Breach Notification , Cybercrime , Finance & Banking
New Data Leaks Add to Australia's Data Security Reckoning
MyDeal Data Appears Online; Vinomofo Discloses Breach; Optus Fallout Continues
Personal data from MyDeal.com.au, a marketplace owned by Australia's largest grocery chain, Woolworths Group, has appeared for sale on a data leak forum. Later on Tuesday, it was marked as sold.
That comes as wine retailer Vinomofo disclosed a breach on Monday and as the Optus telecommunications breach continues to fuel concerns over data security and if Australian data protection laws are adequate.
The 500-line sample data from MyDeal appears to be legitimate, says Troy Hunt, a data breach expert who created Have I Been Pwned, a service that notifies people when their email address has appeared in a new data breach.
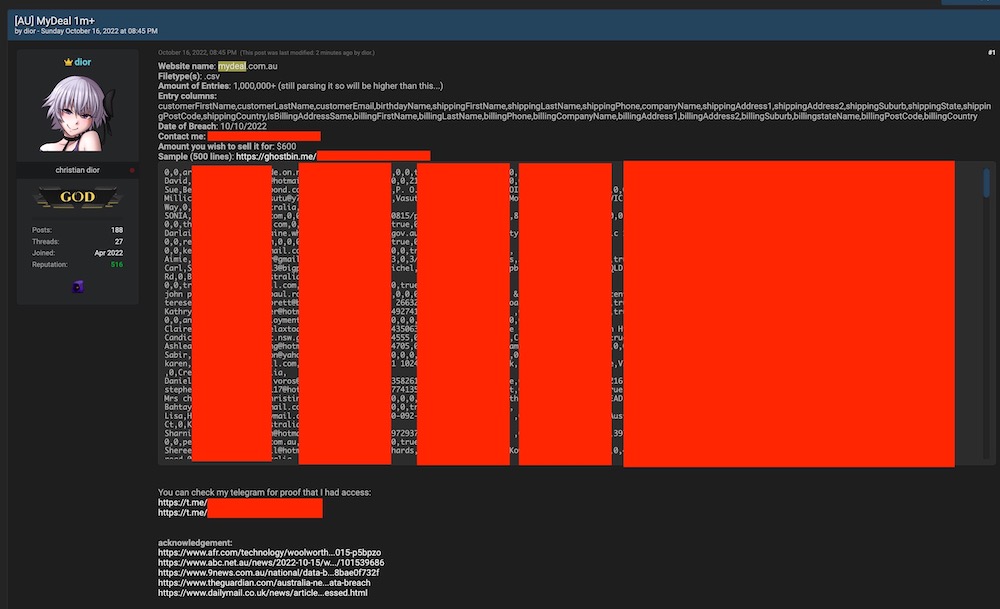
MyDeal's website will reveal if an email address is already in its system when trying to register a new account, Hunt says. Email addresses in the sample are registered with MyDeal.
An attacker who goes by the nickname "Christian Dior" was selling the entire MyDeal data set for $600. Later on Tuesday, Dior marked the data as "sold" and wrote on Telegram, "MyDeal DB has been sold - won't be selling any more copies."
Woolworths Group, which owns MyDeal, disclosed on Friday that an attacker had gained access to its customer relationship management system using a compromised login credential. CRM software is widely used among organizations to store and process user data.
Dior confirmed to Information Security Media Group that's how he gained access to MyDeal. "Most of the access was gained from password reuse. They [MyDeal] didn't even notice until we started [f***ing] with customers' support tickets."
Woolworths said 2.2 million people are affected. For 1.2 million people, only their email address was exposed. For the rest, names, email addresses, phone numbers, delivery addresses and sometimes birthdates were exposed. Woolworths said MyDeal does not store passport details, driver's license numbers or payment information.
Dior told ISMG he sent an email to around a dozen people at MyDeal asking for $20,000 in exchange for deleting the data. Dior says he's not sure if MyDeal responded, as he lost access to MyDeal's systems a day later "while I was high on mushrooms." Cybercriminals often try to extort organizations after stealing sensitive data with the promise that data will be deleted.
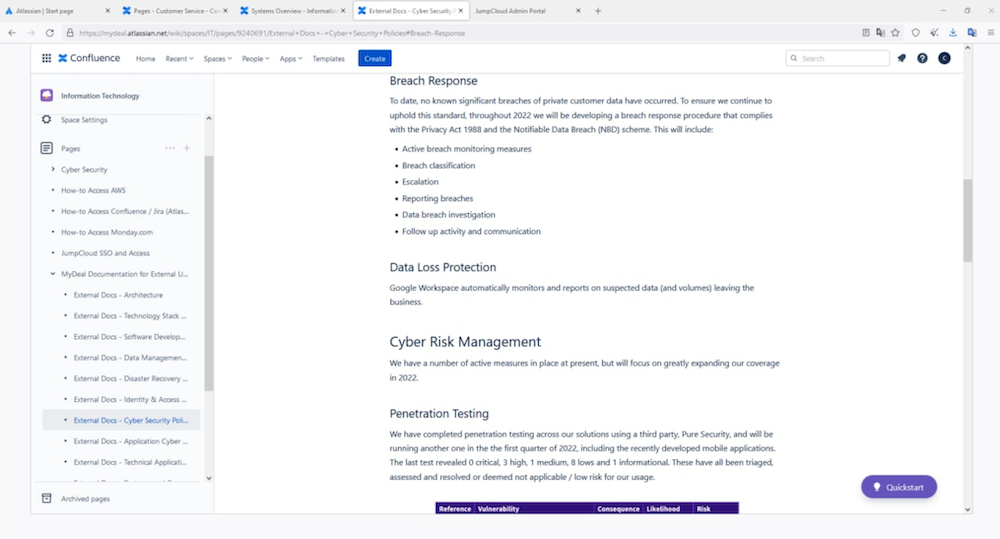
Dior published a screenshot that indicated access to MyDeal's Atlassian Confluence server, which is a collaboration tool. The URL visible in the screenshot is mydeal.atlassian[dot]net. The screenshot shows a page open in MyDeal's internal wiki that shows its cybersecurity and breach response policies.
Dior shared screenshots with ISMG that have not publicly been released, including a network infrastructure map. A screenshot that is too sensitive to post features a complex diagram showing how MyDeal's infrastructure is connected, from SaaS services to e-commerce systems to payments to development systems to the CRM system that was hacked.
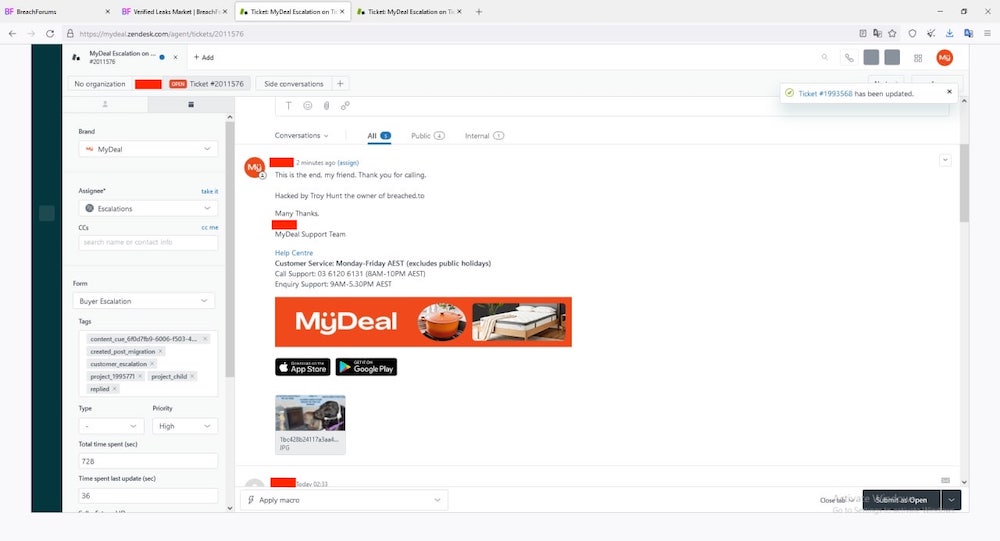
Dior said he accessed source code in MyDeal's Bitbucket, which is a software platform for managing code development. He was also inside MyDeal's Zendesk customer support system.
Australia's Privacy Reckoning
The MyDeal development comes as Australian wine retailer Vinomofo began notifying its customers around Monday of a data breach involving its customer database. According to a notification, Vinomofo says someone unlawfully accessed the database when it was connected to a testing platform.
Hunt says organizations often make the mistake of using real data within test environments, which can lead to trouble if there is a compromise.
Vinomofo didn't say how many people are affected. It maintained the risk is low but that the compromised data includes name, gender, birthdate, email address and phone number. It says it reported the breach to the Australian Cyber Security Center and the Office of the Australian Information Commissioner.
Adding to the mix was an announcement on Monday by health insurer Medibank saying it had "contained" malicious activity that likely would have led to a ransomware attack. Medibank said it has so far found no indication that customer data was taken from its network (see: Australian Insurer Medibank Says Incident Was Ransomware).
Although significant, the MyDeal and Vinomofo breaches follow what was perhaps the greatest privacy breach in Australian history, which involved Optus, the country's second-largest telecommunications company.
An attacker who went by the nickname "Optusdata" accessed an internet-facing application programming interface that did not require authentication. It was connected to Optus' customer database. The person subsequently downloaded around 10 million current and former customer records going back to 2017 (see: Optus Under $1 Million Extortion Threat in Data Breach).
The person then tried to extort Optus for US$1 million. Two days later, Optusdata withdrew the demand, apologized for releasing data samples affecting 10,200 people and said the data would no longer be sold. Optus told ISMG the same day that it had not paid a ransom (see: Optus Attacker Halts AU$1.5 Million Extortion Attempt).
The Optus data breach was particularly sensitive. Around 2.8 million of the 10 million people had either their passport number or driver's license number and driver's license card number or Medicare card number revealed. Medicare is Australia's national insurance plan. That data was leaked in addition to name, address, phone number and birthdate.
The incident caused fury among current and former Optus customers and unprecedented action from the government to blunt potential fraud as a result of the breach.
Lawmakers promptly amended the Telecommunications Regulations 2021 law to allow the sharing of information related to the Optus breach with financial institutions.
"These changes will reduce the impact of this data breach on Optus customers and enable financial institutions and government agencies to implement enhanced safeguards and monitoring, according to an advisory on Friday from the Australian Cyber and Infrastructure Security Center.
The government also created the Commonwealth Credential Protection Register, which is intended to stop the fraudulent use of ID information. It added 100,000 compromised passport numbers exposed in the Optus breach to the register. Those numbers can now no longer be used with the Document Verification Service.
The DVS is a government service that lets organizations verify whether certain identity data is correct. It can be used to check the veracity of 14 documents, including birth certificates, driver's licenses and passport numbers. When entities registered with DVS request a check, DVS returns only a "yes" or "no" answer as to whether a document is correct.
In what may be a world-first, the Australian government also pressed Optus to reimburse people for fees incurred related to replacing their passports and driver's licenses. For passports, those eligible must pay for the replacement upfront and then apply for reimbursement from Optus.
Optus will apply a credit to customers' bills to cover the cost of replacement driver's licenses, depending on the state or territory. Some states and territories are initially waiving the cost of replacement due to the breach. Optus provides more information here.

The government's pressure on Optus to reimburse those affected by the breach is striking and could send a message of increasing intolerance for data breaches and a desire to increase the immediate costs for those responsible for breaches. Consumers often wait years to see any compensation from class action lawsuits as a result of a breach.
The government is also considering strengthening privacy laws to create higher penalties for those found to have violated the country's Privacy Act. Each violation can merit a fine up to AU$2.2 million - or US$1.38 million, but the Minster for Home Affairs and Cyber Security, Clare O'Neil, has said that figure is "totally inappropriate."
There are several investigations underway into the Optus breach, including those by the Office of the Australian Information Commissioner and the Australian Communications and Media Authority.



















