Cybercrime , Fraud Management & Cybercrime
Optus Attacker Halts AU$1.5 Million Extortion Attempt
Exclusive: Medicare Numbers Exposed and Optus Says It Has Not Paid a Ransom
The person who stole 10 million customer records from Australia’s second-largest telecommunications company delivered two dramatic twists on Tuesday as the country reels from the impact of a massive data breach.
The person goes by the nickname “Optusdata” on a forum where cybercriminals buy and sell stolen data. Early Tuesday, Optusdata posted an additional 10,000 Optus customer records, a shock move that accompanied an ongoing extortion attempt.
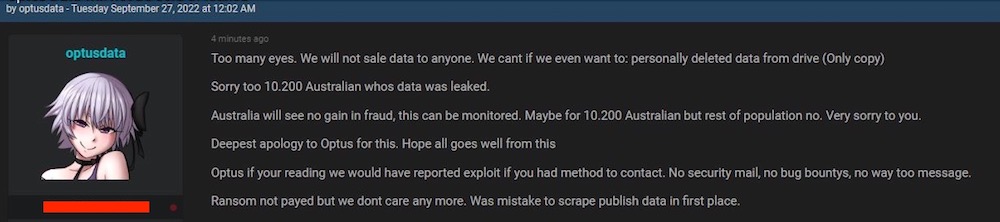
But around 10 AM AEST Tuesday morning, Optusdata deleted the post along with three samples of the data. The person wrote in a fresh post that they were no longer seeking a ransom from Optus. The new post says in rough grammar: “Too many eyes. We will not sale data to anyone. Sorry too 10.200 Australians whos data was leaked.”
In an exclusive, an Optus spokesperson tells ISMG that the company has not paid a ransom to the attacker. Optusdata was demanding AU$1.5 million in the Monero cryptocurrency and was threatening if not paid to sell the data to other cybercriminals.
Also, ISMG broke the news on Tuesday morning that Medicare numbers, which are identifiers associated with Australia's national health insurance scheme, were also included in the stolen data.
Many questions remain, including why Optusdata has backed off the extortion demand. Optusdata sent this reporter a message on Tuesday morning with a link to the new post. This reporter asked why Optusdata had changed their mind but did not receive an answer.
Calls for Better Data Protection
Tuesday’s drama has added to intensifying pressure on Optus to be held to account for the loss of nearly 10 million customer records.
On Monday night Home Affairs Minister Claire O’Neil told ABC’s 7:30 news program that the basic personal details for 9.8 million Optus customers were compromised. She said that for 2.8 million people, extensive personal information had been exposed such as a driver’s license or passport numbers. No passwords or financial information was compromised.
Minister for Cyber Security @ClareONeilMP says Australia is "probably a decade behind" in privacy protections, and the government "has to be involved when the stakes are this high" following Optus' cyber security breach. Watch her full interview with Laura Tingle below. #abc730 pic.twitter.com/Mk791iOehl
— abc730 (@abc730) September 26, 2022
O’Neil is also the country’s first cyber security minister, a recently created ministry.
O’Neil says the smaller group faces a significant scope for fraud and ID theft. People in that group have enough identity information exposed to count for “100 points of ID.” That’s a system used in Australia where certain identity documents are assigned a point value and used when applying for, say, a rental property or a bank account. Applicants are required to meet a points threshold based on the ID documents they hold.
ABC 7:30 journalist Laura Tingle posed a question to O’Neil about the incident: “You don’t certainly seem to be buying the line from Optus that this was a sophisticated attack.” O’Neil replied: “Well, it wasn’t, so no.”
Optus has said it will supply one year of credit monitoring and ID protection to those “most affected” by the incident. But it remains not entirely clear exactly who will qualify. Optus has also apologized.
The incident has touched off calls for stronger laws to protect personal data and larger fines for entities that fail to protect it. Australia has a mandatory data breach reporting law on the books, but it is less stringent than Europe’s General Data Protection Regulation scheme.
Medicare Numbers Exposed
Earlier this week, ISMG was first to confirm with the Optus attacker and a second source that the cause of the breach was an unauthenticated Application Programming Interface (API) that was left exposed to the internet. APIs are interfaces that allow different applications and services to exchange data (see Optus Under $1 Million Extortion Threat in Data Breach).
Normally, someone only gets access to the data they’re authorized to see when, say, logging into a website that’s using APIs to fetch data. But Optus left an API open on the internet that did not require someone to authenticate.
Optusdata told ISMG in a direct message that’s how the data was stolen and wrote: "No authenticate needed. That is bad access control. All open to internet for any one to use." ISMG confirmed Optusdata’s explanation with a second source within Australia with knowledge of the situation.
Optusdata says they then sequentially accessed and downloaded the customer records using the API, taking advantage of the grave security error.
Optus has not yet officially acknowledged the cause of the breach. But the ease at which Optusdata was able to steal an enormous volume of data has rankled those affected.
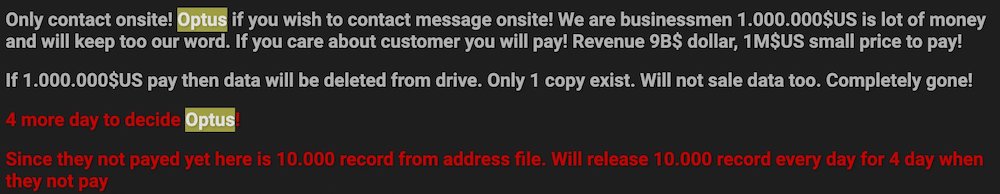
And the pressure increased on Tuesday when Optusdata initially intensified their extortion threat. Optusdata wrote in broken English: “Since they [Optus] not payed yet here is 10.000 record from address file. Will release 10.000 record every day for 4 day when they not pay.”
Despite eventually withdrawing the extortion attempt and deleting the data samples, there is an immediate risk for the 10,200 people who are in the samples.
ISMG is also first to report that the newly released data indicates that some customer records have ID numbers for Medicare, which is Australia’s national health insurance system.

Quick observation on this new data. It appears Medicare numbers may be exposed for some people. Redacted screenshot below. #Optus #OptusDataBreach pic.twitter.com/t3VfZ6cg4j
— Jeremy Kirk (@Jeremy_Kirk) September 26, 2022
Around four hours after ISMG tweeted its finding about the Medicare numbers, O’Neil said in a news release she was “incredibly concerned” about the finding and that the government had not known those identifiers were in the breach.
“Medicare numbers were never advised to form part of the compromised information from the breach,” she says in a statement.
Of the 10,000 new records, 55 contained Medicare numbers, in addition to other data including names, addresses, email addresses, birth dates and sometimes driver’s license or passport numbers.
Other users on the cybercrime forum have now copied and reposted the data samples originally posted by Optusdata, which means it will continue to circulate and poses risks of ID theft.