3rd Party Risk Management , Breach Notification , Business Continuity Management / Disaster Recovery
Kaseya Attack: REvil Offers $70 Million 'Universal Decryptor'
Yet Another Ransomware Attack Targets Managed Service Providers to Maximize Profits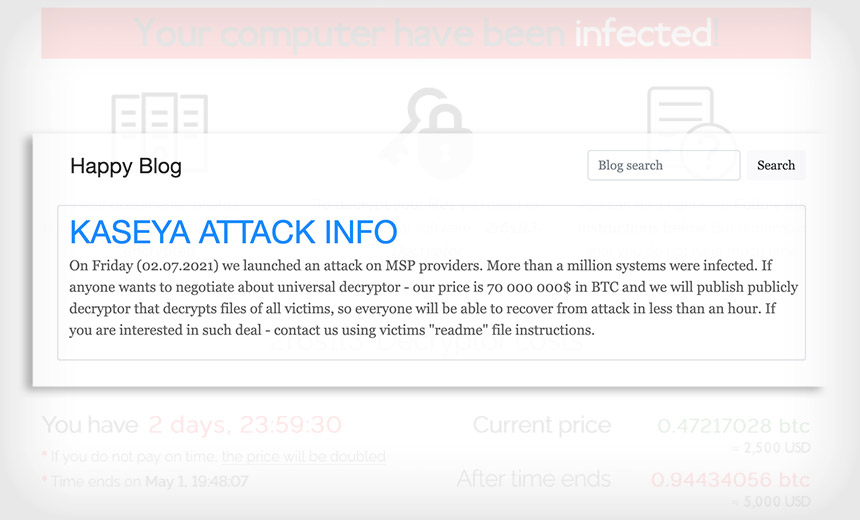
The REvil ransomware operation behind the massive attack centering on Kaseya, which develops software used by managed service providers, has offered to decrypt all victims for $70 million in bitcoins.
See Also: Cybersecurity in Public Sector: 5 Insights You Need to Know
Whether or not REvil would honor that promise or allow the amount to be negotiated down, or whether a coalition of victims will cobble together those funds to potentially pay the ransomware-wielding attackers, remains to be seen. But some victims have reportedly already been negotiating individually with the attackers.
"On Friday, we launched an attack on MSP providers," REvil states in a message posted on Monday to its "Happy Blog" data leak site. "More than a million systems were infected. If anyone wants to negotiate about universal decryptor - our price is $70 million in bitcoins and we will publish publicly decryptor that decrypts files of all victims, so everyone will be able to recover from attack in less than an hour. If you are interested in such deal - contact us."
Remote management software provider Kaseya has 36,000 MSP customers worldwide, and the attack, which it discovered Friday, led U.S. President Joe Biden to order the launch of a full-scale federal investigation.
Based in Dublin, with U.S. headquarters in Miami, privately held Kaseya, founded in 2000, sells IT remote management software used by hundreds of managed service providers. By attacking Kaseya, REvil was able to substitute ransomware for a legitimate software update issued by Kaseya, thus distributing crypto-locking malware not just to Kaseya's MSP customers, but potentially to all of the endpoints managed by those MSPs.
Kaseya maintains that only "a very small number of on-premises customers" - and no MSPs using its software-as-a-service product - were affected by the attack, although these MSPs could still collectively count hundreds of organizations or more as customers, and thus also potential victims.
Some victims have been negotiating with REvil, Bleeping Computer reports, noting that attackers appear to be demanding $5 million from affected MSPs, and $45,000 per encrypted file type from affected customers of MSPs, and that no data appears to have been stolen.
Given the challenge of negotiating with all of these victims, REvil's $70 million universal decryptor offer might simply be an attempt by the group to maximize its profits for minimal effort.
RaaS Operation
REvil is run as a ransomware-as-a-service operation: A core operations team develops the crypto-locking malware and makes it available to affiliates. In REvil's case, the core team also runs a data leak site where affiliates can name and shame victims and leak samples of stolen data - if any data was stolen - to try and force nonpaying victims to change their mind. Experts say the operators sometimes also assist with negotiations with victims, again to try and get them to pay, and occasionally also launch attacks themselves.
Any time a victim does pay, the responsible affiliate and the operator share in the profits (see: REvil's Ransomware Success Formula: Constant Innovation).
According to recent chatter on cybercrime forums, many REvil affiliates receive 75% of every ransom payment, according to cybersecurity firm Group-IB. But the operation may well give more generous cuts to more highly skilled attackers. And competition between RaaS operations for the best affiliates can be fierce, since more skilled attackers can take down larger targets in pursuit of bigger ransoms, via big game hunting.
Some affiliates specialize in hitting MSPs, which remain a top target for ransomware-wielding attackers, because hitting a single organization can generate dozens or hundreds of MSP victims. Each of these MSPs, in turn, may manage systems used by dozens or hundreds of organizations, each of which may have hundreds or thousands of endpoints.
Repeat Target: Kaseya
The attack against Kaseya is not the first time that a REvil affiliate has targeted IT managed service providers - or perhaps even Kaseya.
"This is not the first time Kaseya has been impacted before," Raj Samani, chief scientist at McAfee, tells Information Security Media Group, referring to a 2019 attack by GandCrab, a now-defunct RaaS operation that appeared to morph into REvil - aka Sodinokibi - around mid-2019.
In that attack, GandCrab-wielding attackers targeted a Kaseya remote monitoring and management tool, leading to at least 1,500 systems managed by an MSP being crypto-locked, and the MSP facing a $2.6 million ransom demand, as DarkReading reported at the time.
"Admittedly this was GandCrab, but remember many of the affiliates from GandCrab moved over to REvil - if anything, I would argue this is more the connection" between the two different Kaseya-targeting attacks, Samani says.
"MSPs and their software have been of interest to REvil/GandCrab from the get-go," says John Fokker, principal engineer and head of cyber investigations for McAfee Advanced Threat Research.
"Given REvil’s operational budget and skillset, it was only a matter of time before something like this could happen," he says. "Which affiliate was responsible for the current attack remains to be seen. However it isn’t uncommon for the REvil admin group to stick their hands in the cookie jar or their affiliates' cookie jar," meaning that the core group of operators may be behind this particular attack, or at least may have taken control after a certain point.
Fokker says REvil's core operators are unusually hands-on. "With the REvil RaaS operation, we have observed the admin group actively attacking victims too, as opposed to other RaaS where the admins only supply the framework," he says. "Subsequently, the REvil admin group also have mingled in negotiations and so on, when an affiliate has caught a big fish."
5 Repeat Tactics
While the Kaseya hit and high dollar figure attached to the universal decryptor offer might seem audacious, in fact every element of this attack has been seen before, including the focus on MSPs.
- Holiday weekend: Attackers love to hit targets on weekends, and especially during holiday weekends, or days such as Christmas Eve, when key personnel may be away, and response times slower.
- MSP focus: While a GandCrab affiliate hit Kaseya in 2019, attackers have also directly targeted MSPs as well. Also in 2019, for example, an attacker - perhaps even the former GandCrab affiliate - hit a single MSP, allowing the attackers to remotely access poorly secured remote administration tools installed by the MSP on the endpoints of up to 22 Texas municipalities, which allowed the attacker to infect the municipalities' systems with REvil ransomware (see: Texas Ransomware Responders Urge Remote Access Lockdown).
- Zero-day flaws: In the attack that came to light on Friday, REvil appears to have exploited zero-day flaws in Kaseya's software - not unlike the attacks seen last December against users of Accellion's File Transfer Appliance. In that campaign, which continued through January, attackers reverse-engineered the software and identified four zero-day flaws, which they used to steal data being stored on numerous FTA devices. Stolen data ended up in the hands of the Clop ransomware operation, which used its data leaks site to extort victims into paying a ransom for a promise that the stolen data would be deleted.
- Malicious update: By targeting a zero-day flaw in Kaseya's software, REvil was able to successfully distribute a malicious file via the RMM used by MSPs to the endpoints managed by those MSPs. In some respects, this also resembles the NotPetya attack, in which Russian government hackers allegedly backdoored a Ukrainian account software vendor's software, using it to push destructive malware to every endpoint running the software.
- Supply chain attack: REvil's attack on Kaseya focuses on a firm that supplies others, making it not unlike the supply chain attack against security vendor SolarWinds, in which Russian intelligence agents allegedly altered SolarWinds code to potentially give themselves remote access into any environment where it was running.
Kaseya Required Reduced Security to Run
Another potential commonality between SolarWinds and Kaseya could be the age of each one's code base. One criticism of SolarWinds sounded by multiple security experts, for example, is that a once-innovative vendor of security products had been coasting, with no major updates in recent years to revamp an aging code base. In the wake of the attack against FTA users, meanwhile, Accellion announced that it would no longer support the software, which was nearly 20 years old. It urged holdouts to move to more modern software, as it had been doing prior to the attack.
"What I think we are learning is that the 5-, 10-, 15-year-old code in products is just not up to the attacks we are seeing perpetrated by malicious actors," says Ian Thornton-Trump, CISO of threat intelligence and incident response services firm Cyjax.
Thornton-Trump says multiple pieces of evidence suggest the same criticism could be applied to Kaseya, for which multiple serious flaws have come to light in its software in recent years.
The company also made questionable security choices, such as requiring that many of the directories that its software installs on systems, as well as various applications, be excluded from antivirus and firewall checks. Accordingly, if those apps started misbehaving - as happened during the REvil attack - then organizations' existing security defenses may have been configured in such a way, per Kaseya's instructions, that they would not have flagged the bad behavior.
Dear vendors. These kind of recommendations for your product in 2021 are just unacceptable. KTB https://t.co/t9Oxvo1RZz
— Ian Thornton-Trump CD (@phat_hobbit) July 3, 2021
"It’s untenable to ask customers to reduce security to accommodate software products in this day and age," Thornton-Trump tells ISMG. Notably, the antivirus exclusion document "indicates the company was not interested in putting in the effort to accommodate the level of security the modern threat landscape requires. Disabling antivirus and/or having to turn your firewall into Swiss cheese is just not a viable approach, in this day and age."





















