Is Gov't IT Secure? FISMA Report Can't Tell
Analysis: Weighing the Value of the 11-Year-Old FISMA
The latest report to Congress on the implementation of the Federal Information Security Management Act of 2002 runs 68 pages, but even after reading the entire report, don't be surprised if you can't tell if government IT systems are secure.
See Also: Continuous Monitoring for Government Agencies
"If you analyze the questions that are used to develop agency responses, you can quickly discern that many have absolutely nothing to do with true cybersecurity or speak to true risk profiles of the agencies that respond," says the chief information security officer of a cabinet department.
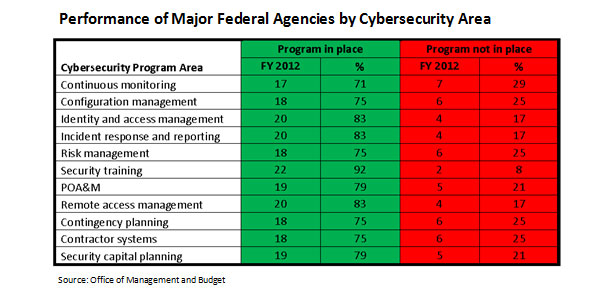
The fiscal year 2012 annual report to Congress from the White House Office of Management and Budget, issued this month, gives mixed grades on how federal agencies complied with FISMA regulations. For instance, the report suggests that agencies did a better job in complying with the Trusted Internet Connection initiative, but not as well in assessing their respective IT systems' configurations through continuous monitoring.
Compliance Doesn't Equal Security
The Trusted Internet Connection initiative, known as TIC, has reduced the number of federal government connections to the Internet [see What's Happening with the Trusted Internet Connection?]. Fewer connections make it easier to monitor traffic for malware and other anomalies. TIC traffic consolidation increased to 81 percent in fiscal year 2012, up from 65 percent in 2011. More agencies, therefore, are complying with TIC, and presumably that means networks are more secure. But compliance with TIC doesn't prove that the networks are secure.
Similarly, OMB reports significant progress in agencies that continuously monitor for vulnerabilities. Yet, OMB reports a substantial decline in configuration of continuous monitoring. That's due, in part, by the Department of Defense changing the way it measures configuration management compliance, resulting in a 42 percentage point drop in compliance for DoD last year, pulling the overall government score down. "Improved configuration management and the development of secure configuration baselines allow for the operating system to be hardened, making it more difficult for attackers to exploit any vulnerabilities," the OMB report states. But is the overall government less safe? The report doesn't - or can't - say.
"FISMA is largely a counting exercise and does not reflect the most important elements of an information security program," says Robert Bigman, who retired last year after serving 15 years as chief information security officer at the CIA. "It is easy to count, for example, the percentages of networks with intrusion detection, but it is more important to measure if the agency has a multi-layered intrusion detection/prevention strategy."
The following table, Major Federal Agencies' Compliance Scores, shows the scores major federal agencies received for complying with FISMA processes, but those scores don't reflect how secure each of these agencies' IT systems are.
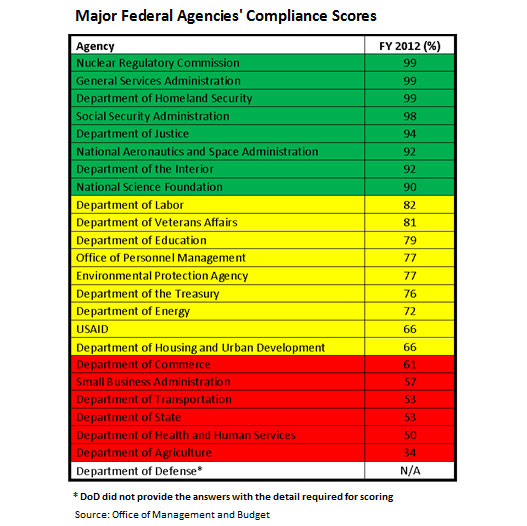
"Many of the agencies at the upper bands of yellow and in the green have serious and well-known cyber-hygiene issues and data-center weaknesses that have led to significant cyber compromises," says the departmental CISO, who asked not to be identified because of the sensitivity of the topic within the administration. "Green gets you a pass at the PMC (President's Management Council), but it doesn't get you to a real cyber program."
(The President's Management Council is a forum where the deputy secretaries, the No. 2 executives from major federal departments, can help drive implementation of strategic cybersecurity goals. The Department of Homeland Security has assumed many of the cybersecurity oversight responsibilities for civilian agencies from OMB.)
"Some agencies not in the top dismiss DHS's approach as a meaningless time-sink that distracts resource-challenged cyber teams from the real problems," the departmental CISO says. "So these agencies' FISMA results are of questionable integrity. Still, some of those agencies in the lower yellow or even red bands have very capable cyberdefense programs, focused on real-world, operational cyber threats."
Combining Facts with Subjective Judgments
Mischel Kwon, the onetime director of the United States Computer Emergency Readiness Team, sees another weakness of FISMA in its inability to accurately state the security of government systems. "Statistics are interpretations and some of FISMA is based on facts, like scanning, [while] other parts of FISMA are more subjective." Kwon says. "Also, the metrics used for incidents are still based on an older taxonomy that doesn't match up with current cyberattacks; this makes the responses difficult."
It's not just the metrics, but how the report uses audits conducted by each agency's inspectors general to assess compliance. "The IG's role in the FISMA process varies so greatly from agency to agency, and the process itself is so different," Kwon says. "It would be very hard to get any kind of consistent accurate results out of this process in terms of reporting."
FISMA wasn't designed to determine, for instance, whether the controls it measures could help agencies defend against advanced persistent threats. "FISMA has done nothing to prepare agencies to counter these attacks or deal with them once the attacks are successful; and they are almost always successful," laments the departmental CISO. "Nowhere in DHS's or the IG's questions am I asked about my agency's ability to perform malware reverse engineering, network surveillance down to the bit level or sophisticated malware eradication. These are the things we should be focused on if we are to ever stand a chance in today's world."
FISMA as a Catalyst
Still, this CISO sees some value in FISMA: "For many agencies, FISMA still serves as a forcing function to at least do the bare minimum."
That's a point shared by former Interior CIO Hord Tipton, executive director of the IT security certification concern (ISC)2: "People won't pay attention to what is not measured. Government for a long time has been catastrophe-based. The FISMA report always gave me the opportunity to point out my issues and obtain funding where needed."
Kwon sees FISMA as a management tool that can help a very large organization manage its security controls, policies and processes if used properly. "It has its place - and if used properly with the right automated tools it's not a bad methodology," she says. "The report is a report."
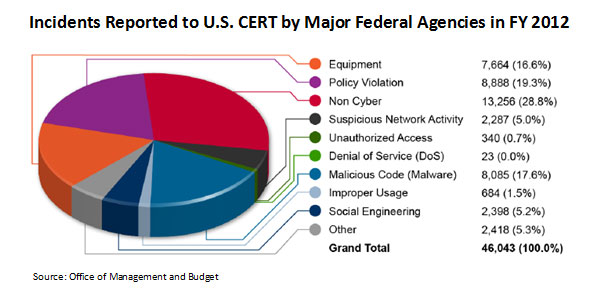
And, as a report, the annual submission to Congress provides a snapshot of some elements of how the government approaches cybersecurity. For instance, it shows the number and type of cyber-instances reported in fiscal year 2012 to U.S. CERT from major federal agencies, up about 5 percent from 2011.
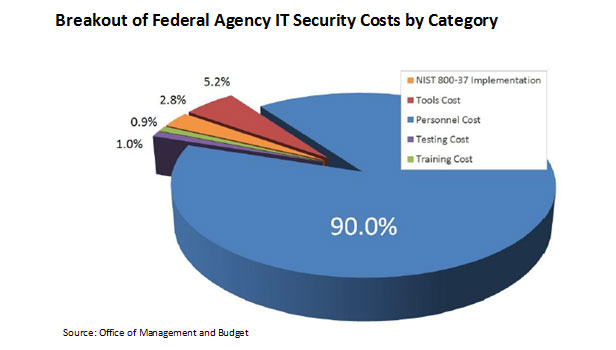
OMB's report to Congress also discloses how agencies allot their IT security budgets, which for major federal agencies reached $14.6 billion in 2012 ...
... as well as provides a breakdown of IT security personnel working in the federal government between employees and contractors.
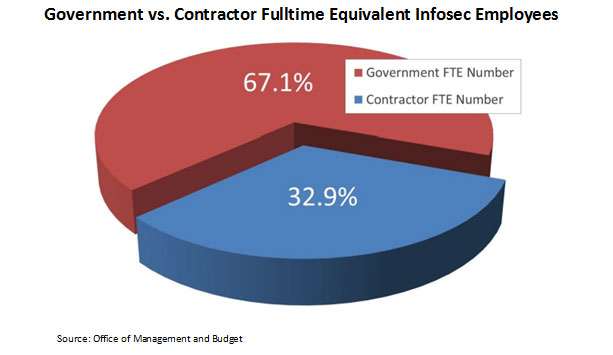
Reform: Years in the Making
For years, official Washington has had a stated goal to upgrade FISMA to focus less on compliance and more on determining in near- or real-time the security of federal government information systems. Four years ago, Sen. Tom Carper, the Delaware Democrat who this year took over the leadership of the Senate Homeland Security and Governmental Affairs Committee, introduced legislation to reform FISMA [see FISMA Reform Outlined].
White House Cybersecurity Coordinator Michael Daniel says the administration is exploring existing legal authorities to move toward continuous diagnostics of government IT systems and away from the compliance checklist approach [see Daniel Sees Path to New Infosec Law]. "Ultimately," he says, "we'd like to see legislation in this space to update FISMA to reflect this new framework that we're moving toward so that the statute is more in line with what the best practices are," he says.
Earlier this month, the leaders of the House Oversight and Government Reform Committee introduced legislation to reform FISMA that would de-emphasize compliance and emphasize continuous monitoring of IT systems for cyberthreats and implement regular threat assessments [see FISMA Reform Bill Introduced in House]. "This update to FISMA will incorporate the last decade of technological innovation, while also addressing FISMA shortcomings realized over the past years," Committee Chairman Darrell Issa, R-Calif., says. On March 20, the committee unanimously approved the bill, sending it to the full House for consideration [see 7 Duties for CISOs under FISMA Reform].
Delaying Reform Seen as Costly
But in nearly a half decade of trying - despite bipartisan support - reforming FISMA has been a hard nut to crack. The basic thrust of FISMA reform isn't controversial, but side issues - such as the role DHS should play in governing IT security among federal civilian agencies - has stymied earlier attempts to change the law. And such delays are costing the federal government - and by extension, American taxpayers - from getting value from FISMA.
There is a growing consensus that as long as FISMA reporting continues to emphasize compliance at the expense of reducing real risks, we will continue to spend scarce cybersecurity resources on measures that do nothing to enhance our cybersafety," says Franklin Reeder, a former OMB executive and founding chairman of the Center for Internet Security, the not for profit that operates the Multi-State Information Sharing and Analysis Center.
The hang-up in getting FISMA reform passed has been side issues, such as the role DHS should play in overseeing federal civilian agency cybersecurity, and not the processes themselves. Square away those differences, and FISMA reform will happen. If not, OMB will continue to issue annual reports to Congress that won't tell the true nature of federal government IT security.






















