Business Continuity Management / Disaster Recovery , Critical Infrastructure Security , Cybercrime
Belarusian Spear-Phishing Campaign Targets Ukraine Military
Hacktivist Group Breaches Belarusian Weapons Manufacturer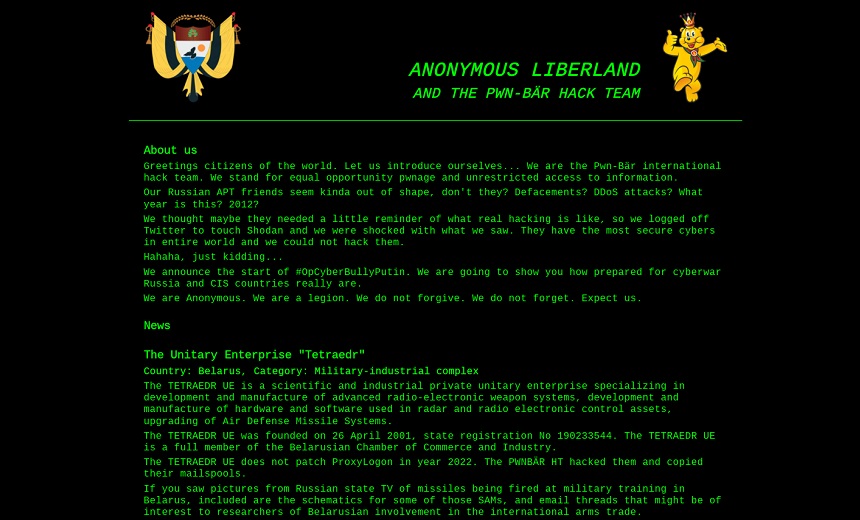
The Computer Emergency Response Team of Ukraine is warning of a massive spear-phishing campaign targeting private accounts of Ukrainian military personnel and related individuals. CERT-UA attributes the activities to the UNC1151 group, which consists of officers of the Ministry of Defense of the Republic of Belarus.
See Also: The State of Organizations' Security Posture as of Q1 2018
"Mass spear-phishing campaigns have recently been observed targeting private 'i.ua' and ‘meta.ua’ accounts of Ukrainian military personnel and related individuals. After the account is compromised, the attackers, by the IMAP protocol, get access to all the messages. Later, the attackers use contact details from the victim’s address book to send the phishing emails," Ukraine's Computer Emergency Response Team said in a statement on Facebook.
The agency released a follow-up statement that attributed the attacks to the Minsk-based group UNC1151 - aka Ghostwriter.
UNC1151 is a state-sponsored cyberespionage actor that engages in credential harvesting and malware campaigns (see: 'Ghostwriter' Disinformation Campaign Targets NATO Allies).
In a statement provided to ISMG, the security firm Mandiant confirmed that "the domains mentioned in the CERT.UA Facebook post are attributable to UNC1151."
Mandiant director Ben Read said the activity matches the historical pattern of efforts targeting the Ukrainian military over the past two years (see: Destructive Malware Discovered Targeting Ukrainian Systems).
"UNC1151 is in play," tweeted John Hultquist, vice president of intelligence analysis at Mandiant. "Watch out for hack and leak, fake documents and content, and information planted on real media sites. Maybe something designed to degrade support for the Ukrainian military or suggest fissures with and within the NATO alliance."
UNC1151 is in play. Watch out for hack and leak, fake documents and content, and information planted on real media sites. Maybe something designed to degrade support for the Ukrainian military or suggest fissures with and within the NATO alliance.https://t.co/7oAnTYspbx
— John Hultquist (@JohnHultquist) February 25, 2022
Exposing Weapon Trader
Hacktivist Collective 'Anonymous' and Pwn-Bär international hack team claimed that they have successfully breached Belarusian weapons manufacturer Tetraedr after declaring cyberwar against Russia and its allies. The group of hacktivists also exposed more than 200GB of emails from the manufacturer.
Some more groups are now active - #anonymous #liberland and #pwnbar hack team.
— CyberKnow (@Cyberknow20) February 26, 2022
Have leaked military data from #belarus #cybersecurity #infosec #threatintel #Ukraine #RussiaUkraineWar pic.twitter.com/WeTKnZ2svz
The group says it stands for unrestricted access to information and announced the start of #OpCyberBullyPutin, while mocking Russia and CIS countries for their lack of preparedness for cyberwar.
"The Tetraedr is a scientific and industrial private unitary enterprise specializing in development and manufacture of advanced radio-electronic weapon systems, development and manufacture of hardware and software used in radar and radio electronic control assets, upgrading of Air Defense Missile Systems," the group says.
The group of hacktivists says that the weapon manufacturer Tetraedr did not patch ProxyLogon in 2022, making Pwn-Bär team able to hack them and copy their mailspools.
Meanwhile, the Ukrainian Ministry of Defense has reportedly issued a call for Ukrainian hackers to safeguard its networks and potentially tap into Russian infrastructure (see: Ukraine Reportedly Calls for Volunteer Cyberwarriors).
According to Reuters, the country is looking to its underground to field a team of digital volunteers to serve as a line of Ukrainian defense, including spying on Russian troops. Sign-up requests reportedly began circulating on Thursday.
"Ukrainian cybercommunity! It's time to get involved in the cyber defense of our country," says the report. It reportedly urges hackers to submit applications through Google docs - and to highlight any background in malware development.
The report says teams would be split between "defensive - guarding critical infrastructure, and "offensive," including supporting the Ukrainian military in digital espionage. Reuters writes that organizers have already received hundreds of applications that they are now vetting - particularly for potential Russian agents.
The post was reportedly authored by Yegor Aushev, co-founder of the cybersecurity company Cyber Unit Technologies, which has contracted with the Ukrainian government. Aushev reportedly said the request came from the country's Defense Ministry, although the ministry did not confirm the move in initial media reports.




















