Governance & Risk Management , Incident & Breach Response , Managed Detection & Response (MDR)
GAO: Building Systems Pose Cyber Risks
Report Says DHS Has Failed to Develop a Strategy
The Department of Homeland Security has failed to develop a strategy to secure computers in federal facilities that monitor and control building operations, such as electrical power and heating and air conditioning, opening a potential door to security breaches, according to a just-released audit by the Government Accountability Office.
See Also: Deception-Based Threat Detection: Shifting Power to the Defenders
"By not developing a strategy document for assessing cyber-risk to facility and security systems, DHS and, in particular, NPPD (its National Protection and Programs Directorate) have not effectively articulated a vision for organizing and prioritizing efforts to address the cyber-risk facing federal facilities that DHS is responsible for protecting," the GAO says. "Building and access control systems are vulnerable to cyber-attacks," the auditors write, adding that "control systems were not designed with cybersecurity in mind."
The GAO defines building and access control systems as computers that monitor and control building operations, such as elevators; electrical power; and heating, ventilation and air conditioning. They're increasingly connected to other information systems and the Internet, the GAO notes, heightening their vulnerability to cyber-attacks, which could compromise digital and physical security.
Strategy as a Starting Point
GAO says DHS lacks a strategy that defines the problem, identifies the roles and responsibilities of individuals and DHS entities, analyzes the resources needed and recognizes a processes to assess cyber-risk. "A strategy is a starting point in addressing this risk," the report says. "The absence of a strategy that clearly defines the roles and responsibilities of key components within DHS has contributed to a lack of action within the department."
For instance, GAO says, no one within DHS assesses cyber-risk to building and access control systems at the nearly 9,000 federal facilities served by the Federal Protective Service as of this past October. NPPD official told GAO that DHS hasn't developed a strategy, in part, because cyberthreats involving these systems are an emerging issue. The Federal Protective Service is the NPPD unit that provides police services to federal facilities owned or leased by the General Services Administration.
Some Types of Building and Access Control Systems in a Federal Facility
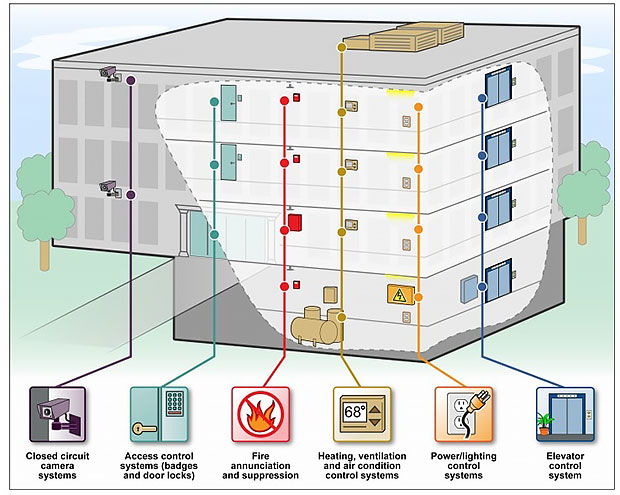
SOURCE: GAO
GAO also took DHS to task for not having its Interagency Security Committee, or ISC, incorporate cyberthreats to building and access control systems in its design-basis threat report that identifies numerous undesirable events. The ISC is responsible for developing physical security standards for nonmilitary federal facilities.
An ISC official told GAO that recent workplace-violence incidents have caused the committee to focus its efforts on policies to help prevent those types of incidents first, rather than securing building and access control systems from cyberthreats. GAO, nonetheless, says incorporating the cyberthreat to building and access control systems in the design-basis threat report will inform agencies about this threat so they can begin to assess its risk. Auditors say this action also could prevent federal agencies from expending limited resources on processes that could result in duplication.
GAO also was critical of the General Services Administration for failing to assess the cyber-attack risk to building control systems in a manner that's consistent with the Federal Information Security Management Act, the law that governs federal government IT security, or its own implementation guidelines. The report points out that GSA has assessed the security controls of these systems, but the assessments fail to assess fully the elements of risk, such as threat, vulnerability and consequence.
Example of Connectivity of Heating, Ventilation & A/C System via Internet
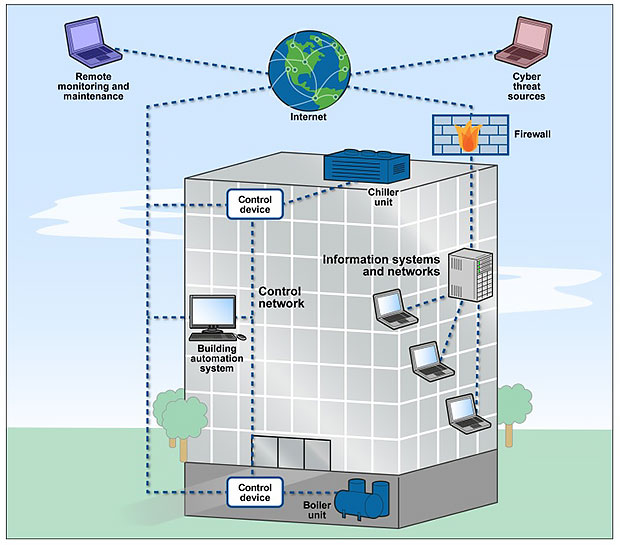
SOURCE: GAO
Auditors say GSA also has yet to conduct security control assessments for many of its building control systems.
GSA information technology officials says the agency has conducted security assessments of the building control systems found in some 500 of Federal Protection Service-protected facilities and plans to complete assessments of the remainder by the end of September or when systems are connected to the network or the Internet.
But GAO's review of 20 of 110 the security assessment reports that GSA prepared from 2010 to 2014 showed that they were neither comprehensive nor fully consistent with FISMA implementation guidelines. GAO cites reports thatshowed that GSA assessed a building control device to determine if a user's identity and password were required for login but did not assess the system to determine if password complexity rules were enforced. "This could potentially lead to weak or insecure passwords being used to secure building control systems," the auditors write.
Agencies Concur
GAO recommends that DHS develop and implement a strategy to address cyber-risk to building and access control systems and direct the Interagency Security Committee to revise its design-basis threat report to include cyberthreats to building and access control systems. GAO also recommends that GSA fully assess the cyber-risks to its building control systems fully reflect FISMA requirements and guidelines.
GSA and DHS concurred with GAO's recommendations. "Since protecting federal facilities is a government-wide responsibility, NPPD will work through the ISC to ensure that GSA, federal departments and agencies, and other partners proactively identify and mitigate cybersecurity risks to federal buildings and access control systems," says Jim Crumpacker, director of DHS's GAO-OIG liaison office.
















