Cybercrime , Fraud Management & Cybercrime , Fraud Risk Management
Joker's Stash Advertises Second Batch of Indian Card Data
Haul of 460,000 Bank Cards Retailing for $4.2 Million, Group-IB Finds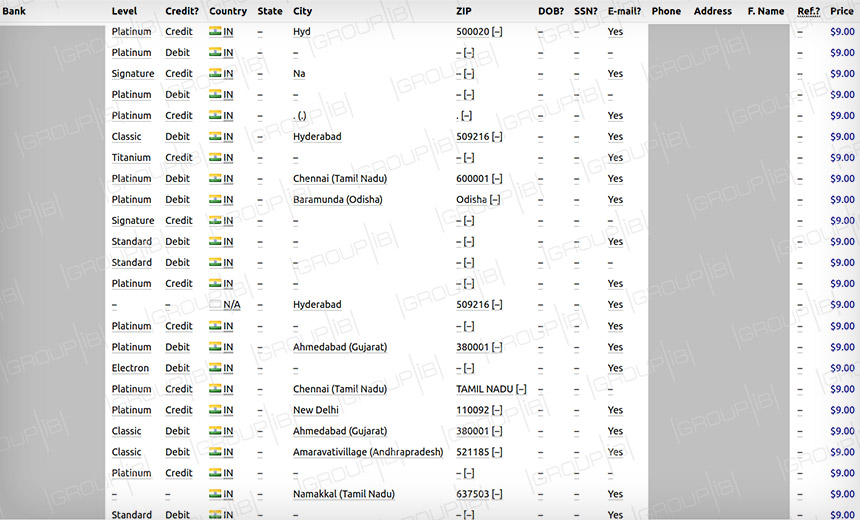
Indian banks are once again facing a fraudster field day as more stolen payment card data appears for sale on cybercrime markets.
See Also: OnDemand | API Protection – The Strategy of Protecting Your APIs
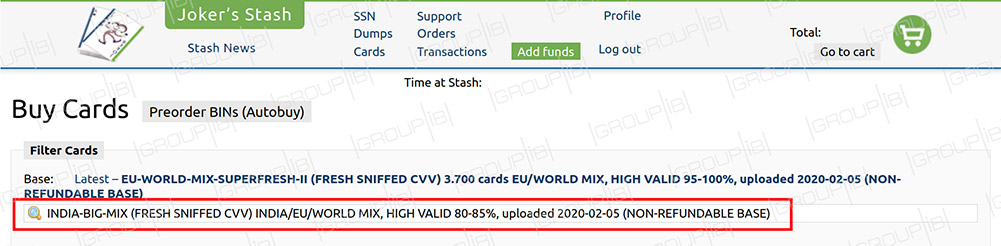
Three months after a massive batch of card data that traced to Indian banks appeared on the notorious Joker's Stash cybercrime marketplace, a fresh "dump" of data is being offered for sale. On Friday, Singapore-based cybersecurity firm Group-IB reported that a new batch of stolen data, named "[CC] India-Big-Mix (fresh sniffed CVV) India/EU/World Mix, High Valid 80-85 percent, uploaded 2020-02-05 (non-refundable base)," first appeared for sale on Wednesday.
The 461,976 payment records include card numbers, expiration dates, CVV/CVC codes and, in some cases, also the full name, email, phone number and mailing address for customers, Group-IB says. Each record retails for $9, making the trove of data valued at $4.2 million.
The origin of the data is unclear, although more than 98 percent of the cards appear to have been issued by Indian banks, Group-IB says, adding that it has alerted Indian's computer emergency response team, CERT-In, about the Joker's Stash listing.
CERT-In didn't immediately respond to a request for comment.
Joker's Stash Keeps Serving Up Dumps
Joker's Stash remains a popular cybercrime "carder" shop that sells personally identifiable information and stolen credit and debit card data. In recent months it's advertised voluminous amounts of stolen payment card data. Last October and November, it was selling dumps that traced to payment cards issued by Turkish banks.
In November 2019, meanwhile, a Joker's Stash "New World Order" dump listed millions of payment cards for sale that researcher Gemini Advisory, which tracks stolen payment card data, said traced to breaches at four U.S. restaurant chains: fast-food chain Krystal, as well as Moe's Southwest Grill, McAlister's Deli and Schlotzsky's, all three of which are owned by Focus Brands.
India a Growing Target
The latest Joker's Stash dump, however, shows the cybercrime marketplace continuing to demonstrate an interest in Indian payment card data, following the October 2019 appearance of an "India-Mix-New" dump on Joker's Stash. That particular haul comprised details on 1.3 million credit and debit card, as Group-IB detailed at the time.
But there's a significant difference between the two Indian card dumps, says Dmitry Shestakov, Group-IB's head of cybercrime research.
Notably, the information being offered for sale last October appeared to have been stolen from cards' magnetic stripes, suggesting that attackers had installed malware on point-of-sale devices, or else somehow exfiltrated card data from an environment with POS terminals, he says.
But the dump that posted this week contains "fullz," which is carder-speak for records that contain full packages of personally identifiable information. In this case, that means not just card numbers but also various types of PII were stolen, which suggests that the data was likely stolen from e-commerce sites that would have been gathering this full array of information. "This type of data is likely to have been compromised online - with the use of phishing, malware or JavaScript sniffers," Shestakov says.
The database contains CC data: card numbers, expiration dates, CVV/CVC codes and some personal info such as cardholders’ full names, as well as their emails, phone numbers and addresses#card #data #leak
— Group-IB (@GroupIB_GIB) February 7, 2020
JavaScript Sniffers Proliferate
JavaScript sniffing code, aka JS sniffers or virtual skimming code, is an increasingly popular attack technique being used by crime groups to surreptitiously inject rogue JavaScript code onto e-commerce sites to intercept payment card and customer data, in what are often known as Magecart attacks (see: Police Bust 3 Suspected Magecart Hackers in Indonesia).
Last year, Group-IB reported that it had counted 38 JS-sniffer families. But last month, the firm said that figure has nearly doubled.
Magecart isn't a stand-alone crime group, but rather an umbrella term that refers to the use of these types of tools, which appear to have been traded or disseminated among crime gangs since 2014 (see: Magecart Group Continues Targeting E-Commerce Sites).
Since 2018, the number of Magecart groups has surged, with at least 12 groups now at work, according to researchers. Victims of Magecart-associated groups have included shoe manufacturer Fila, bedding sites Mypillow.com and Amerisleep.com, as well as British Airways, Ticketmaster and Newegg (see: RiskIQ: Magecart Group Targeting Unsecured AWS S3 Buckets).





















