Fraud Management & Cybercrime , Ransomware
Ransomware: 'Amateur' Tactics Lead Fewer Victims to Pay
Criminals Shooting Themselves in the Foot With Faulty Decryptors, Re-Extortion
Why are so many ransomware-wielding attackers collectively shooting themselves in the foot?
See Also: The Cybersecurity Swiss Army Knife for Info Guardians: ISO/IEC 27001
Ransomware victims who opt to pay a ransom have been seeing a "decline in quality and reliability" when it comes to quickly restoring affected systems, ransomware incident response firm Coveware reports.
Blame, at least in part, a surge in groups wielding amateur tactics. Think crypto-locking malware that shreds rather than encrypts targeted files, leading to permanent data loss - unless the victim has working backups - and victims paying for decryption tools that fail to restore their files.
Also on the rise: Victims hit multiple times over a period of days or weeks by the same attacker, sometimes using different strains of malware to try and disguise their tactics, Coveware says.
"Re-extortion has historically been a forecastable tactic, used principally by small-game ransomware actors who can withhold keys from certain systems," Coveware says. "The tactic is amateur to the point that most mid-big-game hunting ransomware affiliates avoided ever using it out of fear it would damage their reputation."
But in recent months, "well-known big game actor groups" have been using the tactic, sometimes hitting the same victim multiple times and demanding a ransom worth millions of dollars with each attack, Coveware says.
Gangs' reliability gets tracked by specialists, so they can advise a victim on whether paying a ransom has a likelihood of getting them a working decryptor and their data back in an acceptable timeframe.
Reputationally, ransomware groups have wanted to be seen to do what they've promised. Otherwise, what incentive do victims have to pay a ransom for the promise of a working decryptor?
Penny-Wise But Pound-Foolish
The increase in decryptors failing to function properly is a byproduct of many ransomware-wielding attackers no longer working with ransomware-as-a-service operations, which supply crypto-locking malware as a service, typically in return for 20% or 30% of every ransom paid, Allan Liska, a principal intelligence analyst at Recorded Future, tells Information Security Media Group.
Since source code leaked from many top RaaS operations, including for heavyweights Conti, Hello Kitty and LockBit, many criminals have opted to use the source code themselves, and avoid the expense - and potential law enforcement exposure - that comes from working with a big-name RaaS operation, he says (see: Ransomware Ecosystem: Big-Name Brands Becoming a Liability).
But whereas big-name RaaS operations tend to be staffed with specialists, including expert developers, smaller players often lack the technical expertise required to troubleshoot code-level problems, such as decryptors failing to function properly, Liska says.
Ransomware Ecosystem: The Fracturing
Some ransomware groups run data leak sites, where many but not all groups list victims who haven't paid. These lists are notoriously incomplete: groups don't list all victims, paying or otherwise, and sometimes they get it wrong or even lie (see: Tracking Ransomware: Here's Everything We Still Don't Know).
In another sign of how the ransomware ecosystem has been fracturing, in 2021, ransomware groups collectively ran 44 data leak sites, while already this year there are 107 sites in total. "We expect we'll be close to 125 if not 130 by the end of the year," Liska says.
Of the groups that run data leak sites, the most victims during the third quarter - ranging from 200 to 20 - were listed by LockBit, followed by Black Basta, Hive, BlackCat and BianLian, threat-intelligence firm Kela reports. The most victims were based in the United States (40%), followed by the United Kingdom, (6%), France (6%), Germany (5%) and Spain (4%).
Industry-wise, listed victims most often hailed from professional services (17%), followed by manufacturing & industrial products (16%), and healthcare and life sciences (8%), Kela reports.
Caveat Emptor
The average ransom payment - when a victim chooses to pay - has been increasing.
From July through September, the average ransom payment was $258,143, up 13% from April through June, Coveware reports. Those findings are based on thousands of cases the firm helped investigate, many of which have not been publicly disclosed.
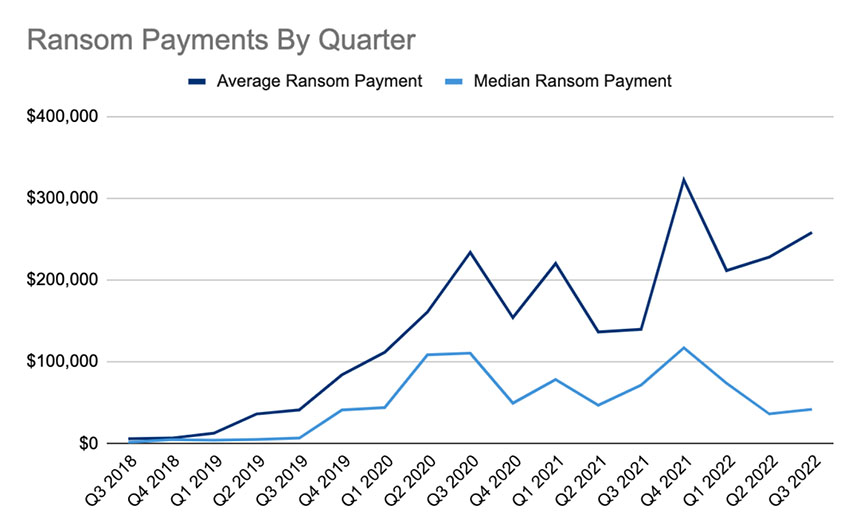
In the same timeframe, the median ransomware payment increased by 15.5% to $41,987, which Coveware says reflects ransomware-wielding attackers more often hitting midsize organizations. For large organizations, it says the most likely outcome of a ransomware attack is simply loss of data. But for the small and midsize sectors, outages are common, lasting an average of 25 days in Q3.
Which ransomware groups are most active? Answers to that question vary on investigators' perspective.
Coveware reports that in Q3 BlackCat - aka Alphv - was tied to 15% of incidents it investigated, followed by Hive (14%), Black Basta (6%), Dark Angels (4%), Phobos (4%), Vice Society (3%) and AvosLocker (3%).
Based on incidents it worked, the most-hit sectors in the third quarter were professional services (18% market share) followed by healthcare (17%) and the public sector (12%).
Attacks against healthcare have been surging, with many such attacks tracing to Hive. "Unlike some groups, Hive does not even attempt to steer clear of impacting healthcare facilities and displays a general ambivalence to the potential kinetic outcomes that their attacks may have on patient care," Coveware says.
Other groups - including BlackCat, Black Basta, and Vice Society - have also shifted to targeting healthcare. This too could be a result of many groups opting for more amateur money-making strategies at the expense of their reputation, leading to a revenue shortfall.
As Coveware says: "Their collective pivot towards this higher-profile sector could indicate more desperate economics of running a profitable ransomware brand."











