Anti-Phishing, DMARC , Email Threat Protection , Fraud Management & Cybercrime
Fancy Bear Invites DC Conference-Goers to Install Malware
Hackers Go Phishing for Cybersecurity Conference Attendees With Decoy Document
Want to target a large swath of cybersecurity professionals in one go? Just crash their "cyber" party with a decoy document.
See Also: ISO/IEC 27001: The Cybersecurity Swiss Army Knife for Info Guardians
So goes the modus operandi for an advanced persistent threat group of hackers who appear to have targeted the upcoming International Conference on Cyber Conflict - CyCon U.S. - taking place at the Ronald Reagan building in Washington from Nov. 7 to Nov. 8, researchers at Cisco's Talos security group warn.
CyCon U.S. is a collaboration between the Army Cyber Institute at the U.S. Military Academy and the NATO Cooperative Cyber Defense Centre of Excellence, based in Tallinn, Estonia, where the complementary CyCon Conference is held every spring. The IEEE Computer Society is a technical co-sponsor of both events as well.
The conference organizers bill CyCon U.S. as being "a venue for fresh ideas, relevant and actionable content, insight into future trends, and access to industry, government and military leaders, cyber innovators and pioneers in the discipline." They say it will include discussions about new cyber initiatives as well as research and cooperation into "cyber threats and opportunities" spanning technical, legal, political, military and economic arenas.
Irony Alert
The theme of this year's CyCon U.S. is "The Future of Cyber Conflict." But for at least some conference attendees, the conflict comes now, say Talos security researchers Warren Mercer, Paul Rascagneres and Vitor Ventura.
Potential conference attendees, they say, are being targeted by at least one decoy document designed to resemble a CyCon U.S. flier, but which includes malware that's been previously used by the APT group Fancy Bear, aka APT28, Group 74, Pawn Storm, Sofacy, Strontium and Tsar Team (see Microsoft Battles Fancy Bear Hackers - With Lawyers).
Cybersecurity firm CrowdStrike has said that the attack group appears to be associated with the GRU Russian military intelligence agency.
"Unlike previous campaigns from this actor, the flyer does not contain an Office exploit or a zero-day, it simply contains a malicious Visual Basic for Applications (VBA) macro," the Talos researchers say (see Hello! Can You Please Enable Macros?).
If the VBA macro executes, it drops a new variant of Seduploader reconnaissance malware, which for years has been tied to Fancy Bear attacks, and which includes both a malware dropper as well as a malicious payload, Talos says. Seduploader includes multiple features, including the ability to capture screenshots, exfiltrate data and system configuration information, execute code as well as download files onto endpoints.
"The dropper and the payload are quite similar to the previous versions but the author modified some public information such as MUTEX name, obfuscation keys," Talos says. "We assume that these modifications were performed to avoid detection based on public IOCs," referring to "indicators of compromise," which can involve virus signatures tied to previously seen strains of malware as well as server addresses and IP addresses that have been seen in previous attacks.
CyCon Pysch-Out
While that might seem to be an obvious attack to launch against potential attendees of a NATO cybersecurity conference, Talos says it's tracked endpoints that have apparently allowed the macros to execute, resulting in the decoy documents "phoning home" to attacker-controlled servers.
In this case, the sample of malware analyzed by Talos found that it phoned home to "myinvestgroup.com."
"At Cisco Talos, we go out of our way to collect as many samples of attacks as we possibly can," Martin Lee, a technical lead at Talos, tells me. "We discovered this attack within unclassified samples that were available to us."
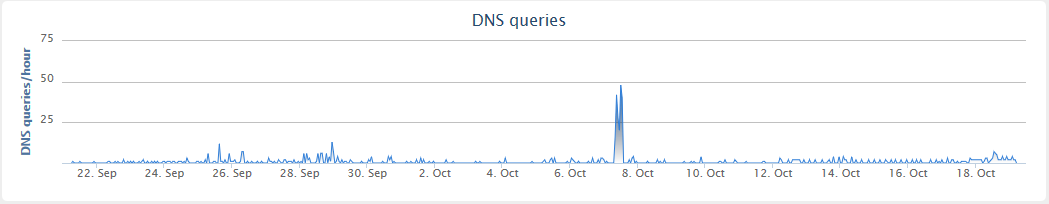
Talos says the attack file appeared to have been created on Oct. 4, and three days later, it saw a peak of endpoints infected by the new Seduploader variant attempting to phone home. "We certainly don't have DNS traffic from every infected endpoint within this data set, and equally not every DNS request to this domain is necessarily from an infected endpoint," Lee says. "Nevertheless, we can observe a clear pattern of activity showing a burst of DNS request activity on the 7th of October, which may suggest this is when the campaign was most active."
Lee says it's not clear how attackers distributed this document or what their motivations might be. "But using social engineering techniques, including invitations to conferences or documents that are particularly enticing to the recipient, are all part of the craft of the attacker," he says. "Presumably, the attackers are using these sorts of document because they know, or strongly suspect them, to be effective in eliciting a response from their intended victims."
Cisco Talos has issued IOCs for the attack, including hashes of the weaponized Office documents, Seduploader dropper and payload. The researchers recommend not just looking for those IoCs, but also blocking any attempts to access the command-and-control domain.
Cyberattacks: The Future is Now
But Fancy Bear regularly updates its attack code, the researchers warn, meaning that today's indicators of compromise may not spot tomorrow's attack. The new Seduploader payload variant includes 195 functions, of which 149 are an exact match for functions contained in the May sample, while "16 match at 90 percent [similarity] and 2 match at 80 percent," the Talos researchers say.
Attackers have good reason to keep revising their malware. "Once their campaigns have been exposed they will often try to change tooling to ensure better avoidance," the Talos researchers say. "For example, the actor changed the XOR key and the MUTEX name," referring to code constants in the malware that were seen in a version of the Seduploader uploader and payload that were recovered from an attack campaign that began in May.
"We assume that these modifications were performed in order to avoid detection based on public IOCs," Cisco says.
Oct. 23: This piece has been updated with comments from Martin Lee at Cisco Talos.











