Governance & Risk Management , IT Risk Management , Next-Generation Technologies & Secure Development
Linux Botnet Disguises Itself as Apache Server
Researchers: Operators of Stantinko Botnet Putting More Emphasis on Stealth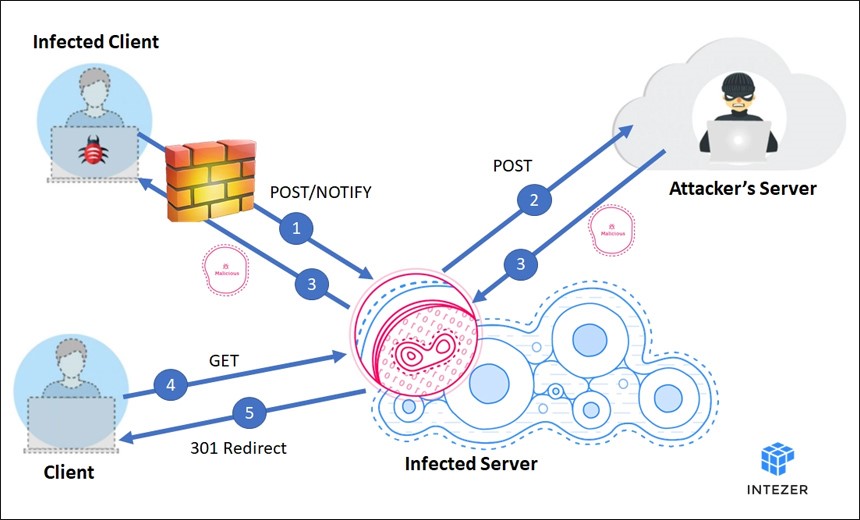
The latest Linux version of the Stantinko botnet is designed to disguise the malware as an Apache server to help better avoid security tools and remain hidden, according to Intezer Labs.
See Also: Bank on Seeing More Targeted Attacks on Financial Services
The botnet, which has been in operation since at least 2012, was created to infect Windows devices to increase its malicious infrastructure. In 2017, however, research firm ESET reported that a Linux version of the malware had been created.
The Stantinko botnet primarily mines for cryptocurrency or spreads other types of malware, such as adware, researchers say.
In the latest version of Stantinko that the Intezer Labs researchers found, the botnet’s operators appear to have placed more emphasis on avoiding security tools. The operators switched the proxy version file name to "httpd," which is normally associated with the Apache Hypertext Transfer Protocol Server, a commonly used program on Linux servers, according to the report.
"We believe this malware is part of a broader campaign that takes advantage of compromised Linux servers," the Intezer Labs researchers note.
Updated Version
The latest version of the Stantinko botnet, labeled version 2.17, is a significant upgrade from the Linux version 1.2 found in 2017 by the ESET researchers. The botnet, however, still targets vulnerable devices, primarily in Russia, Ukraine, Belarus and Kazakhstan.
Intezer Labs notes that the malware uses a configuration file that is dropped on the targeted devices to plant the malicious code.
"The configuration file contains the command-and-control IP address together with other parameters," according to the report. "In the old version (1.2), the command-and-control is hardcoded in the binary, making it easier to block the campaign's traffic once the binary is detected."
Linux Targeted
Stantinko is one of several botnets targeting Linux devices, usually to mine for cryptocurrency. Another example is the "InterPlanetary Storm" botnet that infects Windows, Linux, Mac and Android devices, according to Barracuda Networks (see: 'InterPlanetary Storm' Botnet Infecting Mac, Android Devices).
In addition to botnets, researchers have found ransomware that targets both Linux and Windows devices.
Earlier this month, researchers at Kaspersky released a report on RansomEXX, crypto-locking malware that was developed for Windows but was then ported over to Linux to attack a much larger array of devices (see: RansomEXX Ransomware Can Now Target Linux Systems).




















