The Decade in Vulnerabilities and Why They Persist
Despite 'Patch or Perish' Problem, Bugs Rarely Burn Out, Instead Slowly Fading Away
Here's a cybersecurity truism: Big, bad bugs never burn out. They slowly fade away - despite the risk that attackers will exploit them to steal data, seize control of systems or deploy ransomware.
See Also: ISO/IEC 27001: The Cybersecurity Swiss Army Knife for Info Guardians
Ideally, all organizations would rapidly expunge known vulnerabilities from their networks, starting with the most severe bugs that pose the greatest risk.
In reality, serious vulnerabilities never seem to die. In April, for example, the Five Eyes intelligence alliance - comprising Australia, Canada, New Zealand, the U.K. and U.S. - issued a joint alert urging organizations to patch 15 of the most exploited vulnerabilities of 2021, not least by nation-state attackers.
Of those 15 highlighted flaws, two came to light in 2020, one in 2019 and another in 2018.
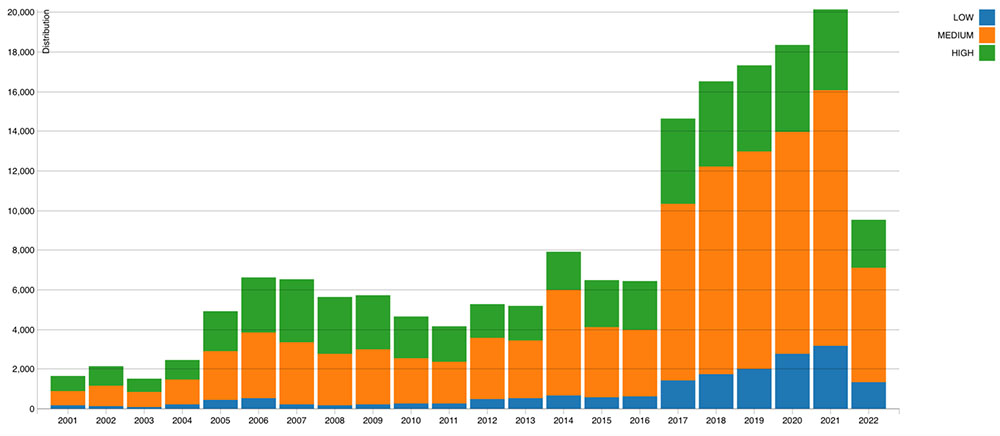
Another take on the challenge comes via a list of "the most egregious network security flaws" of the past decade - from 2011 to 2021 - compiled by the SpiderLabs research and intelligence team at Chicago-based cybersecurity firm Trustwave, which is part of Singaporean telecommunications company Singtel Group Enterprise.
Of the 10 vulnerabilities the security researchers highlight, attackers continue to actively exploit these five:
- SolarWinds backdoor: Attackers sneaked a backdoor into the SolarWinds Orion network monitoring tool used by 18,000 organizations and used it to target a subset of those organizations. This supply chain attack, later attributed to Russia's foreign intelligence service, was first detected on Dec. 8, 2020, and initially patched on Dec. 13, 2020. Nevertheless, "infected servers currently exist, and attacks still take place due to companies being unaware of dormant attack vectors" that were put in place before organizations patched, SpiderLabs says.
- Heartbleed: This flaw in older versions of OpenSSL, designated CVE-2014-0160, can be exploited to steal data, eavesdrop on communications and impersonate sites, services or users, without leaving any trace. Based on searches conducted by SpiderLabs using the Shodan internet-connected device search engine, more than 200,000 systems still remain vulnerable to Heartbleed. While that's a reduction from the 250,000 systems counted as being vulnerable in 2015, it highlights how incredibly slowly even serious vulnerabilities can fade away.
- BlueKeep: Microsoft Remote Desktop Protocol facilitates remote access to systems. But a vulnerability designated CVE-2019-0708 could be used to design wormable malware and has been widely used by cryptomining malware. Shodan searches show at least 30,000 vulnerable systems remain worldwide.
- Drupalgeddon: Vulnerabilities in the content management system, including this SQL injection flaw first discovered in 2014, as well as the Drupalgeddon 2 and 3 flaws, were used in mass attacks and continue to enable attackers to take control of websites, oftentimes to press compromised servers into service for cryptomining botnets.
- Ripple20: Widely used code for implementing networking protocols can be exploited via a set of 19 vulnerabilities first patched in March 2020. But given the flaws' wide use in internet of things devices, their impact will likely "ripple" for years.
Overall Severity of Flaws Increasing
Patching is a Sisyphean task. New flaws are always coming to light. In the case of previously unknown zero-day flaws, the vulnerabilities may already be actively exploited with no patch yet available.
The patching problem is compounded by bug severity, says Trustwave's SpiderLabs team, based on its own analysis of vulnerabilities, as well as its reading of information provided by the U.S. National Vulnerability Database, the Exploit-DB public archive of exploits and vulnerability information engine VulnIQ.
"Security incidents and individual vulnerabilities have been increasing in number and becoming more sophisticated," SpiderLabs says.
Don't Forget Log4j
Not highlighted in Trustwave's top 10 was Log4jShell, a vulnerability in the open-source logging utility Log4j maintained by Apache. Multiple flaws were found in the software and disclosed beginning in December 2021. One challenge is that Log4j is so widely used and built into other pieces of software that patching all instances seems unlikely.
One piece of good news is that relatively few Log4Shell-exploiting attacks - and none targeting critical infrastructure - have been seen so far, says the Cyber Safety Review Board, established last year by President Joe Biden to review serious cybersecurity incidents.
"The Log4j event is not over," the Cyber Safety Review Board says in a recent report on Log4j. "The board assesses that Log4j is an 'endemic vulnerability' and that vulnerable instances of Log4j will remain in systems for many years to come, perhaps a decade or longer. Significant risk remains."
Unfortunately, the same remains true of so many vulnerabilities that have been discovered or are yet to be found.











