Business Email Compromise (BEC) , Cybercrime , Email Threat Protection
Internet-Enabled Crime: 2020 US Losses Exceed $4.2 Billion
$1.8 Billion Stolen via Business Email Compromise Scams, FBI Reports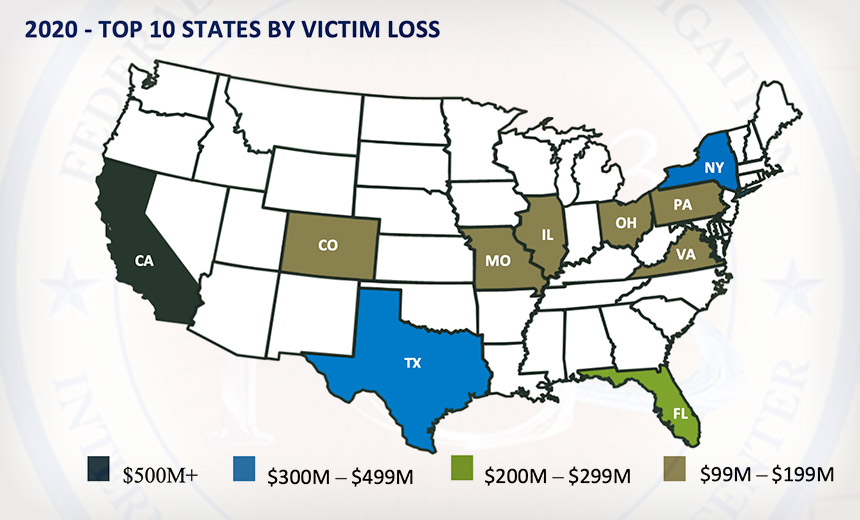
Online crime has surged during the pandemic, with more than $4.2 billion in losses reported by victims to U.S. authorities in 2020.
See Also: Disrupting the Secure Email Gateway: What is the Future of Email Security & Protection?
So says the FBI in its latest annual Internet Crime Report, noting that its Internet Crime Complaint Center, or IC3, received nearly 792,000 victim reports of suspected internet-facilitated crime last year. That record-setting number was a 69% increase from the 300,000 complaints it logged in 2019.
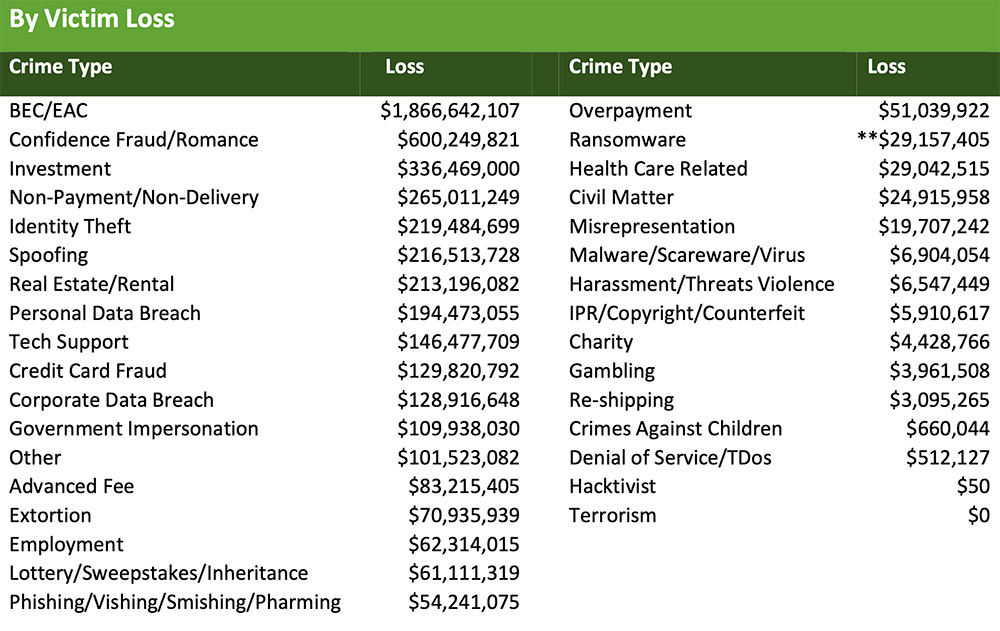
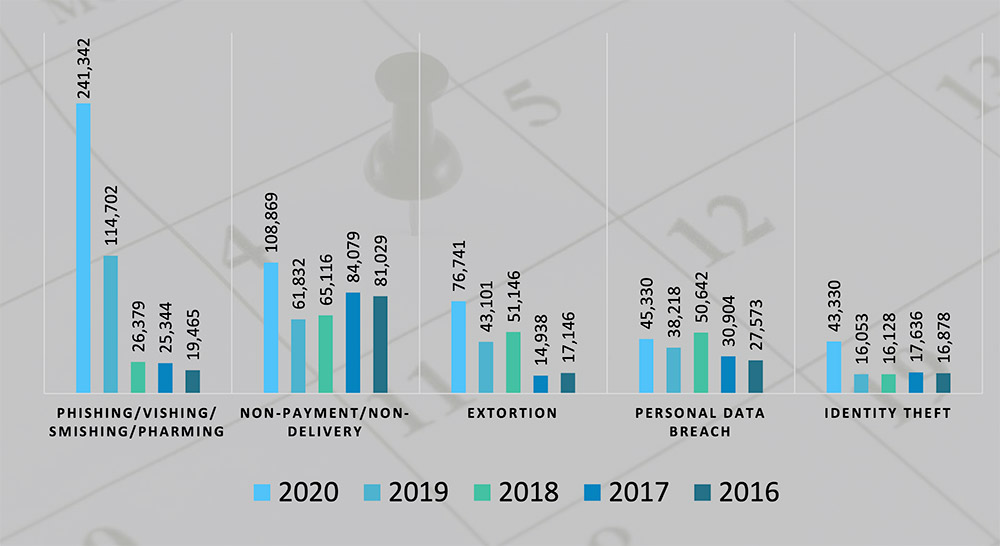
"The top three crimes reported by victims in 2020 were phishing scams, non-payment or non-delivery scams and extortion," the FBI says. "Victims lost the most money to business email compromise scams, romance and confidence schemes, and investment fraud."
In 2020, reported total losses due to business email compromise scams reached $1.8 billion, with an average loss of $92,932, up from $1.7 billion in reported BEC losses - and an average loss of $72,000 - in 2019, the FBI reports. Phishing scams led to more than $54 million in 2020 losses.
As the COVID-19 pandemic continued, IC3 reports that last year it received more than 28,500 complaints pertaining to COVID-19 fraud. Many of them involved fraudsters attempting to make fake claims under the Coronavirus Aid, Relief, and Economic Security - aka CARES - Act, which was designed to help small businesses. But via a combination of tactics, including using phishing attacks to steal personally identifiable information, some organizations discovered when applied for funds that someone else had already done so fraudulently in their name.
Meanwhile, tech-support fraud - posing as a customer-support representative for banks, utility companies, e-commerce giants and cryptocurrency exchanges - continued to be lucrative, accounting for more than $146 million in losses last year, an increase of 171% from 2019.
"Although pandemic lockdowns caused a brief slowdown to this fraud activity, victims still reported increases in incidents and losses to tech-support fraud," the FBI says, noting that in 2020 it received 15,421 such complaints from victims across 60 countries.
$29 Million in Reported Ransom Payments
Criminals also continue to wield extortion, especially in the form of ransomware attacks, in which they demand a ransom in exchange for the promise of a decryption tool or a promise not to leak or sell stolen data.
In 2020, IC3 received a total of 2,474 ransomware complaints, with total reported losses exceeding $29 million.
That latter statistic, however, carries a big caveat: "This number does not include estimates of lost business, time, wages, files or equipment, or any third-party remediation services acquired by a victim," the FBI notes - meaning that actual losses tied to ransomware were much greater.
"In some cases, victims do not report any loss amount to the FBI, thereby creating an artificially low overall ransomware loss rate," the agency notes. "The number only represents what victims report to the FBI via the IC3 and does not account for victims' direct reporting to FBI field offices or agents."
Officials continue to urge victims to never pay ransoms, although in most cases, doing so is not illegal. "Paying a ransom may embolden adversaries to target additional organizations, encourage other criminal actors to engage in the distribution of ransomware, and /or fund illicit activities," the FBI notes. "Paying the ransom also does not guarantee that a victim’s files will be recovered."
Law enforcement agencies also continue to urge victims to come forward and report attempted - or successful - crime, including ransomware incidents, even when they do pay a ransom.
As the pandemic led to a rise in coronavirus-themed crime, governments urged victims to help them blunt the surge by immediately reporting such attempts. And the same goes for ransomware attacks, the FBI says.
Immediate Reporting Can Block Fraud
"Public reporting is central to the mission and success of IC3. Submitting a cybercrime complaint to IC3.gov not only helps the FBI address specific complaints - and provide support and assistance to victims - but also helps us prevent additional crimes by finding and holding criminal actors accountable," says FBI Deputy Director Paul Abbate. "Information reported to the IC3 helps the FBI better understand the motives of cybercriminals, the evolving threat posed, and tactics utilized, enabling us to most effectively work with partners to mitigate the damage to victims."
For example, IC3 launched its Recovery Asset Team - or RAT - in February 2018 to work with banks and help recover funds transferred by U.S. fraud victims to domestic banks.
Last year, the FBI reports that the RAT team helped with 1,303 incidents and was able to help recover 82% of funds stolen in those cases. Funds frozen last year totaled $380 million out of $463 million in reported losses.
The FBI recommends that any organization that suspects it has fallen victim to a BEC attack "contact the originating financial institution as soon as fraud is recognized to request a recall or reversal and a 'Hold Harmless Letter' or 'Letter of Indemnity.'" It says they also should "file a detailed complaint at www.ic3.gov," and notes that "it is vital the complaint contain all required data in provided fields, including banking information."
Success Stories: Recovery Asset Team
The FBI says it has been able to recover some money stolen in internet-enabled fraud schemes even after it has been moved abroad or converted to cryptocurrency.
In June 2020, the agency says, a victim company located in St. Louis filed an IC3 report noting that it had wired $60 million to fraudsters who controlled a Hong Kong bank account. While the report came too late for the "international financial fraud kill chain" to be employed, the FBI says its Hong Kong legal attache worked with local police to successfully block the wire transfer from being added to the recipient's account, resulting in the full return of the missing funds.
Also in June 2020 - several months into the pandemic - the FBI says a Chicago business specializing in hand sanitizer production, believing it was investing in ventilators, sent a fraudster nearly $1 million via two wire transfers. The firm reported the suspected scam to the FBI, which says it was able to reverse the second wire transfer via the domestic financial fraud kill chain.
But the earlier payment had already been wired to a cryptocurrency exchange at another bank, and the funds had been converted to bitcoins. "Collaboration with the bank, which housed the cryptocurrency account, and with the cryptocurrency account-holder company resulted in tracing the wallet path of the funds upon being converted into bitcoin," the FBI says.
While it doesn't appear that those funds have yet been recovered, previous cases have shown that investigators often identify suspects months or years later as more intelligence and evidence come to light.
Top Target: Older Victims
One final trend highlighted in the latest FBI Internet Crime Report is the rise in fraudsters targeting individuals 60 years of age and older. While not all crime reports include a victim's age, fraudsters do appear to especially target older individuals. "Victims over the age of 60 are targeted by perpetrators because they are believed to have significant financial resources," the FBI says.
Top scams encountered by older victims include:
- Advance fee schemes, which involve securing advance payment for goods or services that never arrive;
- Investment fraud schemes;
- Romance scams;
- Tech-support scams, with 84% of all known 2020 losses - more than $116 million - tracing to individuals age 60 and over;
- Grandparent scams, in which fraudsters pretend to be a relative of the victim who's in distress;
- Government impersonation scams;
- Sweepstakes/charity/lottery scams;
- Home repair scams;
- TV/radio scams;
- Family/caregiver scams, which may lure victims into applying for fake jobs and being tricked into handling stolen goods or rerouting stolen funds.
"If the perpetrators are successful after initial contact, they will often continue to victimize these individuals," the FBI says.