Apple iOS Exploit Makes Apps Vulnerable
Replaces Authentic Apps with Malicious Versions
Security firm FireEye is warning Apple users about a flaw in which downloaded malicious apps can replace genuine iOS apps, an exploit the security firm is dubbing the "Masque Attack."
See Also: Email's Need For The Security Advantages of Cloud Infrastructure
Using the "Masque Attack," an attacker can replace authentic apps, such as banking and e-mail applications, using malware through the Internet, FireEye says.
"That means the attacker can steal users' banking credentials by replacing an authentic banking app with malware that has [an] identical [user interface]," the company says. The exploit affects all versions of iOS from 7.1.1 onward for both jail-broken and non-jail broken devices, according to FireEye.
The security firm has shared a proof of concept video of the exploit in action. The company notified Apple about the vulnerability July 26.
How Serious?
Robert Graham, CEO of research firm Errata Security, says exploiting the bug requires bypassing the Apple Store. "If all your apps come from Apple's store, it doesn't apply to you," he says.
The issue arises through enterprises' mobile device management systems that manage the applications on a user's iPhone or iPad, Graham says. "It's these systems that are under threat. Thus, if you are a security manager at one of these companies, you need to pay attention to this problem quickly."
The "Masque Attack" exploits a system Apple developed to allow large organizations to deploy custom-built software without going through the App Store, David Richardson, iOS product manager at mobile security firm Lookout, tells Reuters.
The threat is serious, says Aditya Gupta, security researcher and co-founder of mobile security firm Attify Inc. "A critical point here is that the malicious app has access to all the stored data of the application it replaces," he says.
Gupta says that attackers stand to gain the most by targeting banking apps. If the legitimate banking app downloaded from the iOS App Store gets replaced, it could send a user's banking credentials back to the attacker without the user ever noticing anything is wrong, because the app has the exact same look and feel as the original app.
Because the exploit gives an attacker access to the authentic app's data, banking apps storing information, including bank account details and passwords, are all available to the attacker with no extra effort, Gupta says.
Security Impact
In a "Masque Attack," an attacker lures a victim, using malicious text messages, e-mails or Web links, to install an application using a deceiving name crafted by the attacker, such as "New Angry Bird." Once the application is installed, the iOS system will use it to replace a legitimate app.
A "Masque Attack," however, can't replace Apple's platform applications, such as Mobile Safari, but it can replace applications installed from the App Store. As a result of an attack, FireEye says, cybercriminals can:
- Mimic the original app's login interface to steal the victim's login credentials;
- Steal sensitive data stored in the original app's directory;
- Bypass the application's normal sandbox and then get root privileges by attacking known iOS vulnerabilities.
Security firm Norton says iOS users can protect themselves from the Masque Attack by not installing applications from third-party sources; avoiding clicking "Install" on a pop-up from a third-party Web page; and uninstalling an application immediately if, when opened, an alert that says "Untrusted App Developer" appears.
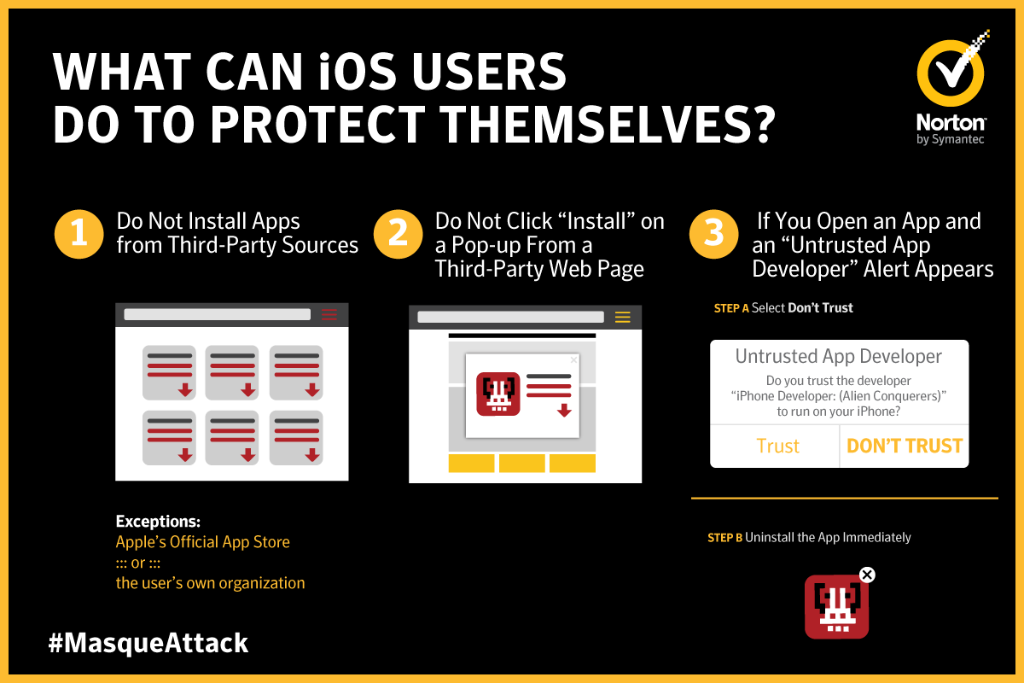
Source: Norton
Apple did not immediately respond to a request to comment on the exploit.
WireLurker
The news of the "Masque Attack" comes just one week after Palo Alto Networks revealed new malware known as WireLurker, which spreads via a third-party Chinese app store and can infect even non-jailbroken iPhones (see: Malware Infects Apple iOS Devices).
Tao Wei, senior staff research scientist at FireEye, says the company decided to go public with its findings after Palo Alto Networks revealed WireLurker, the first campaign to exploit the "Masque Attack" vulnerability, according to Reuters. "Currently WireLurker is the only one, but we will see more," Wei says in the news report.
The WireLurker malware has been hidden in "Trojanized" versions of applications that appear to function normally, but which also include malicious capabilities, including the ability to steal iOS users' data.
Since first appearing in April, "WireLurker was used to Trojanize 467 OS X applications on the Maiyadi App Store, a third-party Mac application store in China," Palo Alto Networks information security researcher Claud Xiao says in a blog post. "In the past six months, these 467 infected applications were downloaded over 356,104 times and may have impacted hundreds of thousands of users."
WireLurker first infects an Apple OS X computer, then watches for any USB-connected devices, Palo Alto says. "WireLurker monitors any iOS device connected via USB [to] an infected OS X computer and installs downloaded third-party applications or automatically generated malicious applications onto the device, regardless of whether it is jailbroken," Xiao says. "This is the reason we call it 'Wirelurker.'"
Once the malware infects an iOS device, it can infect other apps stored on the device, and it regularly "phones home" to attackers' command-and-control server to request updates, Palo Alto Networks says. To date, however, attackers don't appear to have used it for a major campaign.






















