Endpoint Detection & Response (EDR) , Endpoint Protection Platforms (EPP) , Endpoint Security
RagnarLocker Deploys a Virtual Machine to Hide Ransomware
Ragnar Gang's Innovation: Installing Oracle VirtualBox Windows XP Virtual Machine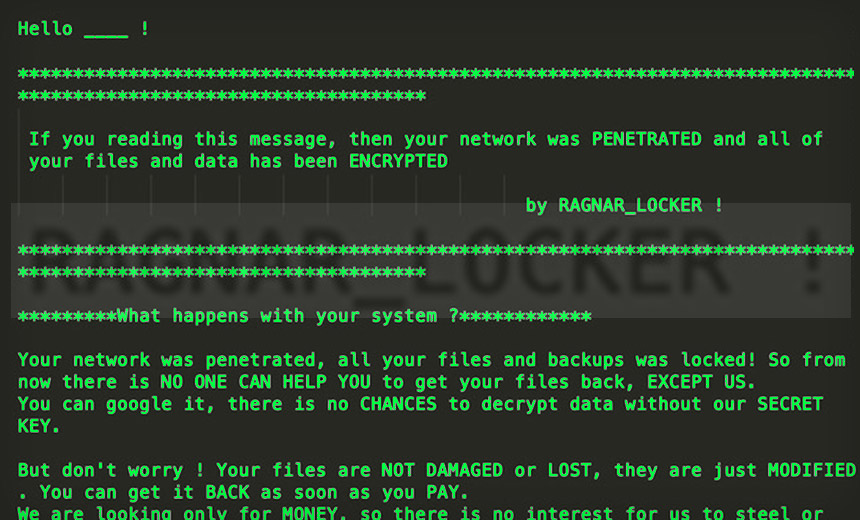
Ransomware-wielding gangs, in their ongoing pursuit of new ways to successfully shake down victims, keep innovating. Many continue to refine not just their business model but also their technology in an attempt to make their malware tougher to block and encrypted files tougher to crack.
See Also: Enabling Government for Modernized IT
To the list of tricks being deployed by ransomware gangs, add this new move: The RagnarLocker gang has been using full virtual machines to try to hide their crypto-locking malware to enable it to forcibly encrypt a victim's systems, security firm Sophos warns.
"In a recently detected attack, Ragnar Locker ransomware was deployed inside an Oracle VirtualBox Windows XP virtual machine," Sophos reports in a blog post. "The attack payload was a 122 MB installer with a 282 MB virtual image inside - all to conceal a 49 KB ransomware executable."
“This is the first time we have seen virtual machines used for ransomware," says Mark Loman, director of engineering at Sophos.
The security firm declined to name the victim, the sector in which they operate, or how much the Ragnar gang was demanding as a ransom.
If It Works, It's Not Overkill
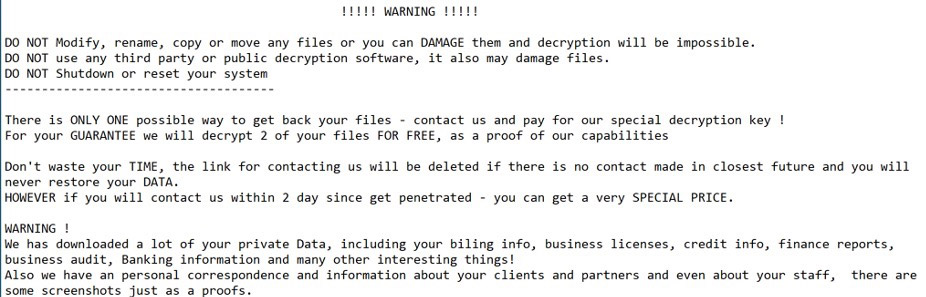
Bringing a massive installer to bear on a system, simply to run a small piece of malware, is without a doubt ostentatious. But is it effective?
"The overhead involved to covertly run their 50 KB ransomware seems like a bold, noisy move, but could pay off in some networks that are not properly protected against ransomware," Loman says.
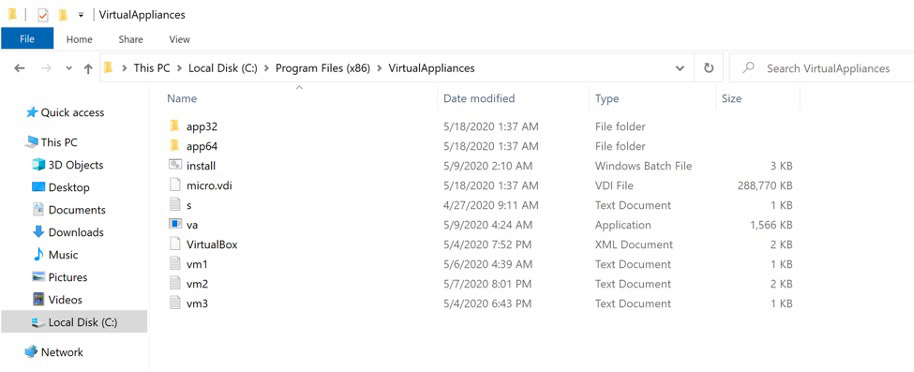
In the attack Sophos studied, the attackers used a Group Policy Objects task to run an executable that downloaded the 122 MB installer file from an external server. That installer included an executable and support files, but primarily a virtual machine: an old Oracle VirtualBox hypervisor, which Sophos notes is technically "Sun xVM VirtualBox version 3.0.4 from Aug. 5, 2009. Oracle bought Sun Microsystems in 2010."
"They are deploying a well-known trusted hypervisor to hundreds of endpoints simultaneously, together with a preinstalled and preconfigured virtual disk image guaranteed to run their ransomware," Loman says.
The next part of the attack involves the VM installing a virtual disk image file called "micro.vdi" which is "a stripped-down version of the Windows XP SP3 operating system, called MicroXP v0.82," that includes the tiny RagnarLocker executable, Sophos says. It then gets compiled for just that victim.
Ransomware Deletes Shadow Copies
Vitali Kremez, a strategic adviser to security firm SentinelOne, who's analyzed Ragnar's ransomware, says it includes features designed to make it difficult for victims to restore their systems. On May 1, Kremez reported that a new version of RagnarLocker was disabling the built-in Windows Defender anti-virus software on victims' systems, and it might also be using the EternalBlue exploit against a long-patched flaw in Windows SMB_v1 to help spread.
2020-05-01:#Ragnarok (!RagnarLocker) #Ransomware
— Vitali Kremez (@VK_Intel) May 2, 2020
Disables Windows Defender | Possible #EternalBlue Exploit Spreader with *NIX config setup
#YARA Signature + Extracted Configuration https://t.co/Znhsd6OWKG
h/t @malwrhunterteam | @JakubKroustek pic.twitter.com/Qi3QuhreuZ
Indeed, as part of the attack detailed by Sophos, a script deletes volume shadow copies to block victims from restoring older versions of their files. Many strains of ransomware now employ this tactic.
The script also enumerates "all local disks, connected removable drives and mapped network drives on the physical machine, so they can be configured to be accessed from within the virtual machine," Sophos says.
After stopping numerous operating system processes, the ransomware mounts all available network drives, encrypts all files on them and drops a ransom note.
"Since the vrun.exe ransomware application runs inside the virtual guest machine, its process and behaviors can run unhindered, because they’re out of reach for security software on the physical host machine," Sophos says.
Ragnar Gang: RDP Experience
RagnarLocker is also known as Ragnarök, which is the name of a battle at the end of the world in Norse mythology. The RagnarLocker name could be a play on Ragnar Lodbrok, a mythical Viking hero and Danish king also from Norse mythology. (Ragnar is Norse for warrior.) Security experts say there appears to be a single gang behind RagnarLocker attacks, but whether they're Scandinavian remains unknown.
In a recent report, Microsoft called out RagnarLocker as being one of four strains of ransomware - along with Maze, RobbinHood and Vatet loader - that regularly get dropped onto systems after attackers gain remote access using stolen or brute-forced RDP credentials (see: 10 Ransomware Strains Being Used in Advanced Attacks).
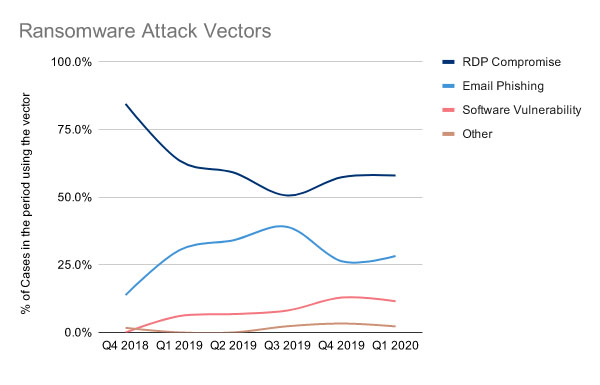
Microsoft notes that the Ragnar gang "heavily uses RDP and Cobalt Strike with stolen credentials." Using RDP gives the gang remote access to a network. Once they have a foothold, they can use Cobalt Strike, a legitimate penetration testing framework, to help gain administrator-level access to endpoints.
After that, the group may use "native Windows administrative tools such as PowerShell" - a task-based, command-line shell and scripting language in Windows - "and Windows Group Policy Objects (GPOs) to move laterally across the network to Windows clients and servers," Sophos says.
Gang Leaks Victims' Data
RagnarLocker is also one of about a dozen gangs that have been tied to not just infecting systems with ransomware, but first stealing data in an attempt to gain more leverage over victims (see: Crypto-Lock and Tell: Ransomware Gangs Double Down on Leaks).
For victims that refuse to pay the gang's ransom demand, attackers first try to name and shame them, typically via a dedicated leaks site, before trickling out data to try and force payment. In many cases, if the victim doesn't pay, the gang will dump all of the stolen data online for anyone to download, as a lesson to future victims (see: Ransomware Reminder: Paying Ransoms Doesn't Pay).

RagnarLocker Victim: Energias de Portugal
In April, the Ragnarok gang, wielding RagnarLocker, attempted to extort 1,580 bitcoins - worth about €10 million ($11 million) at the time - from Energias de Portugal, a major Portuguese electric utilities company based in Lisbon. Attackers claimed to have stolen 10 TB of data from EDP (see: Emotet, Ryuk, TrickBot: 'Loader-Ransomware-Banker Trifecta').
In the case of the EDP attack, "the actors were in the victim's network for some time before running the [ransomware]," the anti-malware group MalwareHunterTeam reports.
2020-04-14:#RagnarLocker (!Ragnarok) #Ransomware
— Vitali Kremez (@VK_Intel) April 14, 2020
Extorting Energias de Portugal Group for 10 Mil Euro
Remote Service Killer (Prevent Easy Recovery) + Backup & Database:
LogMein | ConnectWise | Splashtop| Pulseway
Prevhttps://t.co/AvlDfLkx3a
h/t @malwrhunterteam pic.twitter.com/1TzagS8pUZ
Ransomware incident response firm Coveware reports that based on the more than 1,000 cases it investigated in the first three months of this year, 8.7% involved data exfiltration (see: Ransomware: Average Business Payout Surges to $111,605).





















