HIPAA/HITECH , Incident & Breach Response , Managed Detection & Response (MDR)
Lessons from 2015's Top Health Data Breaches
What Preventive Steps Do Healthcare Organizations Need to Take in 2016?
Just how big an impact did hacker attacks have on the healthcare sector in 2015?
See Also: Embracing Digital Risk Protection: Take Your Threat Intelligence to the Next Level
Nine of the top 10 incidents in 2015 on the Department of Health and Human Services' "wall of shame" tally of major breaches involved hacker attacks, a huge shift from previous years, when hacker attacks were relatively rare.
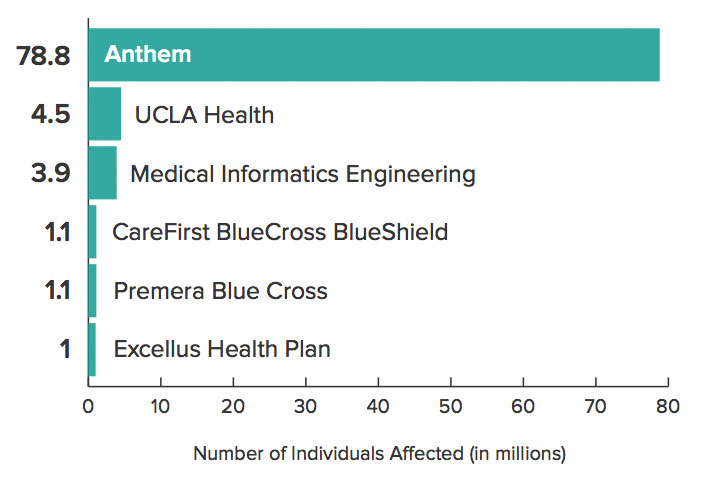
The biggest health data breach of 2015 - the cyberattack on health insurer Anthem Inc. - affected nearly 79 million individuals, making it, by far, the biggest healthcare breach on the list since its inception in late 2009. And the top six hacker attacks affected a combined total of 90 million individuals.
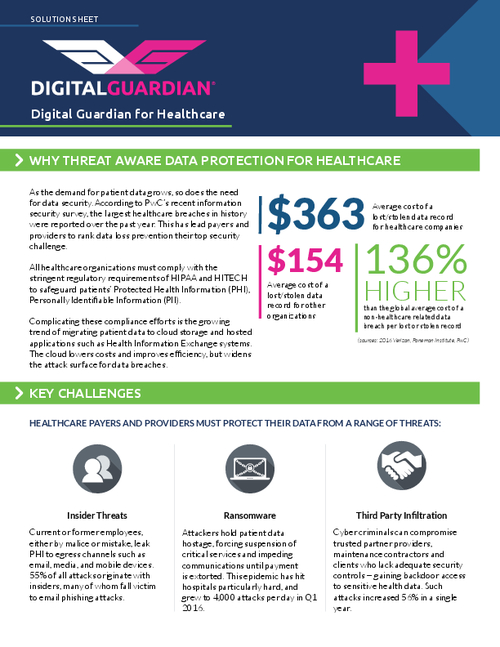
Top Breaches of 2015
While hacker attacks account for less than 11 percent of the incidents listed on the HHS tally so far, they account for 75 percent of breach victims. Some 56 hacker breaches added to the tally in 2015, affecting a total of nearly 112 million individuals.
And a Dec. 31 snapshot of the wall of shame shows 1,425 breaches impacting a total of more than 154 million individuals. That's more than three times the number of victims affected by health data breaches as of one year ago - a result of the massive hacker attacks.
Lessons Learned
So what are the top lessons to be learned from the epidemic of mega-hacks in 2015?
"Healthcare organizations need to become more mature in their security posture and be a lot more proactive about protecting data," says Jay Trinckes, senior practice lead for healthcare and life sciences at the consulting firm Coalfire. "We see many small organizations basically doing the bare minimum when it comes to security, such as 'checking the box' type activities for HIPAA compliance. But it's interesting to note that the top breaches are happening to the large covered entities believed to have a higher security maturity level."
The hacker attacks point to the need for continual risk analysis, says privacy attorney Kirk Nahra of the law firm Wiley Rein LLP.
"These 'cyber' risks really aren't new, but the form they take keeps evolving, and other risks change as well," he says. "Security protection - whether as a regulatory requirement or just as smart business - cannot be stagnant; it must be reviewed, assessed and improved almost constantly."
Need for Penetration Testing
The cyberattacks in 2015 also point to the need to conduct more rigorous and thorough penetration testing on a regular basis, Trinckes says.
Healthcare entities, as well as their business associates, also need to comply with industry standards that go far beyond HIPAA Security Rule, he stresses. The wall of shame indicates that business associates have been involved in about 20 percent of all breaches.
"A trend we've noticed is that business associates are realizing the benefits of assessing risk against many compliance standards/frameworks - including HITRUST, SOC, ISO, PCI - as a competitive differentiator to increase revenue," Trinckes says. "They're using this level of thoroughness as a marketing tool to demonstrate their high bar of data protection and to meet customer demands. This is also particularly evident with cloud service providers that serve the healthcare industry."
Other Steps to Take
Another important step that healthcare entities and BAs can take to bolster breach prevention and detection in 2016 is to improve their communication, Nahra says.
When it comes to BA's alerting the organizations they serve about breaches, Nahra says, "make sure that reporting channels are clear - that people know where to go as soon as possible. Also make sure that reporting suspicions [about breaches] is incredibly important. People need to know that they should report, even if it turns out to be nothing, and that they shouldn't try to 'figure things out' before reporting. The faster that these problems can be stopped, the better for everyone." p>
Organizations in the healthcare sector also should consider performing social engineering tests in an attempt to prevent falling victim to phishing attacks, which are frequently at the center of major hacking incidents, Trinckes says.
"Results of this testing often lead to identifying the need for more effective internal training," he says.
Healthcare organizations are also under pressure to bolster their breach detection and incident response plans, he adds. They should consider implementing sophisticated intrusion detection and prevention solutions along with log monitoring systems, he suggests. But they must ensure they have "the resources to maintain and monitor these solutions on a continuous basis."
Hospitals and others also need to be mindful about dealing with the potential cyber risks posed by medical devices, he says.
"We've also seen many medical device manufacturers seeking to assess their solutions for vulnerabilities and malware," he notes
Looking Ahead
Looking ahead to 2016, Nahra predicts the cyberattack epidemic will endure. "These breaches will continue on a large scale, and will continue to be in the news because they have a long tail - both in cleaning up problems and in subsequent enforcement, if any, which can occur several years later," he says.
Trinckes predicts that hacking incidents will continue to multiply "as healthcare providers face ever increasing issues with the 'Internet of Things' world.
The increased value of protected health information and personally identifiable information in the black market underground for use in such crimes as identity theft and fraud is fueling the surge in breaches, he adds.
"We will see more healthcare organizations pursuing the purchase of cyber insurance coverage, and these insurers will require these organizations to demonstrate a high level of data security practices, along with having a comprehensive, proactive information security program," he predicts.