Data Loss Prevention (DLP) , Endpoint Security , Open XDR
How to Anticipate Breaches & Prevent Data Loss: Avoiding the Fate of OPM
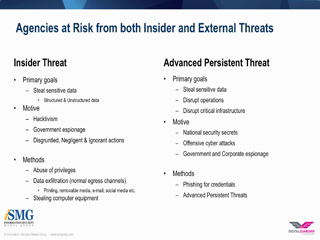
In light of what is being called one of the largest breaches in U.S. government history at the Office of Personnel Management, every agency needs to be asking if their investments in data security are being managed appropriately. In absence of an appropriate risk-based approach, agencies can invest significant resources in data protection without effectively minimizing risk.
See Also: 5 Best Practices for CISOs Adopting XDR: Cybersecurity Beyond the Endpoint
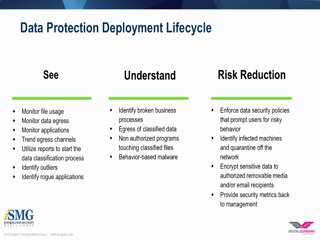
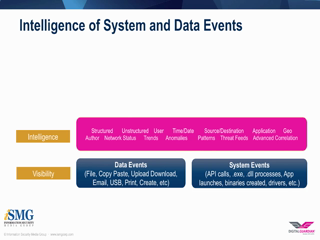
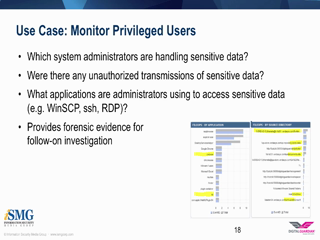
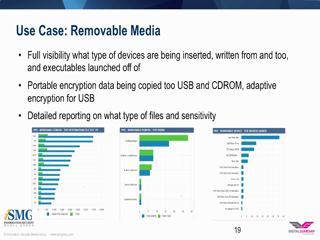
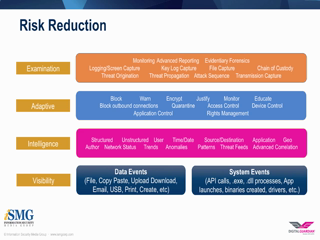
The first step in any data protection strategy is gaining visibility into your organization's sensitive data and how it's being used. However, visibility alone won't reduce your risk profile unless you recognize and understand the actions against that sensitive data. This approach to threat protection is the basis of the 3 R's of Data Protection - Reviewing & Understanding Visibility, Recognizing Risk, and Reducing Risk which provides the best defense against advanced threats.
In this webinar, Chris King from Digital Guardian will discuss:
- How to integrate the three R's of Data Protection in order to reduce the risk of data loss;
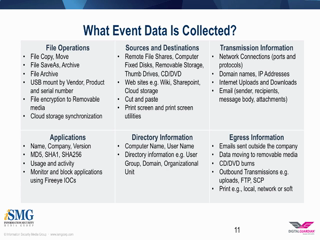
- Understanding the Enterprise Audit and building more effective security policies;
- Effective integration with other platforms to maximize data protection.