Fraud Management & Cybercrime , Fraud Risk Management , Social Engineering
Phishing Campaign Features Fake Office 365 Update
Trend Micro Says Campaign Designed to Steal Executives' Credentials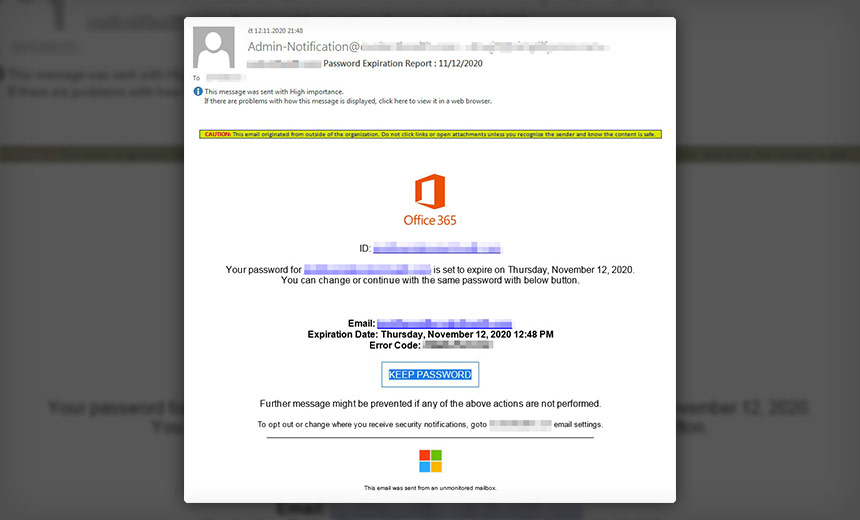
A targeted phishing campaign is using a fake Microsoft Office 365 update to steal email credentials from business executives, and the credentials are then being offered for sale in underground forums, security firm Trend Micro reports.
See Also: OnDemand | MFA, Passwordless, & Passkeys: Defend Your Workforce
The ongoing campaign, which began in May 2020, is using a compromised virtual private network and URLs to send phishing emails, the report notes.
"The attackers reuse compromised hosts for the phishing pages targeting organizations in the manufacturing, real estate, finance, government and technological industries in several countries, such as Japan, the United States, U.K., Canada, Australia and Europe," the researchers note.
The phishing campaign is estimated to have compromised 300 URLs and 70 email addresses, including 40 legitimate email accounts of company CEOs, directors, owners and founders as well as other enterprise employee targets, Trend Micro says.
The compromised credentials are then offered for sale in underground forums for $250 to $500 each, the report notes.
Phishing Methods
The campaign begins with the hackers sending phishing messages, portrayed as Office 365 password expiration updates, to C-level executives after obtaining their emails from LinkedIn, the report says.
The phishing messages appear to come from legitimate sources, such as an organization's IT support staff. "They prompt the targets to click the embedded link in the email if they want to continue using the same [Office 365] password; choosing the 'Keep Password' option leads the user to the phishing page," the report notes.
On the phishing page, the victims are asked to enter their current credentials into the fake domain as a way of keeping their present usernames and passwords. The attackers then use those credentials to host other phishing pages and send more emails to other potential targets, according to Trend Micro.
Once the victims' credentials have been harvested, they are offered for sale on underground forums, the report adds.
Misconfigurations Found
Trend Micro notes it was able to access the phishing kits due to misconfigurations in the domains the hackers used.
"This exposed content of the directory, allowing the download of the phishing kit and associated log files without authentication," the report notes. "This also allowed us to get additional insights on the campaign and find evidence for potential attribution of the kits in their different deployment locations."
A further analysis of the phishing kit revealed that the malicious tools the hackers used had undergone changes during the campaign, according to Trend Micro.
The latest kit - dubbed "V4" by the researchers - was updated with a block list containing a set of predefined IP addresses to block access to security companies or large cloud providers, the report notes. Also, it can detect bot scanning or crawling attempts and provide alternative content when bots are detected.
Other Attacks
In August 2020, Trend Micro uncovered a business email compromise scam that targeted the Office 365 accounts of business executives at more than 1,000 companies worldwide (see: BEC Scam Targets Executives' Office 365 Accounts).
And in a phishing campaign detected in May 2020, executives at more than 150 businesses were targeted for credential theft, security firm Group-IB reported (see: Phishing Campaigns Target Senior Executives via Office 365).






















