Endpoint Security , Fraud Management & Cybercrime , Healthcare
Feds Warn Healthcare Entities of 'Evernote' Phishing Scheme
Scam Uses 'Secure Message' Theme and Trojan to Harvest Credentials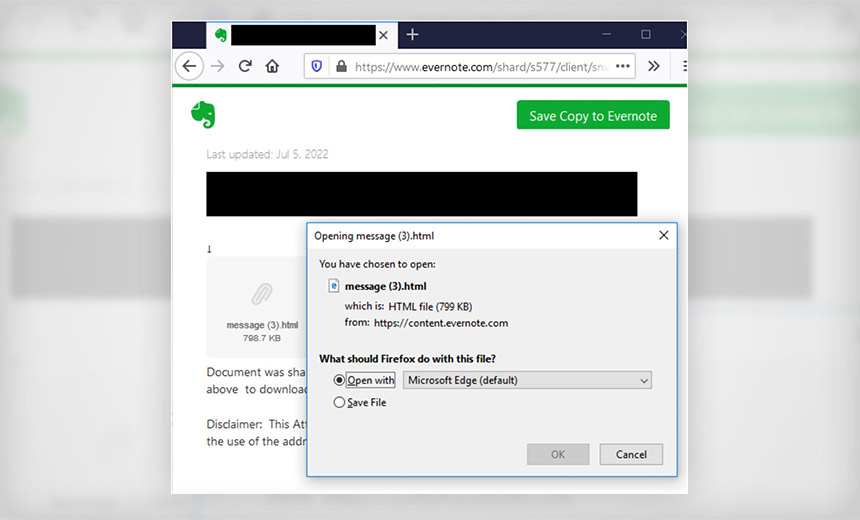
A phishing campaign targeting healthcare providers aims to lure recipients to a fake Evernote notepad website in an attempt by hackers to harvest security credentials, federal authorities warn.
See Also: OnDemand | Making the Connection Between Cybersecurity and Patient Care
The campaign tells victims they've received a "secure message" and asks them to click on a link. Falling for the phishing scheme puts healthcare sector entities at risk for an array of potential data security compromises, warns the Department of Health and Human Services' Health Sector Cybersecurity Coordination Center in an alert issued Wednesday.
The link leads to a website that looks like Evernote, the note-taking and to-do list management app. The site contains a downloadable file containing a Trojan. Once installed it, the malware will do what "it was designed for - damaging, disrupting, stealing, or inflicting harm on your data or network," HC3 warns. To make the phishing email look legitimate, phishers may use a legitimate but compromised email address from a third party.
It's an Evernote World
The population of healthcare providers using Evernote that could become potential victims is large.
"I’ve been surprised throughout the years by the large number of healthcare organizations that use Evernote. It is quite popular and has been used for sharing files, healthcare notes, scheduling, meeting notes and more," says Rebecca Herold, CEO of consulting firm Privacy & Security Brainiacs.
"Healthcare workers like to sync the data throughout all their devices they use. That seems to be the primary reason it is used in covered entities and their business associates - ease of sharing data and accessing it from generally anywhere they need to," she says.
Herold says there are potentially many risks that already may have led to incidents involving the Evernote-themed phishing campaign that went undetected.
"The fact that the Evernote app can reside on healthcare workers' phones and other devices, along with other malicious apps that could be accessing the associated Evernote data, makes it very risky to use Evernote in healthcare settings where PHI and also other entity data and access to systems is provided," she says.
"Once the threat actors gain a foothold in the environment, it is easier to cause disruption and extort the organization for financial gain."
Evernote did not immediately respond to Information Security Media Group's request for comment.
Herold says that additional security controls on Evernote are warranted, including strong encryption of Evernote data and strong firewalls on the device.

She also suggests taking administrative actions to ensure Evernote is used offline to better protect the use of the application by clinicians.
The downside is that taking the application offline "would then eliminate most or all of the data sharing throughout devices that users love."
Taking Action
The HHS HC3 alert includes a detailed list of indicators of compromise involving the phishing campaign.
Healthcare sector entities should consider a number of actions to help protect against compromises involving the campaign, the advisory says. That includes:
- Updating operating systems and software applications;
- Protecting email accounts with complex, unique passwords;
- Regularly backing up files;
- Training users to avoid opening unsolicited emails - including attachments and links - from senders they do not know.
Users falling victim to phishing attacks is a leading cause of cyber incidents and is used as a primary tactic by adversarial threat actors, warns Dave Bailey, vice president of security services at privacy and security consulting firm CynergisTek.
"From a defensive and security posture perspective, the organization must be perfect in stopping the attack. It only takes one user for the adversarial actor to be successful," he says.






















