Fraud Management & Cybercrime , Fraud Risk Management , Ransomware
PR Campaign: Babuk Ransomware Gang Claims Decryptor Repaired
Gang Issued Statement After Emsisoft Found Decryptor Flaw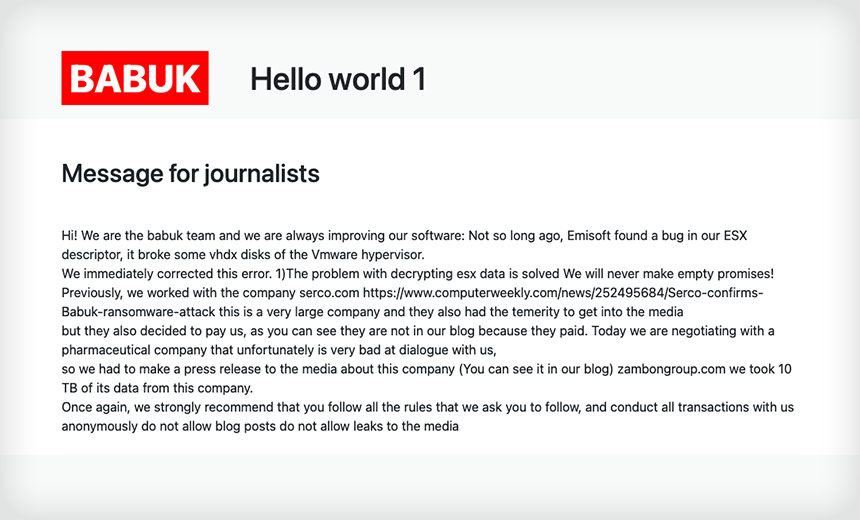
The Babuk ransomware gang launched a public relations campaign Saturday, posting a message on its website saying it had repaired a defect in the decryptor it provides to victims who pay the ransom demand.
"Message for journalists. Hi. We are the babuk team and we are always improving our software: Not so long ago, Emisoft found a bug in our ESX descriptor, it broke some vhdx disks of the Vmware hypervisor," the note says. "We immediately corrected this error."
When commenting on Babuk taking responsibility for an April 14 ransomware attack against the Houston Rockets basketball team, Brett Callow, a threat analyst with the security firm Emsisoft told Information Security Media Group that Babuk's decryptor destroys the files it decrypts (see: Houston Rockets Investigate Ransomware Attack).
Now, Emsisoft is checking if, in fact, the Babuk gang has repaired the decryptor.
Even if it has fixed the flaw, the decryptor could still be faulty, resulting in its victims suffering data loss or additional malware infections.
"The simple fact is that it would be a huge mistake to assume that criminals' decryptors will work as they should. At best, they'll perform poorly," Callow says. "At worst, they'll trash the data. If an organization intends to use a tool which was supplied by a ransomware gang, it's critical that the encrypted files be backed up first as a safeguard."
Efforts to Win a Ransom
Philip Reitinger, president and CEO of the Global Cyber Alliance, says he wasn't surprised by Babuk's latest PR move, pointing out that the gang is taking steps in hopes of getting more victims to pay a ransom.
"Ransomware gangs want victims to believe that paying the money means getting your data back and preventing a leak. That's clearly a 'business imperative' for them, and in that regard, I'm not surprised that blog was written or by its content, which is focused on these two issues," he says.
Erin Sindelar, threat researcher at Trend Micro, says ransomware gangs are now more frequently posting messages. "We haven’t seen this specifically from Babuk before, but we expect more of this type of notification to continue as actors seek new, more convincing ways to encourage victims to pay," she says.
Trend Micro first spotted Babuk in December 2020, at which time researchers labeled it Vasa Locker. It was given its current moniker in 2021.
Rockets Attack
The Houston Rockets reported on April 14 that the team was hit with ransomware, although it did not say which variant was involved. The malware did not halt operations, and security staffers were able to contain the ransomware, the team said.
Last week, Babuk posted files and folders to its site that it claimed had been taken from the Rockets. The team has not confirmed that it has lost any data.
Callow noted at the time that if Babuk was behind the attack, recovering the data could be difficult, even if the team manages to obtain a decryptor key. Emsisoft pointed to a bug that would cause Babuk only to rename files on an ESXi server, but not encrypt them.
"Babuk incidents are particularly problematic, as the Linux decryptor the actor supplies is buggy and will actually trash data as it's decrypted, resulting in it being lost," Callow said.






















