Governance & Risk Management , IT Risk Management , Patch Management
Microsoft Exchange: 355,000 Servers Lack Critical Patch
Fix Released in February Only Installed on 18 Percent of Servers, Rapid7 Warns
Patch or perish alert: Less than than 20 percent of all Microsoft Exchange servers have received a fix for a serious flaw Microsoft first disclosed nearly two months ago, security firm Rapid7 warns.
See Also: Finding and Managing the Risk in your IT Estate: A Comprehensive Overview
"As of March 24, there were over 350,000 Exchange servers exposing a version of the software that has this vulnerability," writes Tom Sellers, a senior manager at Boston-based Rapid7 Labs, in a blog post.
The vulnerability could allow a remote attacker "to turn any stolen Exchange user account into a complete system compromise," he says. "In many implementations, this could be used to completely compromise the entire Exchange environment - including all email - and potentially all of Active Directory" (see: Why Hackers Abuse Active Directory).
Microsoft addressed the remote-code-execution vulnerability - designated CVE-2020-0688 - via security updates it released on Feb. 11 for all supported versions of Microsoft Exchange. At least at that point, the flaw didn't appear to have been targeted in the wild, the company said. The flaw was reported to Microsoft by an anonymous researcher via Trend Micro's Zero Day Initiative.
"A remote-code-execution vulnerability exists in Microsoft Exchange Server when the server fails to properly create unique keys at install time," Microsoft said in its security alert. "Knowledge of the validation key allows an authenticated user with a mailbox to pass arbitrary objects to be deserialized by the web application, which runs as SYSTEM. The security update addresses the vulnerability by correcting how Microsoft Exchange creates the keys during install."
Security Updates Include Patch
To fix the flaw, Microsoft pushed security updates for four base versions of Exchange:
- Exchange Server 2010 service pack 3 update rollup 30;
- Exchange Server 2013 cumulative update 23;
- Exchange Server 2016 cumulative update 14;
- Exchange Server 2016 cumulative update 15;
- Exchange Server 2019 cumulative update 3;
- Exchange Server 2019 cumulative update 4.
But the vast majority of these servers remain unpatched, according to a survey conducted by Project Sonar, Rapid7's in-house internet scanning project (see: Is COVID-19 Driving a Surge in Unsafe Remote Connectivity?).
"On March 24, we used Project Sonar to survey the internet for publicly facing Exchange Outlook Web App - OWA - services," Sellers says. "What we found was that at least 357,629 (82.5 percent) of the 433,464 Exchange servers we observed were known to be vulnerable."
Subsequently, Sellers added a caveat that 35,000 fewer servers might be vulnerable, owing to Microsoft's fix for Exchange 2010 not updating the visible build information, meaning that scans alone could not tell if an Exchange 2010 system had been updated. Instead, organizations will need to manually verify that every such system has the update. Sellers says they should do the same for all Exchange 2013 and newer systems, noting that the build number alone should indicate if the relevant update is in place.
Check for Compromise
Rapid7 also recommends all organizations that use Exchange search for any signs that they have been compromised via this flaw.
"The exploit code that we tested with left log artifacts in the Windows Event Log and the IIS [Internet Information Services] logs on both patched and unpatched servers," Sellers says, noting that the log error message will also name the compromised user account.
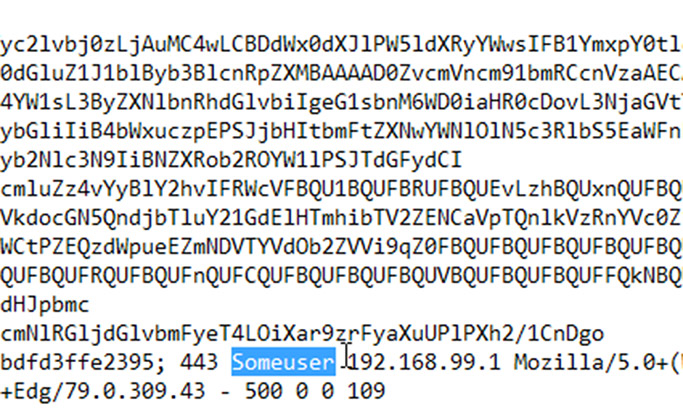
Because the attack requires a valid Exchange user account to succeed, "any user accounts seen in these exploitation attempts should be considered compromised," Sellers says.
But Wait, There's More
Unfortunately, the Project Sonar scans revealed more widespread problems than a lack of CVE-2020-0688 patching. Notably, Rapid7 researchers found 31,000 Exchange 2010 servers online that had received no updates since 2012, as well as 800 Exchange 2010 servers that have never been updated. It also saw 10,371 Exchange 2007 servers.
"In addition to the high numbers of servers that are missing multiple updates, there is a concerning number of Exchange 2007 and 2010 servers," Sellers says, although he notes that Exchange 2007 is not vulnerable to CVE-2020-0688. Even so, the unsupported operating system long ago stopped receiving security updates, and now has a raft of critical flaws that attackers could exploit. "Exchange 2007 transitioned to 'end of support' status nearly three years ago, on April 11, 2017," he says. "No security updates, bug fixes, time zone updates, etc., are provided after that date."
Exchange 2010 was scheduled to reach end of support on Jan. 14, although that's now been postponed until Oct. 13, 2020. "There are over 166,000 of these servers connected to the internet," Sellers says. "That’s a staggering number of enterprise-class mail systems that will be unsupported in a few months."





















