NIST Guide Targets Supply Chain Risks
Taking a Multi-Tier Approach to Supply Chain Threats
Breaking down silos should help organizations mitigate vulnerabilities introduced into their systems from the information and communications technology supply chain, says the co-author of revised guidance being drafted by the National Institute of Standards and Technology.
See Also: Bolstering Australia’s Security Posture with Accelerated ZTNA
Organizations that institute separate programs to implement supply chain risk management pose risks to the entire enterprise, says Jon Boyens, a NIST senior adviser for information security. "Acquisitions offices may not be communicating and seeking needed information and input from the office that will own and use the information system and, ultimately, manage the risks associated with the system," he says.
Supply Chain Relationships
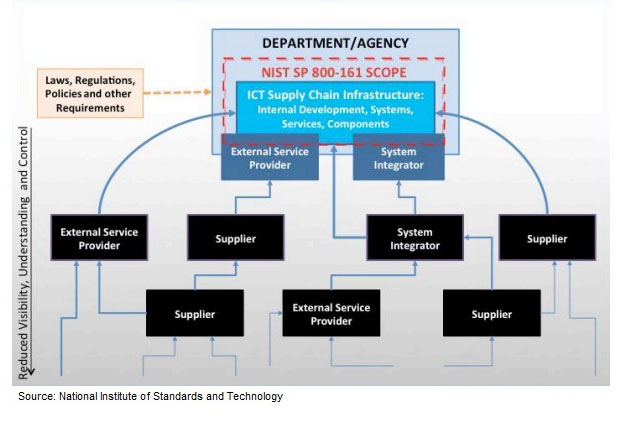 Earlier this month, NIST unveiled the second draft of Special Publication 800-161, Supply Chain Risk Management Practices for Federal Information Systems and Organizations, guidance for how to integrate information and communications technology supply chain risk management into an organization's risk management activities by applying a multi-tiered approach that includes risk assessments and risk mitigation activities.
Earlier this month, NIST unveiled the second draft of Special Publication 800-161, Supply Chain Risk Management Practices for Federal Information Systems and Organizations, guidance for how to integrate information and communications technology supply chain risk management into an organization's risk management activities by applying a multi-tiered approach that includes risk assessments and risk mitigation activities.
Describing the Supply Chain
NIST defines the information and communications supply chain as a complex, globally distributed and interconnected ecosystem that has geographically diverse routes and consists of multiple tiers of outsourcing. Entities within the supply chain ecosystem depend on each other to develop, integrate and use information and communications technology products and services. The global ICT supply chain could allow adversaries to disrupt the operation of enterprises, increasing risks for end-user organizations.
Boyens says NIST stakeholders identify malicious insertion of malware, counterfeit products, intellectual property theft and poor technology development as the most significant supply chain risks they face.
Because adversaries use malware installed inside the organizational perimeter to identify targets of opportunity, NIST, in the guidance, advises enterprises to perform malware-focused internal reconnaissance.
The guidance points out that criminal groups seek to acquire and sell counterfeit ICT components for monetary gain. Specifically, organized crime groups seek disposed units, purchase overstock items and acquire blueprints to obtain ICT components that they can sell through various gray market resellers to acquirers.
Regarding intellectual property theft, the guidance addresses ways to prevent disgruntled insiders from selling or transferring government, military and trade secrets, such as software code, blueprints or documentation, to competitors or foreign intelligence agencies for a number of reasons, including monetary gain.
Supply Chain Risks
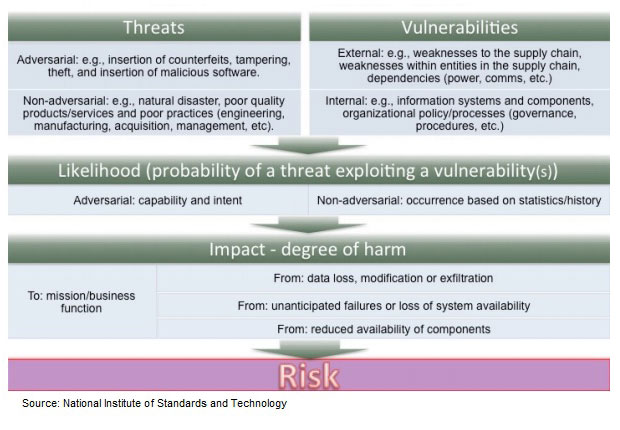
With reports that governments, including the United States and China, tamper with IT wares to provide backdoor access to sensitive systems, Boyens says the revised NIST guidance furnishes a variety of practices organizations can adopt to resist and detect tampering (see U.S.-China Fisticuffs Over Cyberspying) . He says these practices include using tamper-proof technologies, understanding and identifying who uses the information system and components as they traverse the supply chain and throughout their life cycle and applying a variety of testing methods to acquired products.
Boyens says a common misconception is that supply chain risks are too difficult or expensive to manage. "Many common practices used in traditional supply chain risk management, quality assurance or information security, can help mitigate ICT supply chain risks," he says.
Comments on the draft should be submitted by July 18 to SCRM-NIST.gov with "Comments NIST SP 800-161" in the subject line.