Fraud Management & Cybercrime , Governance & Risk Management , Next-Generation Technologies & Secure Development
Neutrino Exploit Kit: No Signs of Life
Poor Profits May Have Driven Developers Out of Exploit Kit Business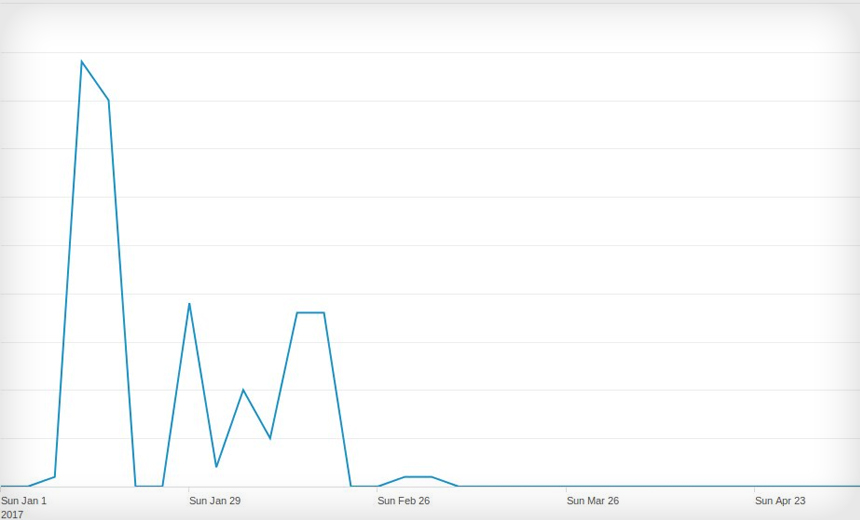
Good news: The Neutrino exploit kit may be dead.
See Also: New OnDemand | Cyber Risk Graph: Solving the Data Problem of Proactive Security
In recent months, security researchers have noticed that the attacks tied to the exploit kit - once big and bad - appears to have gone dormant.
"R.I.P. Neutrino exploit kit. We'll miss you (not)," say researchers at security firm F-Secure via Twitter, noting that they have seen no Neutrino-related activity for nearly three months.
The French anti-malware researcher known as Kafeine also reported Wednesday that "after eight months of 'private mode' activity, it seems Neutrino waves are now dead flat" - since April 10.
From Cybercrime Hero to Zero
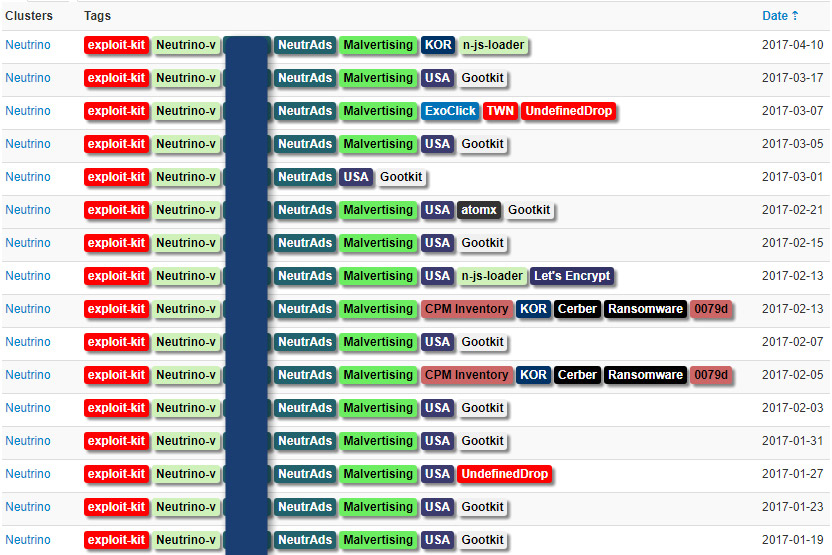
That's significant, because Neutrino at one time ranked as one of the world's most popular exploit kits. Also known as exploit packs, these tools enable anyone - no coding experience required - to run large-scale campaigns designed to infect massive quantities of PCs with malware, turning them into "zombie" nodes in a botnet.
Exploits kits typically do this by infecting legitimate websites with malicious code, then launching drive-by attacks against website visitors, probing their systems for known weaknesses. "Exploit kits ... automate the exploitation of client-side vulnerabilities, often targeting browsers and applications that a website can invoke through the browser," according to a Neutrino teardown published by security firm Malwarebytes. "Known exploit targets have been vulnerabilities in Adobe Reader, Java Runtime Environment, and Adobe Flash Player."
Some exploit kits are private and used exclusively by a single cybercrime gang - often tied to an organized crime syndicate. Others get monetized by developers who rent them out to other attackers, either as a way of infecting systems, or else by using already infected systems on demand, to send large amounts of spam, distribute malware or launch distributed denial-of-service attacks against customer-designated targets.
In the dog-eat-dog cybercrime ecosystem, however, it appears that Neutrino's developer lost market share to rivals.
"I spoke with the [developer] a long while ago he explained it was no longer profitable," one U.S.-based malware researcher says via Twitter.
Neutrino Was Big in 2016

From July 2016 to September 2016, Neutrino dominated the exploit kit scene and appeared lucrative. For example, researchers at Cisco Talos also reported that Neutrino was so popular that its authors had raised its rental price to $7,000 per month, likely at least in partial response to the sudden disappearance of Angler, one of its chief rivals.
As of the next month, Check Point reported that 11 percent of all payments by victims of Cerber ransomware could be traced to an initial infection caused by a Neutrino exploit kit.
In September 2016, however, Neutrino's owners suddenly announced that they would henceforth operate solely in "private mode," for a small, selected group of clients. "We are closed. No new rents, no extends more," Neutrino's authors wrote via Jabber messages sent to their existing clients, Kafeine reported.
The move may have been a reaction to Cisco's security and research group Talos and domain registrar GoDaddy successfully disrupting two large, global malvertising campaigns being launched using Neutrino the same month.
By October 2016, meanwhile, Kafeine reported a dramatic decline in Neutrino-related activity, reporting that there only appeared to be two active campaigns tied to the exploit kit.
But Kafeine told anti-malware site Bleeping Computer Wednesday that Neutrino continued, and in January was testing two new exploits for the Microsoft Edge browser.
Confusingly, Neutrino was sometimes used to distributed Neutrino Bot, aka Kasidet, which can launch DDoS attacks, record keystrokes and install more malware, according to Malwarebytes. Neutrino was seen distributing Neutrino Bot at the end of last year and beginning of this one.
By April, however, Neutrino - the exploit kit - appeared to have disappeared completely.
No Dearth of Alternatives
To be clear, however, there are numerous other exploit kit options, as have been tracked, for example, by the Execute Malware blog.
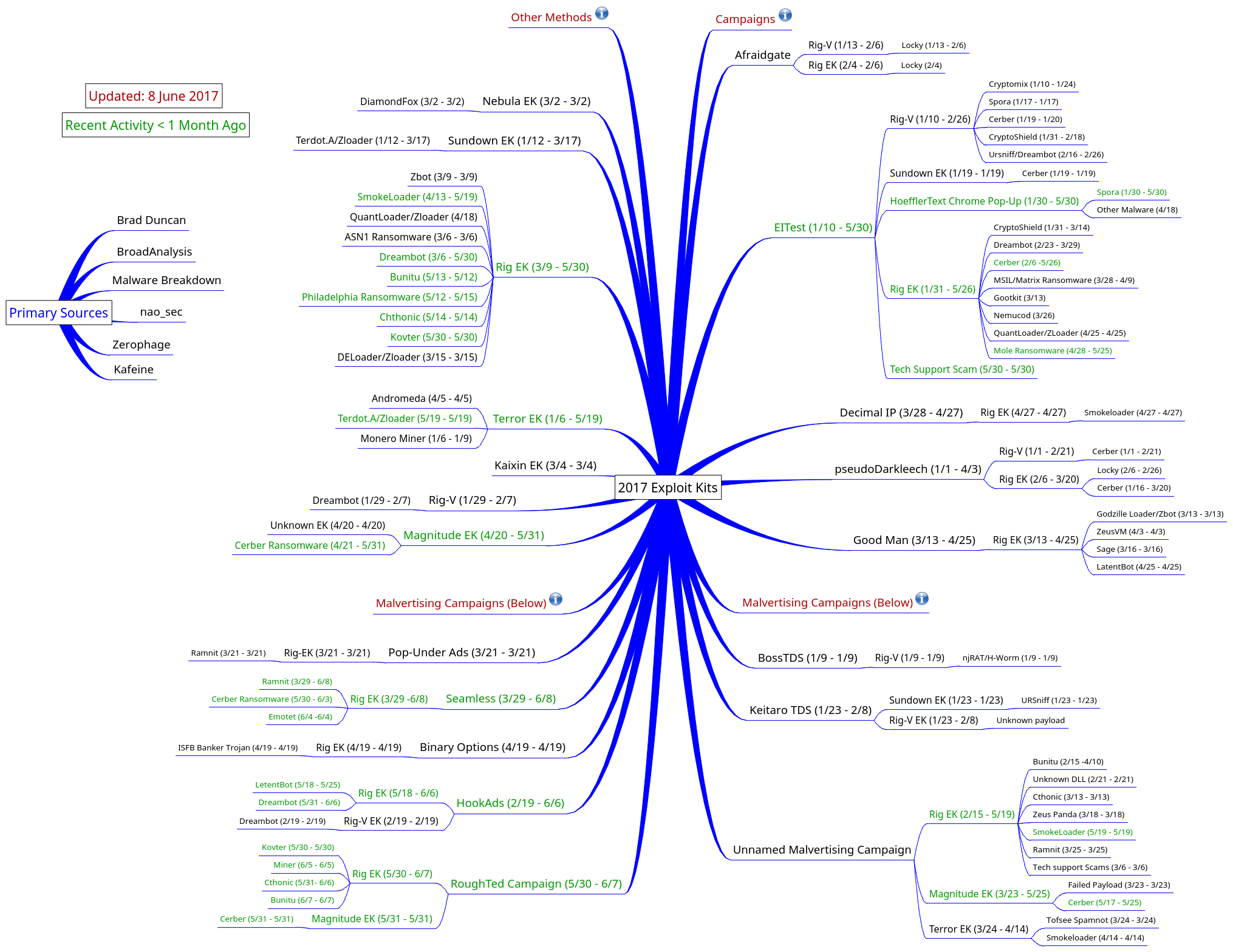
Some security experts say Neutrino has been supplanted by RIG, an exploit kit that has been its chief rival since 2016, and which has since become the dominant player.
Meanwhile, is Neutrino finished, or just resting?
Updated to note the difference between Neutrino and Neutrino Bot.






















