New Snowden Leak Details NSA Collection Program
Meanwhile, Papers from Earlier Snowden Disclosure Declassified
As the Obama administration declassified documents outlining a once-secret intelligence-gathering program outted by Edward Snowden, the Guardian newspaper published details about another top-secret National Security Agency program that it says allows analysts, without authorization, to collect e-mails, online chats and browsing histories of millions of individuals.
See Also: Mastering Data Dilemmas: Navigating Privacy, Localization and Sovereignty
Like earlier revelations about NSA programs [see Who's to Blame at NSA for Snowden Leak?], the latest disclosure was based on documents that Snowden downloaded when he worked as a contractor with top-secret clearance at the NSA.
According to the July 31 Guardian report, the NSA touts in training materials that the program, called XKeyscore, is its "widest-reaching" system for developing intelligence from the Internet.
The Guardian report suggests XKeyscore could be used by a wide-range of analysts, quoting Snowden in a June 10 interview as saying, "I, sitting at my desk, [could] wiretap anyone, from you and your accountant, to a federal judge or even the president if I had a personal e-mail."
White House, NSA React
White House Press Secretary Jay Carney, at a July 31 press briefing, said some of the claims made in the Guardian article aren't true. "As we explained, and the intelligence community has explained, allegations of widespread, unchecked analyst access to NSA collection data are false," Carney said.
"Access to all of NSA's analytic tools is limited to only those personnel who require access for their assigned tasks," he said. "And there are multiple technical manual and supervisory checks and balances within the system to prevent those who don't have access from achieving that access."
In an NSA statement, the agency maintains XKeyscore is used as part of the its lawful foreign signals intelligence collection system. "By the nature of NSA's mission, which is the collection of foreign intelligence, all of our analytic tools are aimed at information we collect pursuant to lawful authority to respond to foreign intelligence requirements - nothing more," the statement says.
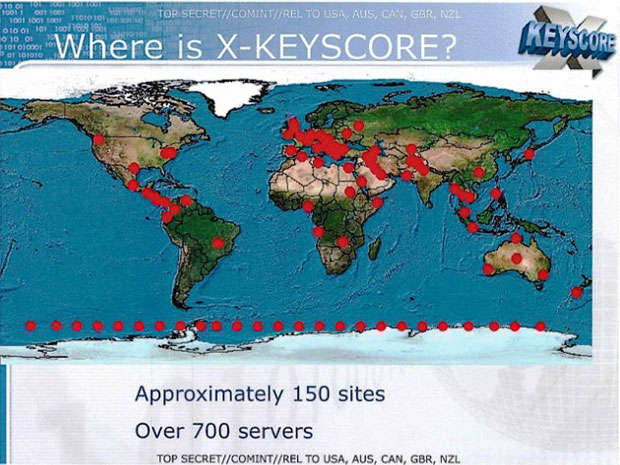
NSA says its tools have stringent oversight and compliance mechanisms bult in at several levels. "Not every analyst can perform every function, and no analyst can operate freely," the NSA says. "Every search by an NSA analyst is fully auditable, to ensure that they are proper and within the law."The Guardian published a 32-page NSA PowerPoint presentation on XKeyscore, which includes a map that shows 150 network sites around the world where the NSA collects information [see map at the end of this story].
According to one of the slides, "A large amount of time spent on the web is performing actions that are anonymous. We can use this traffic to detect anomalies, which can lead us to intelligence by itself."
Detecting Previously Unknown Activity
One slide claims that more than 300 terrorist were captured using intelligence generated from XKeyscore. How? That could be answered in another slide: "Scanning content for the user ID rather than performing strong selection means we may detect activity for applications we previously had no idea about."
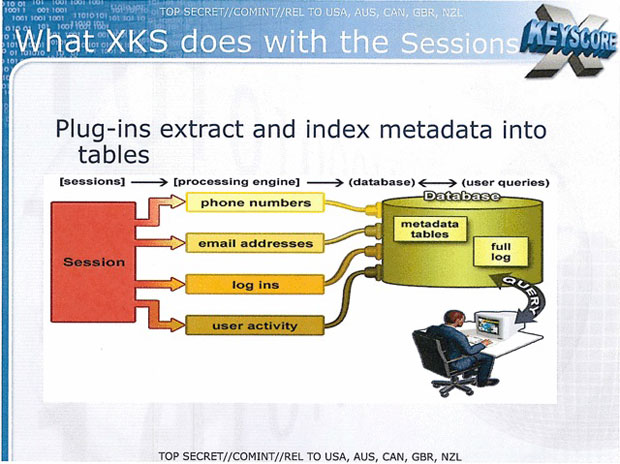
The slideshow also shows how an XKeyscore sessions works. One slide shows the flow of information as plug-ins extract and index metadata into tables.
Administration Declassifies Documents
In a move the government says brings more transparency to its data-collection programs, the National Director of Intelligence James Clapper ordered the declassification of three documents that furnish additional insight into the NSA program, leaked by Snowden, that collected metadata on telephone calls made by most Americans in order to track down terrorists. That program was the subject of a Senate hearing on July 31 [see Who's to Blame at NSA for Snowden Leak?].
declassified documents revealed compliance problems the NSA experienced in 2009 with the intelligence-gathering program:
"A number of technical compliance problems and human implementation errors in these two bulk collection programs were discovered as a result of Department of Justice reviews and internal NSA oversight. However, neither DoJ (Justice Department), NSA nor the FISA court has found any intentional or bad-faith violations."
The document says the incidents were reported to the secret court, established under provisions of the Foreign Intelligence Surveillance Act, which ordered appropriate remedial action.