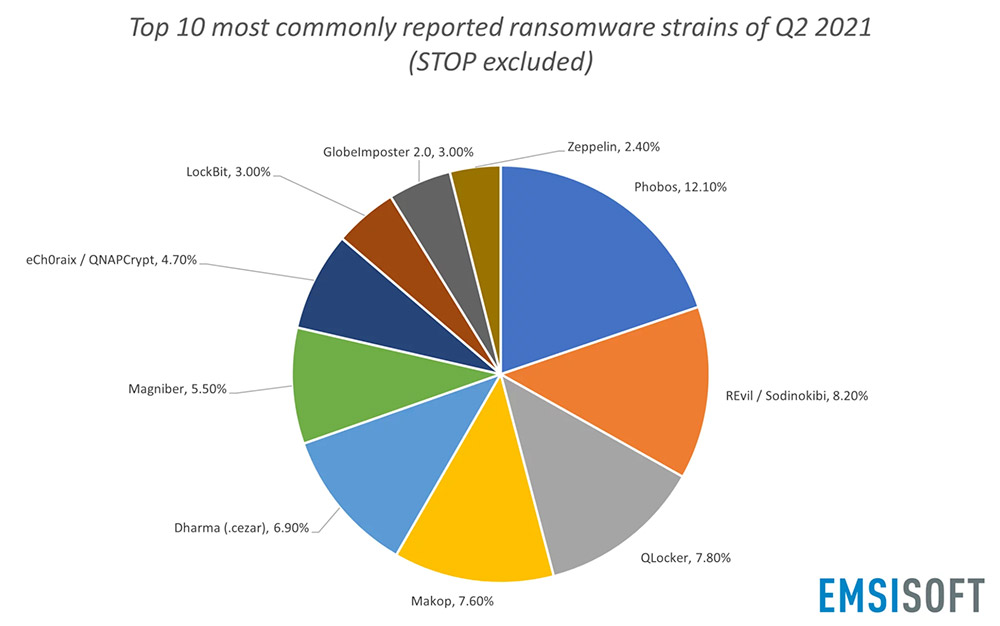
From April through June, based on 137,537 submissions made to Emsisoft and the free ID Ransomware site, the company says the most commonly seen ransomware tied to successful attacks was the Stop - aka Djvu - strain, although it "primarily impacts home users and typically spreads through cracked software, key generators and activators." Other dominant ransomware strains, in findings that changed little from Q1 to Q2, included Phobos, Dharma and Makop.
Every security firm's perspective on top threats varies based on what their customers, often based in different geographies, might be encountering. In the first three months of this year, McAfee found that REvil was the strain of ransomware most encountered by users of its software, followed by RansomeXX, Ryuk, NetWalker - disrupted in January - and Thanos.
Threat intelligence firm Recorded Future, meanwhile, says that based on ransomware operators' postings to their data leak sites, 42% of recent, known ransomware victims trace to REvil.
But not all attacks become public knowledge. In the U.S. and other countries, many victims are not legally required to report if they've been hit by ransomware or paid any ransom, except, perhaps, if consumers' personal data was stolen.
Attackers Prefer the Shadows
In addition, attackers often prefer to operate in the shadows to better evade law enforcement officials.
Many ransomware-wielding attackers will first attempt to contact victims directly and get them to pay a ransom, promising that if the organization does so quickly, then attackers will never leak their data or attempt to "name and shame" them. Hence the number of victims who simply pay remains unknown.
Furthermore, the damage caused by a single attack from a more sophisticated ransomware operation, such as REvil, can be severe. Miami-based Kaseya's software is used by a number of managed service providers to manage clients' endpoints, and up to 60 MSPs and 1,500 of their clients were infected by REvil - aka Sodinokibi - ransomware just in that single attack.
REvil has also been tied to the attack against meat-processing giant JBS - who paid attackers an $11 million ransom - and many other attacks. Another operation, called DarkSide, claimed credit for the May attack against Colonial Pipeline Co., which supplies 45% of the fuel used along the East Coast. Shortly after the attack, DarkSide claimed it would shut down its ransomware-as-a-service operation because of unwanted publicity and attention.
Focus on Russia
Many security experts suspect that many ransomware operations, including REvil, are run by Russian speakers and based in Russia or a neighboring country.
But any ransomware-as-a-service operation, such as REvil, could have administrators working from multiple countries. In addition, RaaS operations often provide their ransomware as a service to affiliates, who take the crypto-locking malware, use it to infect victims and profit-share any ransom that gets paid. As with administrators, affiliates probably hail from numerous countries, too.
If cracking down on ransomware attackers based in Russia might not fix the entire problem, many experts say it would at least go a long way toward disrupting such attacks.
In the wake of the Kaseya attack, President Joe Biden on Friday repeated a demand to Russian President Vladimir Putin, previously voiced at their Geneva summit in mid-June, that Russia crack down on ransomware-wielding criminals operating inside its borders (see: Biden Faces Russian Ransomware Curtailment Challenge).
Biden said his government is prepared to take "any necessary action to defend its people and its critical infrastructure in the face" of these attacks, according to the official readout posted by the White House.
"I made it very clear to him that the United States expects when a ransomware operation is coming from his soil even though it's not sponsored by the state, we expect them to act if we give them enough information to act on who that is," Biden told reporters, adding that there would be consequences for Moscow if it doesn't act.
Biden added that the U.S. has also been setting up closer ties with Russia to be able to more easily share concerns about attacks that target either country.
Mitigation: Multiple Avenues Being Pursued
In a Friday call with reporters, a senior administration official - speaking on condition that they not be named - said the White House continues to pursue multiple avenues to deal with ransomware, including "this leader-level engagement" between Biden and Putin, which the president has said will take time to implement and for him to evaluate - perhaps six months or more.
Beyond that, however, "this is more than just a conversation that’s taking place between the two leaders," the official said. "This is really about our own resilience, as a nation, in the face of these attacks, and strengthening that," including building on Biden's cybersecurity executive order to modernize U.S. government systems as well as systems run by the private companies that make up the vast majority of the critical infrastructure sector.
The overall effort is also focusing on working more closely with international partners - and helping to boost their resilience - as well as disrupting cryptocurrency flows to criminals, the official said.
"So, this is a broad campaign and won’t have an immediate on/off effect like a light switch," the official said.
Will Russia Crack Down on Cybercrime?
How information sharing between the U.S. and Russia might work in practice - and if it will actually lead to any substantial action on Moscow's part - remains to be seen.
Cybersecurity experts say that for years, Russian intelligence agencies and law enforcement officials have allowed criminal hackers to operate from inside the country, provided they do not target Russia or neighboring members of the post-Soviet Commonwealth of Independent States, and occasionally do favors for the government (see: Russia's Cybercrime Rule Reminder: Never Hack Russians).
U.S. law enforcement agencies have previously attempted to work with authorities in Russia and Ukraine, but they've faced numerous challenges, including what in some cases appeared to be widespread corruption in some regions.
As the MIT Technology Review reported last week, the FBI - as part of Operation Trident Breach - in 2010 had attempted to work with authorities in Russia and Ukraine to arrest the mastermind behind the notorious Zeus Trojan and Evil Corp. cybercrime network - Evgeniy Bogachev - together with a top customer, a Ukrainian named Vyacheslav Penchukov, aka "Tank," as well as Russian national Maksim Yakubets, aka "Aqua," who allegedly handled money laundering for Evil Corp.
While dozens of lower-level suspects were arrested across the five countries - also including the U.K. and the Netherlands - Bogachev, Penchukov and Yakubets evaded arrest and continue to do so.

NIST Promises Updated Guidance
As noted, the White House is focusing not just on disrupting criminals, but also attempting to bolster the state of U.S. critical infrastructure cybersecurity.
Where should organizations start, if they want to ensure they can quickly spot ransomware attacks and be in the best position to never even have to consider paying a ransom?
Answering that question is the focus of updated guidance from the U.S. National Institute of Standards and Technology
"Due to the recent surge in ransomware attacks against critical U.S. targets, NIST has accelerated the update to its cyber resiliency guideline, Special Publication 800-160, Volume 2, "Developing Cyber Resilient Systems," the agency says. "The initial public draft has been completed and is currently undergoing an internal review. The publication is on the fast track with expected posting and release for public comment in August."
NIST notes: "The focus of cyber resiliency is on mitigating cyberattacks on systems, organizations, and critical infrastructures from the advanced persistent threat. It is important to understand what effects these mitigations have on adversaries."
Updates to the guidance range from active scanning and maintaining a deception environment to fostering a diverse supply chain and simulating attacks to study the effect of systems and defenses.






















